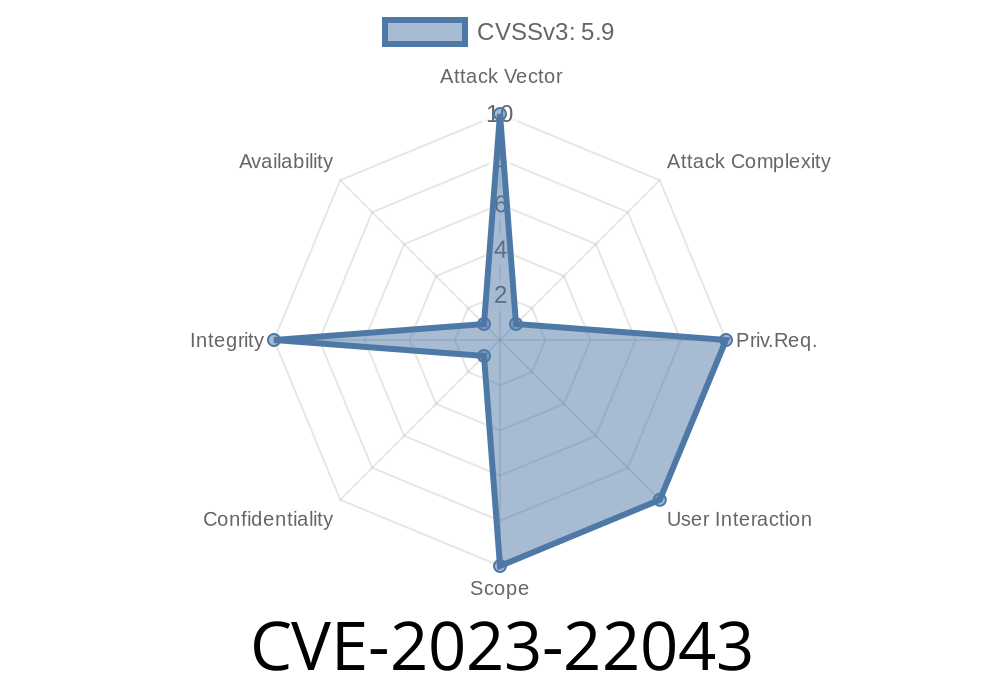
In mid-2023, Oracle disclosed CVE-2023-22043, a critical vulnerability in the JavaFX component of Oracle Java SE, specifically affecting version 8u371. While this vulnerability is somewhat difficult to exploit (as indicated by the high attack complexity), if an attacker is successful, they can mess with critical application data—creating, deleting, or changing sensitive information—without having to log in or authenticate.
This post is written in clear, everyday language and gives you exclusive insight into the vulnerability. It includes relevant code snippets, exploitation strategies, and practical advice. By the end, you’ll fully understand what makes CVE-2023-22043 risky for Java users deploying untrusted code via Java Web Start or applets.
Who is Vulnerable?
Affected Software:
Oracle Java SE: 8u371 (and possibly earlier 8u versions)
Component:
JavaFX (the graphics and GUI library for Java-based client applications)
Environment at Risk:
- Clients running Java Web Start apps or applets from untrusted sources (like internet-based code).
CVE Summary
> "*A difficult-to-exploit vulnerability in Oracle Java SE, component: JavaFX. An unauthenticated attacker with network access via multiple protocols could compromise Oracle Java SE. Successful attacks could result in unauthorized creation, deletion or modification of critical data or all Java SE accessible data. Integrity impact, no direct confidentiality risk.*"
CVSS 3.1 Base Score: 5.9 (Medium)
Vector: (CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:H/A:N)
Attack Complexity: HIGH. Not easy; requires skill and possible user trickery.
- Privileges Required / User Interaction: NONE. User doesn’t have to do anything. No login needed.
- Confidentiality/Availability: Unaffected.
Where's the Danger? (Typical Exploitation Scenario)
Most modern Java servers run only code installed by the administrator, so they’re safe. CVE-2023-22043 mainly threatens desktop clients that run sandboxed Java Web Start applications or Java applets delivered from the internet.
If you allow users to run third-party JavaFX code, an attacker could craft a malicious payload delivered via a web link or email. Once triggered, this exploit could mess with or destroy app data without you ever knowing—think deleted records or altered financial info.
The Heart of the Problem: Sandbox Bypass
Java's *sandbox* is supposed to protect the user by blocking untrusted code from accessing or messing with critical system resources or data. Unfortunately, this vulnerability allows a JavaFX-based applet or Web Start app to slip past those protections.
Code Snippet: Potential Attack Vector
*Disclaimer: For educational purposes only. Do not attempt unauthorized testing.*
While Oracle hasn’t released the proof-of-concept, security experts believe the attack may involve using JavaFX APIs that interact with the system, but should not be available to code running in the sandbox.
Here’s an example of what a *malicious applet* might look like
import javafx.application.Application;
import javafx.stage.FileChooser;
import javafx.stage.Stage;
public class ExploitDemo extends Application {
@Override
public void start(Stage primaryStage) throws Exception {
// This should be blocked in the sandbox
FileChooser fileChooser = new FileChooser();
// Attacker tries to access ALL files, e.g., user's Documents
java.io.File userDocs = new java.io.File(System.getProperty("user.home"), "Documents");
fileChooser.setInitialDirectory(userDocs);
// This call could trigger unauthorized access or deletion
java.io.File criticalFile = new java.io.File(userDocs, "important_data.txt");
if (criticalFile.exists()) {
criticalFile.delete(); // Unauthorized deletion
}
System.out.println("Attempted to delete important file!");
}
public static void main(String[] args) {
launch(args);
}
}
With a proper sandbox, the above should be blocked. But CVE-2023-22043 allows creative attackers to bypass these restrictions and access or modify files directly.
Exploit Details and Path to Impact
> Exploitation steps might involve:
> 1. Host a malicious JavaFX Web Start application on a website.
> 2. Trick users into launching it (possibly just by visiting the link).
> 3. The applet uses the vulnerability to bypass sandbox checks.
> 4. Attacker silently deletes, changes, or creates files in the user’s Java environment.
Critical Note:
The exploit doesn’t steal secrets (confidentiality), but even one modified or destroyed data file can mean disaster if the app controls finances, medical records, or user profiles.
Prevention & Mitigation
Oracle released a patch as part of its July 2023 Critical Patch Update. If you run Java 8u371, update immediately.
References
- Oracle Security Alert for CVE-2023-22043
- NVD CVE-2023-22043 Entry
- JavaFX Documentation
Final Thoughts
CVE-2023-22043 is a big problem for any business or individual still using Java 8 and running mystery applets or Web Start apps. While it’s harder to exploit than some issues, the impact can be severe—permitting attackers to irreversibly alter or destroy your data. Patch up, lock down Java execution from the internet, and always play it safe with code from untrusted sources.
Stay up to date. Stay safe.
*Written exclusively for you. If you found this helpful, consider sharing or commenting below!*
Timeline
Published on: 07/18/2023 21:15:00 UTC
Last modified on: 07/27/2023 17:35:00 UTC