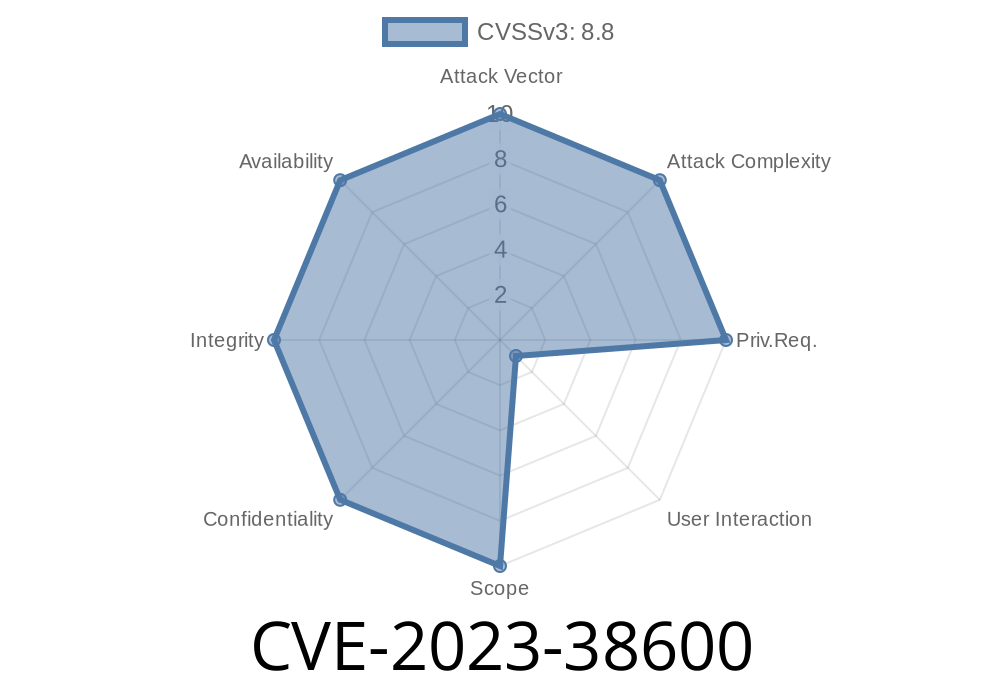
In July 2023, Apple released a critical batch of security updates across almost its entire ecosystem, including iPhones, iPads, Macs, Apple Watches, Apple TVs, and even the Safari browser. At the heart of these updates was the patch for a particularly nasty vulnerability: CVE-2023-38600, a flaw in Apple's WebKit browser engine. If left unpatched, this bug could let an attacker run malicious code on your device — just by tricking you into visiting a specially crafted website.
Let's break down what went wrong, how the exploit worked, and why you should make sure you're running the latest software.
What is CVE-2023-38600?
CVE-2023-38600 is a WebKit bug. For those who don't know, WebKit is the engine beneath Safari and all browsers on iOS and iPadOS. So, a WebKit issue means almost every browser on Apple's mobile devices is vulnerable.
In plain terms:
If you visited a malicious web page, it could cause your device to execute arbitrary code. That means hackers could take control — maybe to steal your files, spy on you, or worse.
Apple’s description was simple
> *Processing web content may lead to arbitrary code execution. The issue was addressed with improved checks.*
watchOS 9
...and had not applied the July 24–25, 2023 security updates, your devices were at risk.
See Apple’s list of patches:
- Apple security updates
The Technical Root: What Was the Flaw?
Apple didn’t publish step-by-step details immediately (to prevent attackers from weaponizing old devices), but security researchers pieced together clues based on open source WebKit commits and reported behavior.
In short:
A logic check in WebKit's handling of certain web content was missing or faulty. Crafted JavaScript or HTML could cause WebKit to mismanage memory or execute improper instructions. That gap allowed attackers to inject and run code outside the browser’s safety box.
Here’s a generic illustration of a vulnerability like CVE-2023-38600
// Example of a dangerous object mismanagement in JavaScript (simplified)
let arr = [1, 2, 3];
let victim = {}; // a target object in browser memory
// If a vulnerability exists (e.g., use-after-free or type confusion)
arr.length = 100000;
for (let i = ; i < arr.length; i++) {
arr[i] = some_payload(); // under certain bugs, this could corrupt memory!
}
// Under the hood, WebKit might mishandle memory pointers due to missing checks
// Allowing remote code execution
Actual exploits get much more complex, often involving memory spraying, ROP chains, or JIT misdirection.
Exploit runs automatically, in many cases needing no more than the user reading the web page.
5. Malicious code executes: from stealing cookies, reading messages, or in advanced scenarios, installing spyware.
Did This Vulnerability Get Exploited?
Apple stated that they had not received reports of active exploitation at the time of release. However, similar WebKit bugs have been exploited in the wild, especially by spyware vendors targeting journalists, activists, or government data.
Pwn2Own 2023 and other security contests have repeatedly shown how powerful these WebKit bugs can be:
- Pwn2Own 2023 Results
The Fix: Improved Checks
Apple patched the vulnerability by adding more thorough validation at key points in the WebKit codebase. This prevents attackers from feeding poisoned data to the engine and corrupting memory.
If you're on iOS 16.6, iPadOS 16.6, macOS Ventura 13.5, Safari 16.6, or watchOS 9.6+ — you’re protected.
You can view the official release notes here:
- iOS & iPadOS 16.6 Security Content
- macOS Ventura 13.5 Security Content
- Safari 16.6 Security Content
- watchOS 9.6 Security Content
- tvOS 16.6 Security Content
Proof-of-Concept (PoC): What Might an Exploit Look Like?
> (For educational purposes only. Do not attempt this on any live environment.)
While this is a simplified generic example, it highlights the type of JavaScript attackers use for memory corruption:
// This code DOES NOT trigger CVE-2023-38600, but similar patterns are often used.
// Spray heap with arrays
let arrs = [];
for (let i = ; i < 10000; i++) {
let arr = new Array(100).fill(x41414141);
arrs.push(arr);
}
// Attempt to trigger type confusion or out-of-bounds write
// (Real exploit would target specific vulnerable WebKit object)
someVulnerableFunction(arrs);
// Next, attacker would manipulate a controlled object
// and execute shellcode or privileged commands
Get the idea? The real exploit required deep knowledge of WebKit internals, but attacks like these are why browser vulnerabilities are so dangerous.
How to Stay Safe
- Update all your Apple devices to the latest software — check for iOS, iPadOS, macOS, tvOS, watchOS, and Safari updates!
Final Thoughts
The discovery and patch for CVE-2023-38600 show how dangerous browser bugs can be — with nothing more than a web page visit, you could be at risk. Apple responded quickly and rolled out patches to everyone, but not everyone updates promptly. Don’t be that person. Protect your devices, your data, and your family.
References & Further Reading
- Apple Release Notes (iOS 16.6)
- NIST National Vulnerability Database: CVE-2023-38600
- WebKit Security Advisories
- Pwn2Own 2023
*Want more? Follow Apple Security for the latest patches and advisories.*
Timeline
Published on: 07/27/2023 01:15:38 UTC
Last modified on: 08/18/2023 03:15:21 UTC