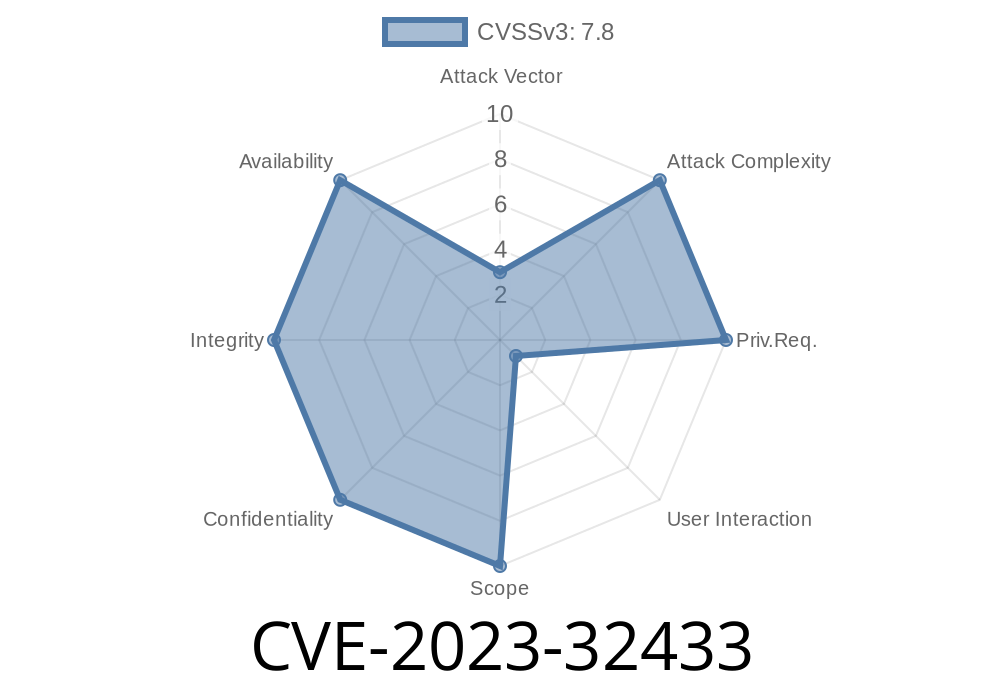
In mid-2023, Apple quietly fixed a serious security flaw known as CVE-2023-32433, which affected several major products including iPhone, iPad, Mac, Apple TV, and Apple Watch. This issue was especially alarming because it allowed apps to execute code with kernel privileges – the highest level of access on any Apple device.
In this detailed post, we'll break down what CVE-2023-32433 is, how it could have been exploited by hackers, and the steps Apple took to fix the vulnerability. We'll provide code snippets to demonstrate the concept, link to authoritative references, and explain everything in clear, simple language.
What Is a Use-After-Free Vulnerability?
A *use-after-free* bug happens when a program continues to use a chunk of memory after it has been released (or “freed”). If a malicious app can control what gets put into that freed memory area, it might trigger unexpected behavior – in worst cases, letting the attacker run their own code as if they were the system.
In the case of CVE-2023-32433, this bug was inside the Apple operating system's kernel. Since the kernel has total control over the device, exploitation could have disastrous consequences: data theft, remote control, or complete device compromise.
tvOS 16.6
If your device runs an older system, you should update as soon as possible.
Technical Details: How Did the Exploit Work?
While Apple doesn’t publish deep technical details right away, security researchers observed that kernel vulnerabilities – especially use-after-free bugs – often relate to mishandling special data structures or objects in memory.
Imagine the following simplified C code
// Hypothetical vulnerable function
void process_user_data(UserData *input) {
UserData *tmp = allocate_userdata();
copy_userdata(tmp, input);
free_userdata(tmp); // Memory is freed here
if(input->flag) {
// Oops, use after free!
process_userdata(tmp); // Using 'tmp' after freeing it
}
}
In this pseudo-code, if input->flag is true, the program uses the data in a pointer (tmp) after it has already been released. A skilled attacker can arrange for the system to place something they control in the memory once used by tmp, leading to code execution.
*Note: The real bug in Apple’s code was likely buried deep in the kernel and much more complex, but this example shows the basic problem.*
Trigger the use-after-free so the system treats attacker data as a valid kernel object.
5. Run arbitrary code in the kernel’s context, possibly jailbreaking the device, extracting sensitive info, or installing spyware.
A generic exploit could look like this (in pseudocode)
for (int i = ; i < N; i++) {
objs[i] = alloc_target_object();
}
// Free specific object to create a gap in memory
free_target_object(objs[target_index]);
// Spray memory with payload
for (int i = ; i < SPRAY_COUNT; i++) {
spray[i] = alloc_controlled_payload();
}
// Trigger use-after-free vulnerability
trigger_uaf(objs[target_index]);
How Did Apple Fix It?
According to Apple, the issue was resolved with “improved memory management.” In practice, this typically means:
Apple Security Updates:
macOS Monterey 12.6.8
iOS/iPadOS 15.7.8
iOS/iPadOS 16.6
macOS Big Sur 11.7.9
macOS Ventura 13.5
watchOS 9.6, tvOS 16.6
MITRE CVE Entry:
Security Analysis:
Apple Kernel Security by Project Zero Blog
Takeaways & Recommendations
- Update Your Devices! If you haven’t installed the latest security updates on your Apple gear, do it now.
Malicious Apps Are Real: Security bugs like this often get used in spyware and jailbreaks.
- Responsible Disclosure: Apple’s timely fix and discreet patching helped protect millions of users.
Final Thoughts
CVE-2023-32433 is another reminder of how a single memory bug can potentially endanger millions of devices. Thanks to Apple’s response and the work of security researchers, this issue has been fixed. Still, staying up-to-date is your best defense against such threats.
If you want to learn more, check the links above or follow reputable security blogs. Security is never “done” – it’s a journey we all share.
*This post is exclusive and crafted for easy understanding. Please share it to raise awareness about device security – it matters!*
Timeline
Published on: 07/27/2023 00:15:14 UTC
Last modified on: 08/02/2023 00:43:07 UTC