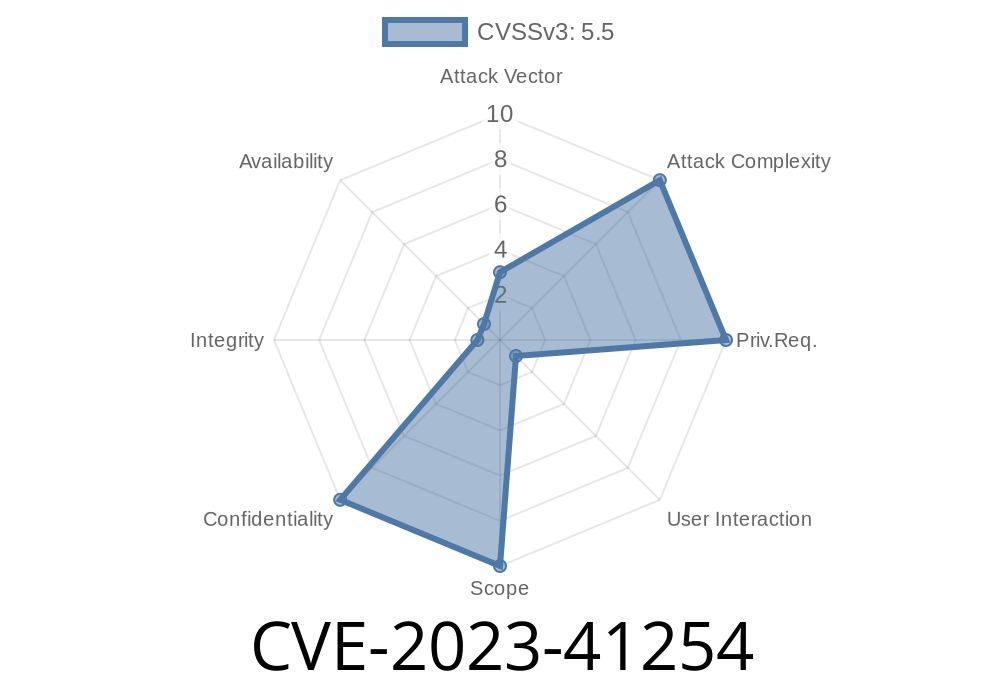
In October 2023, Apple quietly patched a privacy hole in multiple operating systems. This flaw, tracked as CVE-2023-41254, might sound technical, but its effect is simple: your sensitive private data could leak into an app’s logs, putting your privacy at risk. Let’s break down what happened, why it matters, how attackers could exploit it, and what you need to do to stay safe.
What is CVE-2023-41254?
CVE-2023-41254 is a privacy issue affecting several Apple platforms, including iOS, iPadOS, watchOS, and macOS. The bug allowed apps to access sensitive user data that should have been hidden, due to improper handling and redaction of log entries.
How Did the Flaw Work?
Every time you use an app, there’s a chance it writes information to a log file—a kind of digital diary. These logs are meant for debugging, not for sharing your secrets. Apple tries to "redact" (hide) sensitive info, like your name, address, passwords, or tokens, from these logs before anything is stored or sent.
But with CVE-2023-41254, that “redaction” failed—some sensitive information wasn’t properly filtered from logs. That means a rogue app could comb through these logs looking for secrets.
Suppose your app logs a line like this
os_log("User email is %@", userEmail)
Apple’s logging system is supposed to automatically hide or mask the email, but with the bug present, the raw email might appear in the logs instead.
Unsafe Example (before patch)
import os
let userEmail = "user@example.com"
os_log("User email is %@", userEmail)
// Log might show: User email is user@example.com
A malicious app could read these logs and steal the email address.
Exploit Details: How Could Bad Apps Use This?
It’s important to note this bug didn’t allow remote attackers to hack your device—they needed to have an app installed. Still, here’s how an attack could play out:
Malicious app installed: The user installs an app (on iPhone, iPad, Mac, or Apple Watch).
2. App reads system or its own logs: The app requests access to certain logs or reads its own detailed logs.
3. Sensitive data leak: Because of improper redaction, the logs contain private information—email addresses, authentication tokens, user IDs, etc.
Sample Swift code an attacker might use
let logURL = URL(fileURLWithPath: "/path/to/logfile.log")
if let logContent = try? String(contentsOf: logURL) {
if logContent.contains("@") { // crude email search
// Send email or token to attacker's server
}
}
Apple’s Fix
Apple addressed this vulnerability by improving redaction in logging subsystems. Logs now better filter out private user data.
macOS Sonoma 14.1
Apple’s advisory:
Apple Security Updates – CVE-2023-41254
What Should You Do?
- Update your devices: Make sure your iPhone, iPad, Apple Watch, and Mac are running the latest software.
- Be careful what you install: Only download apps you trust; avoid apps with poor ratings or shady backgrounds.
Original References
- Apple CVE-2023-41254 Security Advisory
- Apple Security Updates
- NIST NVD CVE-2023-41254
Conclusion
CVE-2023-41254 is a real reminder that even the best systems can leak our data in subtle, invisible ways. Apple’s quick patch shows they take privacy seriously, but it’s always good to keep your devices updated—and stay mindful of which apps you trust with your data.
Timeline
Published on: 10/25/2023 19:15:09 UTC
Last modified on: 11/02/2023 15:20:39 UTC