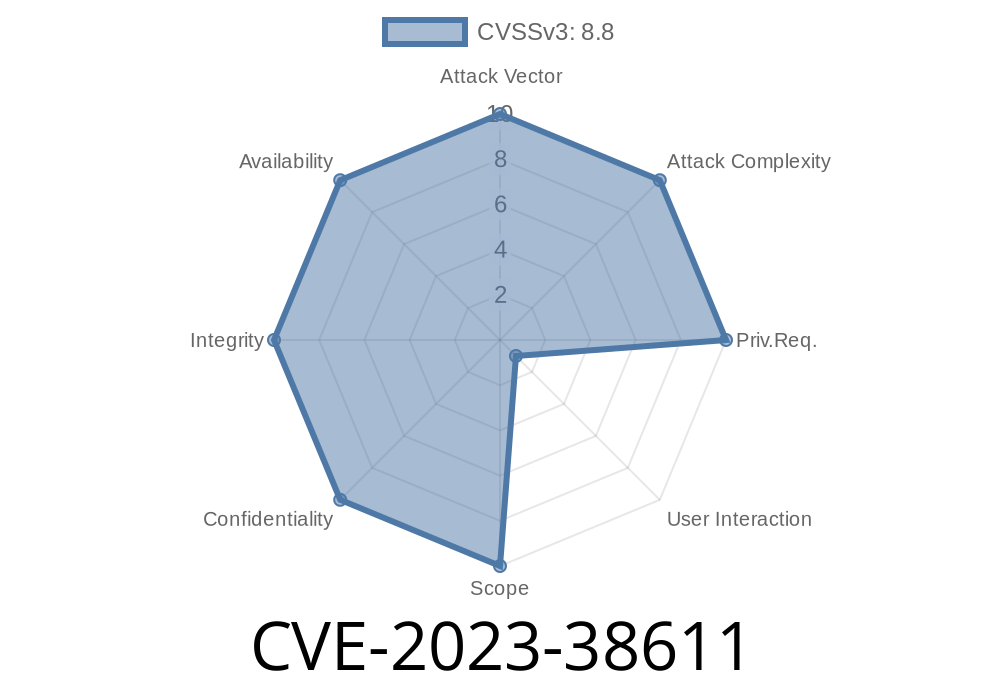
In June 2023, Apple patched a security flaw known as CVE-2023-38611 across its major platforms, including iOS, iPadOS, macOS, tvOS, watchOS, and Safari. This bug allowed attackers to execute code on your device simply by tricking you into viewing a malicious web page. Let’s break down what happened, how it worked, and what Apple did to stop it.
What is CVE-2023-38611?
This vulnerability affected WebKit, the browser engine powering Safari and much of web browsing on iPhones, iPads, and Macs. Here's how Apple described the issue:
> “Processing web content may lead to arbitrary code execution. This issue was addressed with improved memory handling.”
> — Apple Security Update, July 2023
How Did It Work?
At its core, this was a memory safety issue. WebKit had a bug where handling certain web content would allow attackers to cause a “memory corruption” error—a classic flaw that hackers love to exploit.
Uses freed memory, letting an attacker “overwrite” critical structures.
Here’s a simplified code example showing how such bugs can lead to trouble (not the real Safari code, but a teaching demo):
// Hypothetical unsafe code in a browser engine
char web_buffer[256];
// Web page sends data to the browser
void load_web_content(const char *user_input) {
// BUG: No check on input length!
strcpy(web_buffer, user_input);
// Hacker can now overflow buffer with evil code
}
The Exploit: How Attackers Weaponized It
1. Malicious web page: An attacker designs a website with sneaky JavaScript that triggers the vulnerable code path in WebKit.
2. Memory corruption: Carefully crafted data sent to your browser causes memory corruption.
3. Code execution: The hacker’s code runs with the same permissions as Safari—potentially accessing files, cookies, or even installing spyware.
In some cases, these bugs are combined with others (like bypassing Safari’s sandbox) to take full control of devices. No user interaction beyond visiting the booby-trapped website is needed.
The following is an illustrative pseudocode showing an attack technique
// Fake: For demonstration only!
let bigArray = [];
for (let i = ; i < 100000; i++) {
bigArray.push(x41414141); // Push data to trigger vulnerability
}
// Use bug to change memory, then inject malicious code
In real-world bugs, attackers have to chain complex tricks, but buffer overflows like this are highly prized targets.
So, instead of using the unsafe code from above, safe code would now look something like
void load_web_content(const char *user_input) {
// SAFER: Check input length before copying
strncpy(web_buffer, user_input, sizeof(web_buffer) - 1);
web_buffer[sizeof(web_buffer) - 1] = '\'; // Null-terminate
}
This prevents attackers from overflowing the buffer with malicious instructions.
References & Further Reading
- Apple’s Security Updates for July 2023
- NIST CVE-2023-38611 Details
- WebKit Bug Reports
Consider enabling automatic updates on all your Apple gear.
Remember: Memory bugs in browsing engines are critical—always update as soon as patches come out!
Conclusion
CVE-2023-38611 is a perfect example of how one hidden flaw in browser memory handling can potentially let hackers “open the door” on billions of Apple devices. With a quick update, Apple shut that door—but these bugs keep popping up. If you want to keep your data and devices safe, updates are your best friend.
*Stay safe, and always keep your software up-to-date!*
Timeline
Published on: 07/27/2023 01:15:39 UTC
Last modified on: 08/18/2023 03:15:21 UTC