Apple enthusiasts always appreciate the Cupertino-based company for its dedication to privacy and security. But, just like any tech titan, Apple occasionally finds itself patching flaws that could be disastrous if left unchecked. One such issue came to light in late 2023: CVE-2023-42847. Buried in the change logs of macOS Sonoma 14.1, iOS 17.1, and iPadOS 17.1, this vulnerability had the potential to let attackers access your *passkeys* without ever needing to authenticate.
Let's break down what happened, how it worked, and what you can do to stay secure.
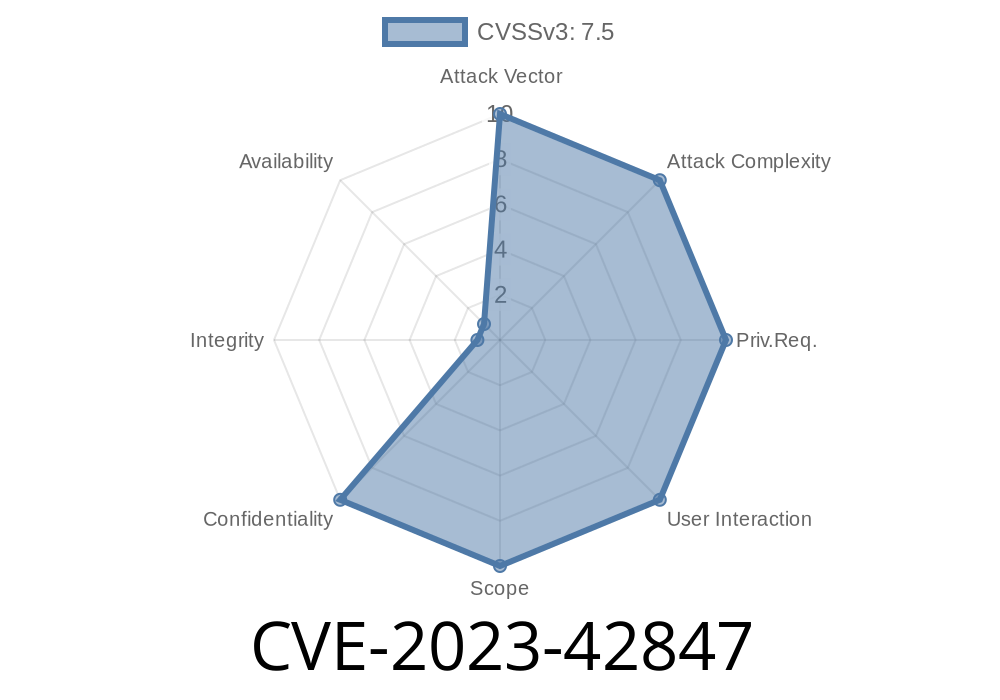
This vulnerability is described quite simply in Apple’s official advisory
> *A logic issue was addressed with improved checks. This issue is fixed in macOS Sonoma 14.1, iOS 17.1, and iPadOS 17.1. An attacker may be able to access passkeys without authentication.*
In basic terms, some mistake in the code ("logic issue") meant that a clever attacker could potentially open up your device and snag your passkeys, which are intended to replace passwords and work as a more secure authentication technology.
Passkeys are supposed to be stored in such a way that even if someone cracks open your phone or Mac, they won’t be able to use the passkeys without your face, fingerprint, or device passcode. This bug broke that critical protection.
How Did the Vulnerability Work?
The root problem here was a logic error in the way the system handled access checks for passkeys. Normally, when an app tries to read a passkey, iOS or macOS is supposed to prompt the user for authentication—like a Face ID scan, Touch ID, or passcode. Users get a dialog, and without verifying, the app (and any attacker) can’t proceed.
But due to this bug, the code skipped or failed the check in certain situations. That meant a malicious app, or attacker with app access, could read out passkeys with zero authentication.
Imagine if you could walk into a bank vault just by opening the door, without anyone asking who you are or for a keycard. That’s more or less what this allowed.
A Simplified Code Example
While Apple hasn't published the vulnerable code, here’s a very simplified example of what might have gone wrong (using Swift-style pseudocode):
func accessPasskey() {
if userIsAuthenticated() {
// Properly allow access
showPasskey()
} else {
// Logic error: forgot to block access
showPasskey() // <-- Should NOT be here!
}
}
In this flawed example, regardless of the authentication, the function gives up the passkey. The correct logic should block access unless the user is authenticated.
What Could an Attacker Do?
If an attacker compromised your device (for example, by getting you to install a malicious app with certain permissions), they could potentially use this vulnerability to read your passkeys.
Links to Original References
- Apple Security Advisory for CVE-2023-42847 (Apple Newsroom)
- CVE-2023-42847 Details (MITRE)
- macOS Sonoma 14.1 Release Notes
- iOS 17.1 Release Notes
Final Words
Vulnerabilities like CVE-2023-42847 are powerful reminders that even the best security systems are only as strong as their weakest lines of code. Apple’s quick fix kept this from turning into a larger crisis, but the take-home lesson remains: never ignore security updates—they may be the only thing standing between your data and the bad guys.
Timeline
Published on: 10/25/2023 19:15:10 UTC
Last modified on: 11/02/2023 18:14:06 UTC