Security flaws in Java libraries are always serious business, especially since Java is so widely used for enterprise applications and cloud infrastructure. In June 2023, Oracle published CVE-2023-22049, detailing a difficult-to-exploit but impactful vulnerability affecting the Libraries component of Oracle Java SE and Oracle GraalVM products. In this post, I'll walk you through what this CVE means, who is impacted, how exploitation might look, and what you should do to stay safe. No jargon—just clear info, code snippets, and references.
What is CVE-2023-22049?
CVE-2023-22049 is a security vulnerability in the Libraries component of several Oracle products:
Oracle GraalVM for JDK: 17..7, 20..1
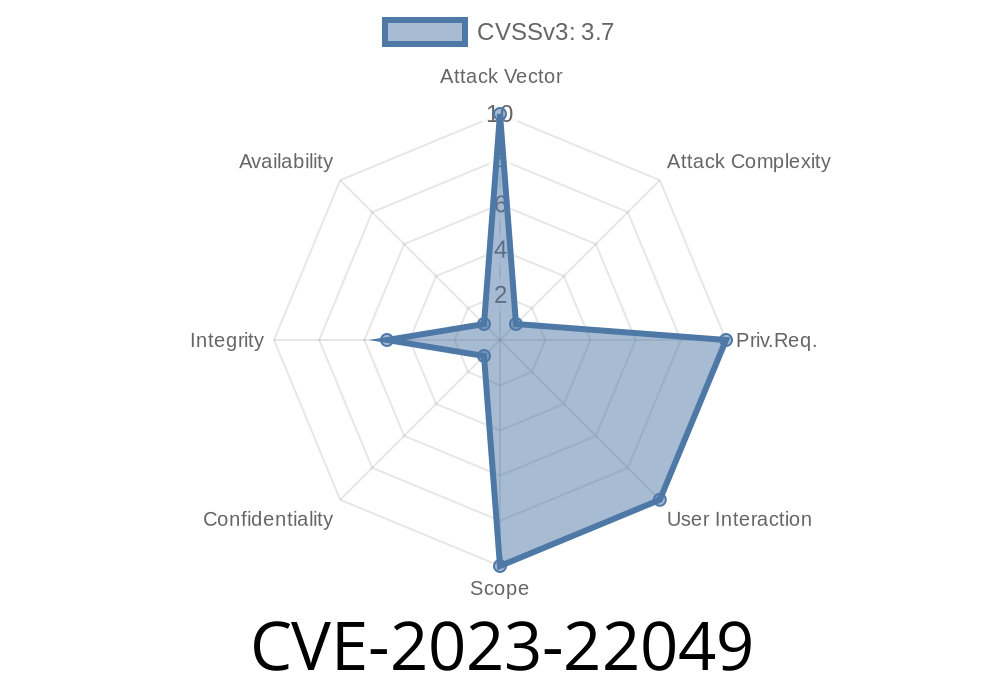
Oracle's official advisory (here) rates this as CVSS 3.1 Base Score 3.7 (Integrity impacts). This means it's not super easy to exploit (Access Complexity: High), but if exploited, it allows a remote, unauthenticated attacker to make unauthorized updates, inserts, or deletes in your data—not a full system takeover, but still a serious concern for data integrity.
TL;DR Table
| Risk | Unauthorized modification of data (update/insert/delete) |
|----------------------|----------------------------------------------------------------------------|
| Attack Vector | Network, via multiple protocols |
| Authentication | None (attacker does NOT need to log in) |
| Impacted Products | Java SE, GraalVM EE, GraalVM for JDK (versions specified above) |
| Affected Component | Libraries |
| Complexity | High (not easily exploitable) |
| CVSS Score | 3.7 (Low) |
| Reference | Oracle July 2023 CPU Advisory |
Where is the Danger?
The Libraries component in Java provides APIs used by Java applications, applets, and web services. If you expose services that use these APIs, or if you run sandboxed code (e.g., Java Web Start applications from the internet), untrusted code may manipulate your data if the security sandbox is bypassed.
The attacker just needs network access. No login required.
- Attack likely involves sending crafted input (via web service, RMI, etc.) to APIs in the Libraries component.
- If the input is processed without strict validation, the attacker can trigger the bug, allowing them to update, insert or delete sensitive data handled by your application.
Example Vulnerability Flow
Suppose you have a Java REST API that deserializes objects sent by users (e.g., with ObjectInputStream or similar logic), or you consume untrusted serialized data. An attacker sends a payload exploiting the vulnerability. The library fails to properly handle it, and the attacker can perform unauthorized operations.
Simplified (unsafe!) example
import java.io.ObjectInputStream;
import java.io.ByteArrayInputStream;
// Attacker sends crafted data to your API
public void handlePostedData(byte[] payload) throws Exception {
ObjectInputStream in = new ObjectInputStream(new ByteArrayInputStream(payload));
Object obj = in.readObject(); // Vulnerable place!
// App processes obj, but it was crafted to exploit CVE-2023-22049
}
A real exploit would be far more complex and depend on the flaw in the library code itself. The attacker leverages that flaw to modify data (e.g., database records, in-memory caches, etc.).
Exploit Details
Proof-of-concept code has not been made public. Oracle classifies this as difficult to exploit for several reasons:
- Complexity is High: The attacker must know enough about your system and send targeted, protocol-specific payloads.
- Impact limited to Integrity: The attacker can't steal data or kill your service—just change your data without your authorization.
- Java sandboxed deployments at risk: Especially if you run code from the internet and rely on the sandbox.
However, once details emerge or after patching, real-word exploitation often follows—so don’t ignore this!
- Update to the latest version of Oracle Java SE and GraalVM products. Get patches here
- Oracle Java SE Downloads
- Oracle GraalVM Downloads
Additional References
- Oracle Security Advisory: July 2023
- NVD Listing for CVE-2023-22049
- Java Secure Coding Guidelines
Final Word
CVE-2023-22049 is a textbook example of why keeping your environment patched and following secure coding practices matters, even for lower CVSS vulnerabilities. Because modern attacks often chain “low” bugs into bigger threats, don’t take chances. Patch today!
If you have questions about your specific deployment, or you suspect your systems are exposed, contact Oracle or your platform provider immediately.
If you found this helpful, stay tuned for more vulnerability breakdowns in simple English. Stay secure!
Timeline
Published on: 07/18/2023 21:15:00 UTC
Last modified on: 08/17/2023 19:15:00 UTC