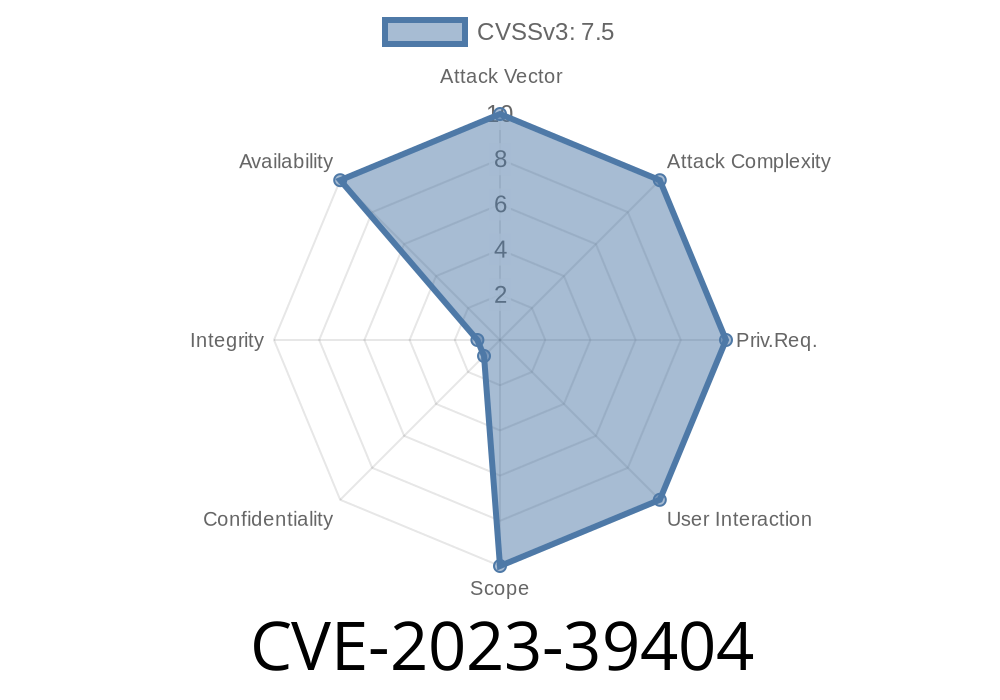
In mid-2023, a critical vulnerability surfaced that affects the window management component of some operating systems and device firmware. Tracked as CVE-2023-39404, this flaw revolves around improper input validation in certain APIs—a classic problem with serious modern consequences. In this post, we dig deeper into what this vulnerability is, how it works, and what it means for not just system admins and developers, but end users too.
What Is CVE-2023-39404?
At its heart, CVE-2023-39404 is a software bug in the code that handles window management. Think of this as the backend system responsible for opening, closing, and moving app windows on your device—but it’s also used in devices without a traditional screen, where “windows” can refer to system resources or UI elements.
The vulnerable APIs are supposed to check and “sanitize” the data (input parameters) they get from applications or system processes. But, due to poor validation, it’s possible for an attacker to send bad data, causing the system to malfunction.
Most notably, exploiting this bug can restart your entire device unexpectedly. In production environments or on critical endpoints, this could mean denial of service attacks, loss of unsaved work, or even deeper system corruption.
Where Did This Happen?
This vulnerability was originally identified in Huawei's window management module, mainly affecting devices running HarmonyOS 2. and newer. But the same pattern of input verification flaws is common across many systems with complex window or UI frameworks.
References
- Huawei Security Advisory - CVE-2023-39404
- CVE Details Page
At the code level, here’s a simplified look (in C-like pseudocode) at what went wrong
// Vulnerable function in window management module
int CreateWindow(int width, int height, const char* title) {
// BAD: No validation on width/height!
Window* w = malloc(sizeof(Window));
w->width = width;
w->height = height;
strcpy(w->title, title);
system_register_window(w);
return ;
}
An attacker might call CreateWindow() with super large or negative values for width or height, or a malicious title parameter. This can:
Lead to unexpected conditions the system can’t handle
The end result? Your device becomes unstable and may spontaneously restart.
Exploit Details: How Attackers Can Trigger a Restart
Step 1: Craft Malicious API Call
The attacker—maybe via a malicious app, or carefully crafted system call—asks the window management module to open a window with crazy, abnormal parameters. For instance, height and width set to 999999 or something negative, or a title string that’s much too long.
Step 2: Overwhelm System Memory or Cause Fault
Because the API fails to check the inputs, the system will try to allocate huge amounts of memory or behave unpredictably.
Step 3: Unhandled System Crash
At some point, the memory allocator fails, or a protection mechanism (like a watchdog timer) triggers, causing an immediate device restart to prevent further damage.
Sample Exploit in C-like Pseudocode
// On a compromised or test system
CreateWindow(9999999, 9999999, "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...");
Proof Of Concept (POC) Shell Command (Android/HarmonyOS)
# Uses window manager shell interface (example, might differ by device)
am window create --width 99999999 --height 88888888 --title "$(head -c 8192 </dev/zero | tr '\' 'A')"
(Actual exploitability depends on whether the attacker has access to the relevant APIs—which may vary by platform and permissions.)
Why This Matters
Even though it “just” causes a restart, this flaw is a classic denial-of-service vulnerability. On consumer devices, it can be irritating, but in mission-critical devices (IoT, medical, industrial controls), it can be genuinely dangerous.
Takeaway:
Always validate input, especially in system-level APIs that touch resources like windows, memory, or hardware. Simple checks—like verifying that width and height are within reasonable limits—can stop exploits like CVE-2023-39404 before they start.
Responsible Disclosure & Patch Status
Huawei and other affected vendors have since released patches that fix the input validation logic. If you’re responsible for device security, make sure to apply relevant updates immediately.
- Full Security Bulletin from Huawei
Final Thoughts
CVE-2023-39404 is another important reminder that the biggest attacks can stem from the smallest oversights. A missing input check in window management code can bring down your entire device—even when you think nobody has access to those APIs.
Update your systems. Review your code. Don’t underestimate the humble input parameter!
*This post brought the issue to light in simple terms with clear examples. For more details, always check the original advisories and test patches in your environment.*
Timeline
Published on: 08/13/2023 13:15:00 UTC
Last modified on: 08/17/2023 13:53:00 UTC