Microsoft’s ODBC Driver for SQL Server is a critical component used by applications to access SQL Server databases on Windows systems. In September 2023, a serious security flaw—CVE-2023-36785—was disclosed by Microsoft. This can allow remote attackers to execute arbitrary code on targeted machines. In this post, we’ll break down the vulnerability in simple terms, show how exploits might work, and provide resources to help you protect your systems.
What is CVE-2023-36785?
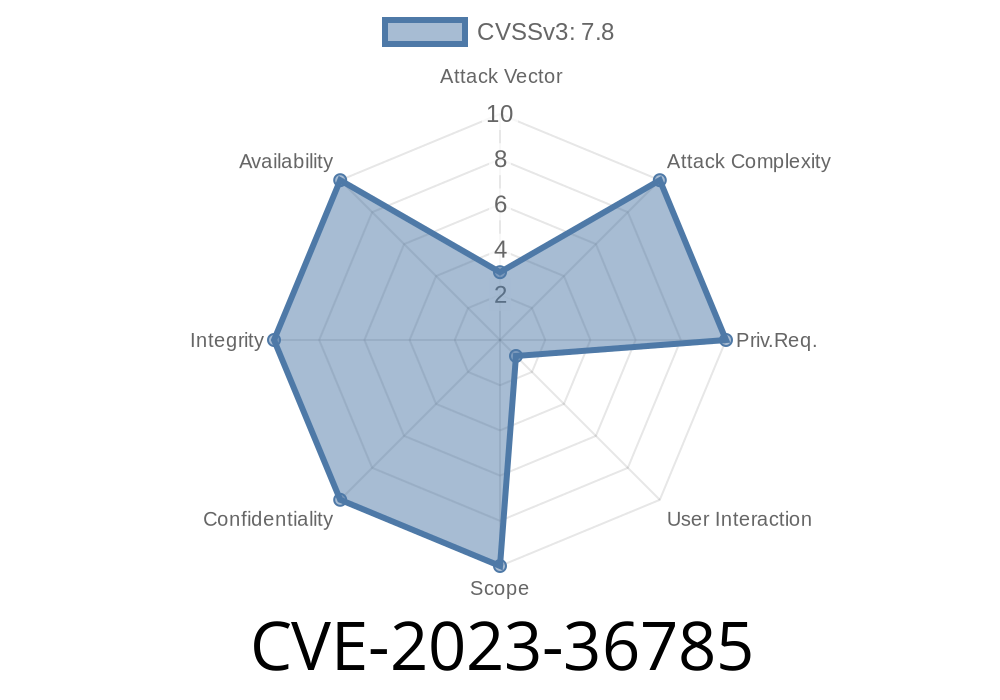
CVE-2023-36785 is a Remote Code Execution (RCE) vulnerability affecting the Microsoft ODBC Driver for SQL Server. If an attacker successfully exploits this vulnerability, they can run any code on the victim’s system. This could let hackers install programs, view and change data, or create new user accounts with full admin privileges.
The vulnerability sits in how the ODBC Driver processes certain inputs, making it possible to trick it into executing malicious code—especially if an app uses inputs from untrusted sources.
Who is Affected?
If your environment uses Microsoft ODBC Driver for SQL Server in any way (for example, web servers, applications, scripts, or client tools), and you have not applied Microsoft’s security updates from September 2023 or later, you’re at risk.
Microsoft ODBC Driver 18 for SQL Server (version prior to 18.3.2.1)
Reference:
- Microsoft Security Update Guide: CVE-2023-36785
- NVD - CVE-2023-36785 Details
How Does The Exploit Work?
This is an input handling bug. Attackers who can convince an application (using a vulnerable ODBC Driver) to process malicious connection strings, database queries, or configuration files, might trick the system into loading and running a code payload.
Imagine a common scenario:
- A web application accepts user input and passes it directly to the database using the ODBC Driver, without proper sanitization or validation.
Example Exploit (Proof of Concept)
While Microsoft hasn’t published in-depth technical details at the time of writing, the common attack vector involves connection strings. If the ODBC driver processes a maliciously crafted connection string, it could trigger the bug.
Below is a simplified proof of concept based on similar vulnerabilities. Note: Never test this outside of a lab environment you control!
Example vulnerable Python code using pyodbc
import pyodbc
# This should be sanitized!
user_input = input("Enter your database connection string: ")
# Dangerous: Using raw user input for connection string
conn = pyodbc.connect(user_input)
cursor = conn.cursor()
cursor.execute("SELECT @@version")
print(cursor.fetchone())
A crafty attacker might provide a connection string like this (payload is hypothetical)
DRIVER={ODBC Driver 17 for SQL Server};SERVER=myserver;UID=sa;PWD=12345;Extended Properties="malicious_code"
If the Extended Properties input is mishandled and reaches the vulnerable code path, the attacker’s code could execute.
Real-World Attack Scenarios
- Compromising Web Applications: Web or cloud services taking in user-supplied database config data.
- Abusing Configuration Files: If attackers can alter config files consumed by ODBC-enabled apps, they can trigger the flaw at startup.
Upgrade to the latest ODBC Driver for SQL Server
- ODBC 17 Download
- ODBC 18 Download
2. Never Trust User Input
Always sanitize and validate anything that ends up in a database connection string, query, or configuration.
3. Restrict Permissions
Run database-connected apps with the least permissions necessary.
4. Monitor for Exploitation
Look for unusual connection failures, new user logins, or strange system behavior.
5. Use Strong Authentication
Avoid using administrative accounts in connection strings.
Links and References
- Microsoft Security Update Guide: CVE-2023-36785
- NIST National Vulnerability Database – CVE-2023-36785
- Microsoft ODBC Driver for SQL Server Documentation
- ODBC 17 Download Page
- ODBC 18 Download Page
In Summary
CVE-2023-36785 is a serious, easy-to-exploit vulnerability in Microsoft’s ODBC Driver for SQL Server. Any untrusted data reaching ODBC connection strings or database configuration files puts your system at risk of remote code execution—even from a browser or indirectly through a web API.
Patch your ODBC Drivers now, and audit your code for unsafe database connection handling. The fix is available; don't wait for an attack to find you.
Timeline
Published on: 10/10/2023 18:15:17 UTC
Last modified on: 10/12/2023 22:21:49 UTC