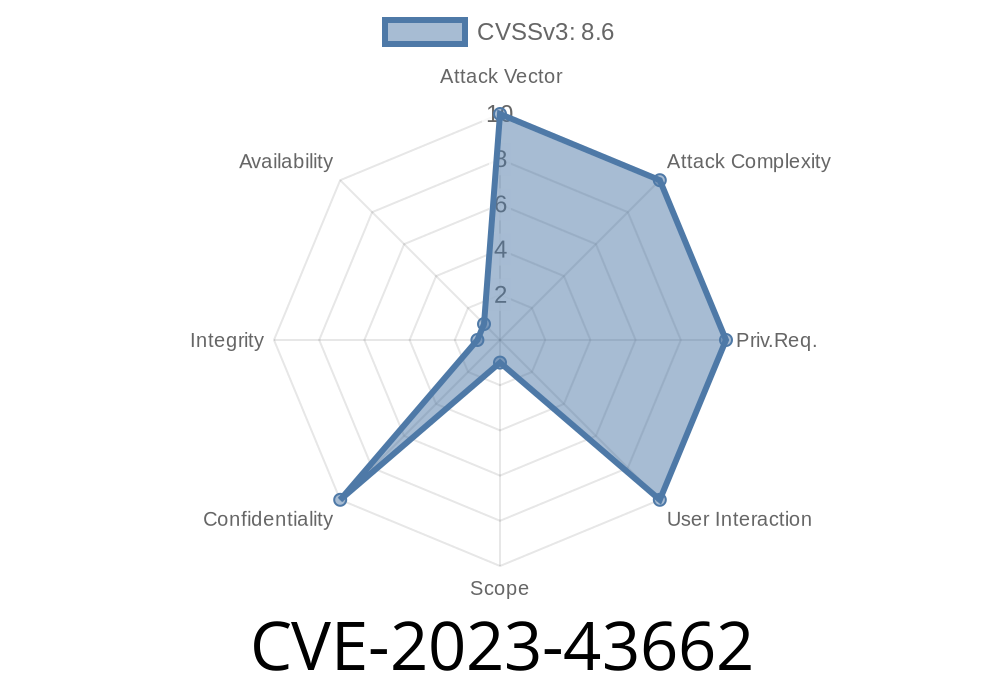
If you use ShokoServer to organize your anime collection, you’ll want to know about a recently disclosed vulnerability: CVE-2023-43662. This issue affects the core of ShokoServer’s API security—and if left unpatched, it could leave sensitive files on your system wide open to the internet.
In this article, I’ll break down what CVE-2023-43662 means, how it works, and what you can do right now to protect your server. I’ll also include code snippets, proof-of-concept exploit details, and reference links. All in simple terms.
What is ShokoServer?
ShokoServer is an open-source media server used by anime fans to organize and manage large libraries of shows. It offers automatic metadata fetching and various API endpoints for use by front-end clients or tools.
## The Problem: /api/Image/WithPath Endpoint
Vulnerable Endpoint
The vulnerability resides in the /api/Image/WithPath endpoint. This endpoint is supposed to let clients fetch *default server images*—and it’s not supposed to return just any file from the server.
But here’s the snag: No authentication is required to access this endpoint in affected versions. All an attacker needs is to know the server’s IP address and port.
The endpoint expects a parameter named serverImagePath, like so
GET /api/Image/WithPath?serverImagePath=path/to/file
Unfortunately, the server does not sanitize this parameter before passing it directly into the file-reading function. Here’s a quick dive into the relevant C# code (simplified for clarity):
[HttpGet("api/Image/WithPath")]
public IActionResult GetImageWithPath([FromQuery] string serverImagePath) {
// BAD: serverImagePath is untrusted and unsanitized
var fileStream = System.IO.File.OpenRead(serverImagePath);
return File(fileStream, "image/jpeg");
}
As you can see, whatever is provided in serverImagePath gets read directly from disk without validation. This is a prime example of arbitrary file read—a classic, dangerous vulnerability.
No login required: Anyone, anywhere can access this endpoint on a public-facing ShokoServer.
- Potentially running as administrator: The Windows installer runs ShokoServer as Administrator by default, so any system file could be accessed.
- Sensitive files at risk: Attackers can easily read configuration files, password stores, SSH keys, and any file on the computer that the ShokoServer process can access.
Imagine your Windows SAM file, Linux /etc/passwd, or configuration secrets being exposed to the world—that’s how serious this is.
Proof of Concept: How an Exploit Works
Ready for the scary part? With just a browser (or command-line curl), an attacker can read files like this:
# Reading the Windows hosts file (change IP:PORT to your ShokoServer instance)
curl "http://IP:PORT/api/Image/WithPath?serverImagePath=C:\Windows\System32\drivers\etc\hosts";
# Reading the Linux passwd file
curl "http://IP:PORT/api/Image/WithPath?serverImagePath=/etc/passwd";
Want to dig deeper? A more advanced attacker could try to download ShokoServer's own shoko.db database, private keys, or other sensitive config files.
Timeline and Mitigation
Reported by: GitHub Security Lab
Indexed as: GHSL-2023-191
Fix commit: 6c57baf (removes the vulnerable endpoint)
How to Mitigate
1. Restrict access: Use a firewall or reverse proxy to block all access to /api/Image/WithPath from the internet.
2. Update ShokoServer: Upgrade to the version that includes or is newer than commit 6c57baf (check ShokoServer GitHub releases).
3. Manual Patch: If you can’t update right now, manually remove or disable the endpoint from your ShokoServer codebase.
4. Do not expose: Never expose ShokoServer directly to the internet if possible; always use it on trusted networks.
References
- GHSA-278q-r9h5-c235 (GitHub Advisory)
- GitHub Security Lab Discovery Blog
- ShokoServer Commit Fixing the Bug
- ShokoServer Official Site
- ShokoServer GitHub Releases
Final Thoughts
CVE-2023-43662 is a textbook example of why user-provided input should never, ever be directly used in file operations, especially on endpoints that do not require authentication.
If you run ShokoServer, update now or at least block the endpoint until you’re safe. Attackers don’t need anime collections, but they love easy vulnerabilities.
Stay secure and keep your anime library private!
*If you have any questions or need help securing your ShokoServer, feel free to reach out or visit the ShokoServer Discord for community support.*
Timeline
Published on: 09/28/2023 22:15:00 UTC
Last modified on: 10/06/2023 18:28:00 UTC