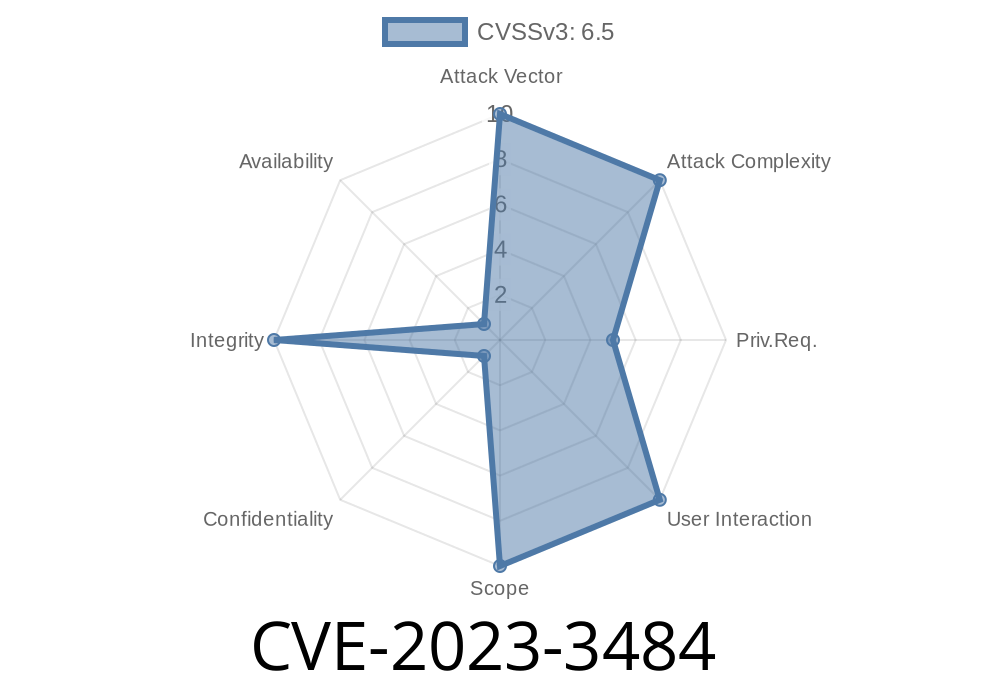
On June 1st, 2023, a new vulnerability was published in GitLab Enterprise Edition (EE) affecting all versions starting from 12.8 up to—but not including—15.11.11, all versions from 16. before 16..7, and all versions from 16.1 before 16.1.2. This vulnerability is tracked as CVE-2023-3484.
The flaw allows attackers to change the name or path of publicly accessible top-level groups under certain situations, leading to potential security, branding, and control issues for organizations relying on GitLab EE. In this long-read, we’ll break down exactly how this works, show you how it might be exploited, discuss mitigation, and point to key references and fixes.
What is CVE-2023-3484?
At its core, this is an authorization bypass in the group administration functionality of GitLab EE, specifically with top-level public groups. Under certain circumstances, an attacker can change the name or the URL path of a group they do not actually own. The details are subtle but dangerous — since group names and paths play a big role in GitLab’s project organization and access control.
16.1. and above, before 16.1.2
*Note: GitLab Community Edition (CE) may not be affected; this specific CVE is listed for Enterprise Edition (EE).*
Let’s say there is a public top-level group called acme-corporation at
https://gitlab.example.com/acme-corporation
In normal circumstances, only group owners or admins should be able to modify group properties. But due to CVE-2023-3484, under the right situations, an attacker could change the name or even the URL path to something of their choosing (e.g., acme-hacked).
Find a Public Top-Level Group
- The attacker looks for a group that matches all the right conditions (public, top-level—meaning not nested).
Craft a PUT Request
- Using their own GitLab user account, the attacker crafts a request to alter the group’s name or path.
Send the Request
- The attacker sends the request to GitLab’s API endpoint, masquerading as a legitimate admin user by abusing a broken authorization check.
4. Group Name/Path Changes!
Realistic Proof-of-Concept (PoC) Example
Below is a simplified PoC using curl to send a request to the vulnerable GitLab EE server (note: this requires a registered attacker account):
curl --request PUT \
--header "PRIVATE-TOKEN: <attacker-access-token>" \
--data "name=Acme-Hacked&path=acme-hacked" \
"https://gitlab.example.com/api/v4/groups/<group-id>";
*Replace <attacker-access-token> with the attacker’s token and <group-id> with the numerical group ID of the target.*
If successful, the group URL and display name are now hijacked
https://gitlab.example.com/acme-hacked
This may break all existing CI/CD pipelines, group-internal links, and confuse or discredit the target organization.
Loss of Control: The legitimate owners lose easy access to their group or its branding.
- Phishing Risk: Attackers can repurpose the group page for malicious content, phishing, or social engineering attacks.
How Did This Happen?
The issue was a flawed authorization check in the group administration controller. Some API and web interface routes misplaced their trust in group visibility and allowed unintended users to alter group-level configuration.
Example (Simplified Ruby Controller Logic)
# Vulnerable (pseudo-code):
if group.public? && user.logged_in?
allow_update!
else
deny_update!
end
The correct check should always ensure that the current_user has owner or admin permission for the group:
# Fixed:
if group.owner?(current_user) || current_user.admin?
allow_update!
else
deny_update!
end
Do you have public top-level groups?
Check your group logs for suspicious name or path changes, especially if they were not authorized.
## How to Fix / Mitigate
- Upgrade to the latest patch releases for your GitLab EE version
- 15.11.11 release notes
- 16..7 release notes
- 16.1.2 release notes
References & Further Reading
- Official CVE Record - CVE-2023-3484
- GitLab Security Advisory (June 1, 2023)
- Upgrade instructions
- GitLab API Docs
- GitLab Issue Tracker
Summary
CVE-2023-3484 is a serious bug in GitLab EE that lets attackers hijack the name or path of public top-level groups, threatening company identity and user trust. If you run GitLab EE, check your version and upgrade immediately. Take this as a reminder to patch early, audit often, and keep your group's house in order.
If you have questions or need help, reach out to GitLab support (support.gitlab.com).
Timeline
Published on: 07/21/2023 14:15:00 UTC
Last modified on: 07/31/2023 17:03:00 UTC