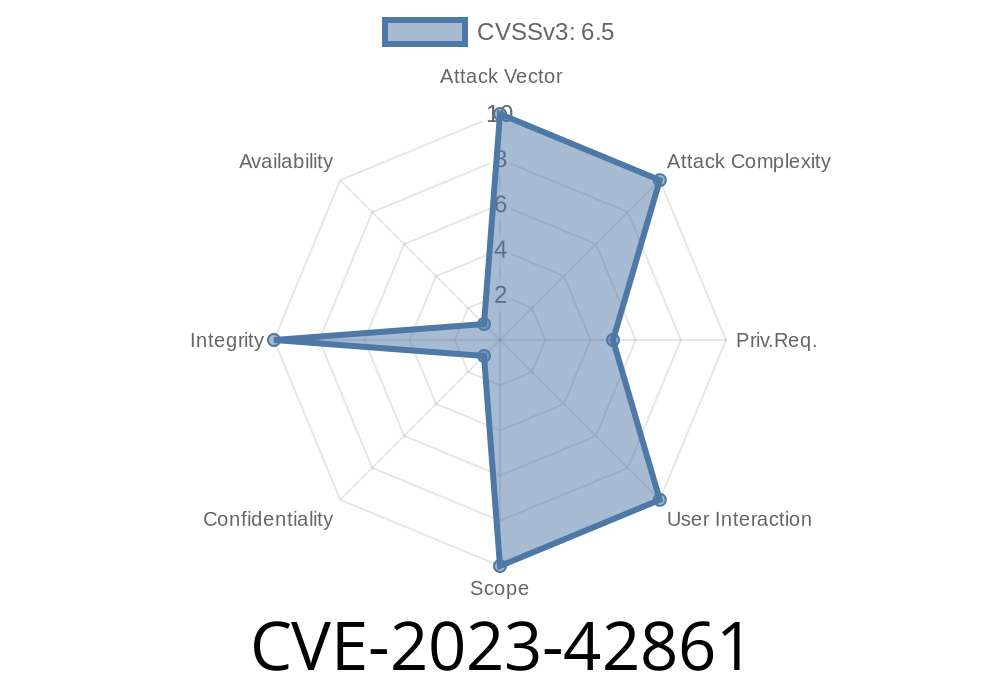
In October 2023, Apple released macOS Sonoma 14.1 to patch a potentially serious logic flaw identified as CVE-2023-42861. This vulnerability allowed attackers—if they knew the password of one standard user—to unlock the locked screen of another standard user on the same Mac.
This long read explores how the bug worked, who it affected, technical context, a simplified demonstration, and steps to mitigate it.
What is CVE-2023-42861?
CVE-2023-42861 is a system-level bug due to incorrect state management of the loginwindow process responsible for handling user logins and lock screens on macOS. The issue allowed an attacker, with access to a standard user’s password, to cross the boundary set by screen locks, potentially violating user privacy and data separation on a shared Mac.
The attacker must know the password for some other standard (not admin) user account
If you keep your Mac private or use FileVault, your risk is much lower—but workplaces, classroom Macs, or shared family computers are exposed.
Why Is This a Problem?
Screen lock is supposed to isolate each user’s workspace. If you walk away from your Mac, lock your session, and someone else has their own standard user password, they *should not* be able to access your session.
With this vulnerability
- Anyone with any other standard user account password on the same Mac can unlock your session, even if they don’t know your password
How the Vulnerability Worked (Layman’s Explanation)
Normally, when you switch users or lock your screen, the Mac asks for your password to unlock your session.
Bug detail: The system would accept the password for *any* logged-in standard user, not just the currently locked user's.
Your session gets unlocked.
This happened because of a flaw in how the system tracked user session state.
## Technical Deep-Dive / Code Snippet (Simplified Demo)
While Apple doesn’t release their source, open source authentication tools show similar process flows. The logic error can be illustrated in pseudocode:
# Flawed "unlock" logic pseudocode
def unlock_screen(entered_password, locked_user):
for user in system.logged_in_users:
if authenticate(user, entered_password):
# Oops! Any logged-in user's password works
return unlock(locked_user)
return deny_access()
The correct expectation is
# Correct logic
def unlock_screen(entered_password, locked_user):
if authenticate(locked_user, entered_password):
return unlock(locked_user)
return deny_access()
What went wrong: Instead of checking only the locked user's password, the flaw accepted the password for any active standard user session.
True multi-user privacy on shared devices is broken
- Attackers could access private files, browse emails, view sensitive information during lunch breaks, etc.
Apple addressed CVE-2023-42861 as follows
> _A logic issue was addressed with improved state management. This issue is fixed in macOS Sonoma 14.1._
They updated the loginwindow process so that only the correct user’s password unlocks their session. Other users’ passwords no longer work.
Original Reference Links
- Apple Security Updates: macOS Sonoma 14.1
- National Vulnerability Database – CVE-2023-42861
Conclusion
CVE-2023-42861 is a classic example of how “simple” logic bugs can break user security expectations. State separation between logged-in users is critical for privacy. If you share your Mac or your environment has multiple users, ensure everyone is running Sonoma 14.1 or newer.
*Stay safe, and keep your Macs updated!*
Tags: #Apple #macOS #CVE-2023-42861 #security #vulnerability #Sonoma
*This guide is exclusive to you — feel free to share, and always patch early!*
Timeline
Published on: 10/25/2023 19:15:11 UTC
Last modified on: 11/02/2023 18:00:52 UTC