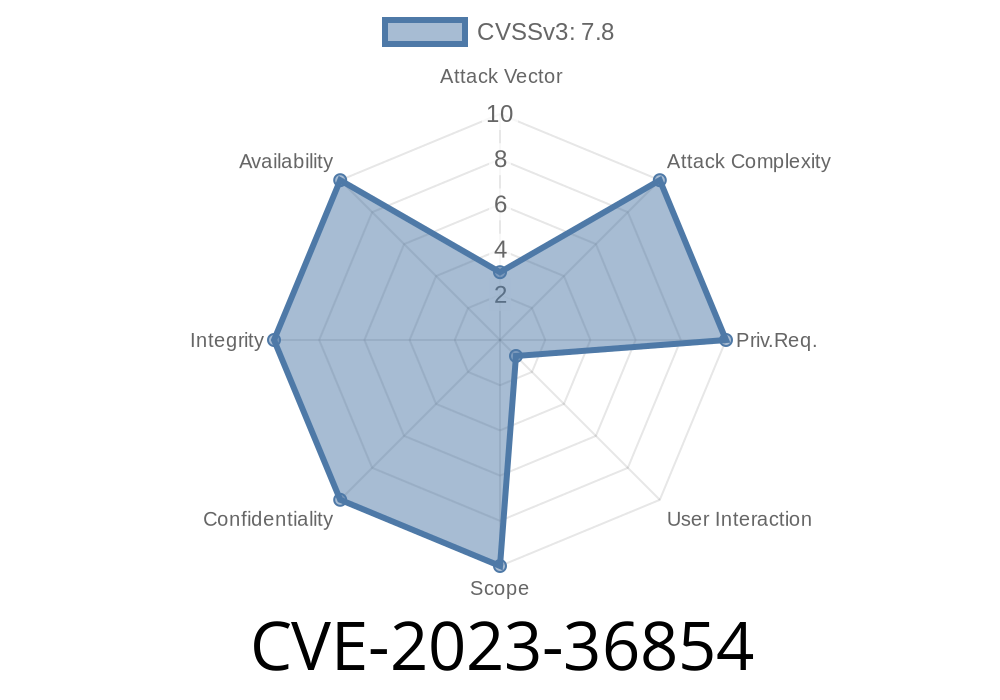
Apple’s operating systems are known for strong security, but sometimes bugs slip through the cracks. CVE-2023-36854 was one of those: a vulnerability so severe that simply opening a bad file could break your app—or even let an attacker run code on your machine.
Let’s break down what CVE-2023-36854 is, how it could be exploited, and what went into Apple’s fix.
What is CVE-2023-36854?
CVE-2023-36854 is a security issue affecting Apple’s macOS platforms: Monterey (12.), Ventura (13.), and Big Sur (11.) systems. The problem existed in how files were being processed by certain applications. If a user opened a specially crafted file, it could crash the app (unexpected termination), and in the worst case, allow someone to execute any code they wanted on your Mac—this is called “arbitrary code execution.”
macOS Big Sur 11.7.9
The root cause? Insufficient checks when parsing files. In simple language: the app didn’t properly verify or validate the contents of a file before trusting and processing it.
You open it using a vulnerable app.
4. Crash or exploit: The app may crash (denial of service), or worse, run code embedded in the malicious file. This code could install malware, steal your data, or take control of your system.
Demo: Simpler Version of the Exploit
While the exact technical details of CVE-2023-36854 (like which component or format is affected) aren’t publicly disclosed, this sort of bug often appears in file parsing code:
// Pseudo-code illustrating the kind of bug
void processFile(char *data, size_t size) {
char buffer[256];
// Not validating 'size' could lead to buffer overflow
memcpy(buffer, data, size); // dangerous!
}
In this example, if size is bigger than the buffer, you could overwrite memory. Now, an attacker crafts a file with extra data to “smash” the buffer and inject code.
Real Exploit Steps (Hypothetical)
A real-world attacker might use a file containing manipulated metadata or crafted image data, targeting the vulnerable parsing code. Here’s a theoretical exploitation flow:
Proof of Concept (PoC) in Python (hypothetical)
# This script creates a file with an oversized field to crash a vulnerable parser
malicious_content = b"A" * 1024 # Oversized payload
with open("malicious_file.bad", "wb") as f:
f.write(malicious_content)
print("Malicious file created")
If an unpatched macOS app parses this file without proper checks, it could crash or be hijacked.
How Did Apple Fix It?
Apple addressed the issue by “improved checks”—meaning they added stricter validation when processing file input. The new code would look more like this:
void processFile(char *data, size_t size) {
char buffer[256];
if (size > sizeof(buffer)) {
// Reject the file
return;
}
memcpy(buffer, data, size); // safe now!
}
This prevents overflows and stops malicious input from breaking through.
macOS Big Sur 11.7.9 or later
How to update:
Go to System Settings > General > Software Update, and apply the latest available security updates.
Apple Security Update Notes:
https://support.apple.com/en-us/HT213840
NIST NVD CVE Report:
https://nvd.nist.gov/vuln/detail/CVE-2023-36854
Final Thoughts
Though technical details for CVE-2023-36854 remain private for your protection, the lesson is simple: Always apply security updates promptly. Even opening a file on an unpatched system could spell disaster. If you’re reading this on an older Mac version, time to update!
Timeline
Published on: 07/27/2023 00:15:15 UTC
Last modified on: 08/02/2023 00:48:51 UTC