If you’re a developer, sysadmin, or just someone who loves using Vim, you should pay close attention to a recently discovered vulnerability: CVE-2023-4734. This post breaks it down in plain English, explains how attackers could exploit this flaw, and includes code snippets to help you understand what’s going on under the hood. We'll also link to the original sources and give you tips to stay secure.
What is CVE-2023-4734?
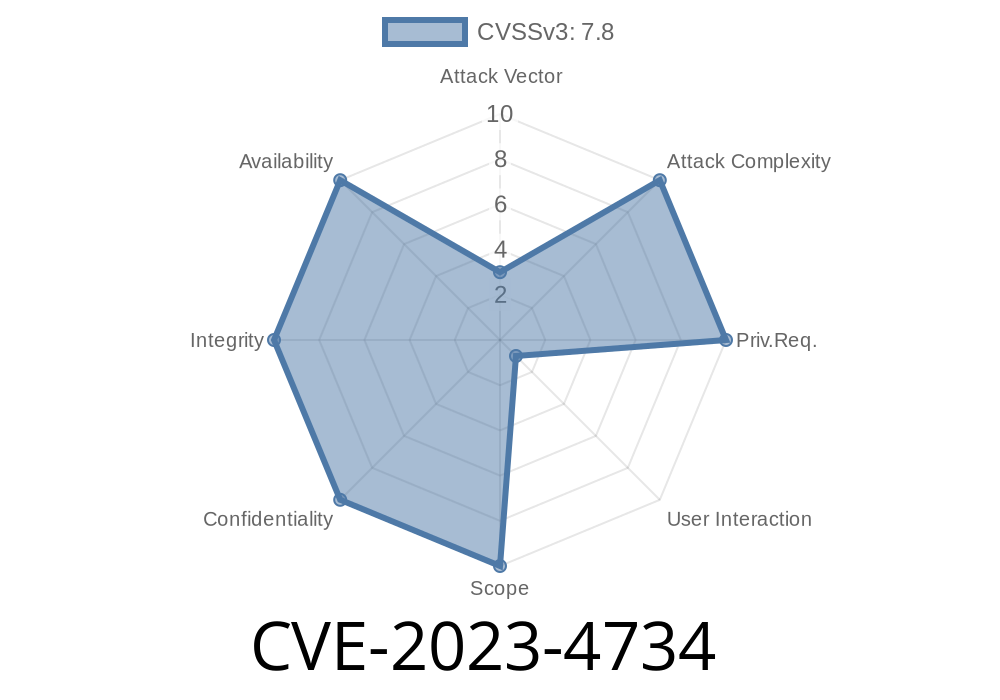
CVE-2023-4734 is an Integer Overflow or Wraparound vulnerability found in the Vim text editor, specifically in versions before 9..1846. This vulnerability lives in vim/vim, one of the most popular text editors on Linux and Unix systems.
Put simply, improper handling of large numbers in the code could let attackers manipulate how Vim performs memory allocations—potentially leading to crashes, unexpected behavior, or even code execution.
The Root Cause: Integer Overflow or Wraparound
In older versions of Vim, some internal code does arithmetic with integers for things like memory allocation without properly checking values. In C, if you add two big enough numbers, they can “wrap around” back to zero or a small number, causing the program to under-allocate memory or write past the end of a buffer. That’s called integer overflow or wraparound.
Real-World Example
Imagine the code needs to allocate "length + 1" bytes for a string. If length is almost at the maximum integer value, then length + 1 actually wraps around to zero—meaning almost _no_ memory is allocated, but data is still written, causing bad things to happen.
Vulnerable Code (Before Patch)
Here’s a simplified version of the sort of buggy C code you might find (not from the Vim source directly, but shows the logic):
char *buffer;
size_t length = /* supplied by user, maybe from a file or command */;
buffer = malloc(length + 1);
if (buffer == NULL) {
// handle allocation error
}
strcpy(buffer, user_content); // Danger: No bounds check!
If length is very large, length + 1 wraps around to a tiny value, and malloc doesn’t get nearly enough buffer space—strcpy then overruns the buffer.
*The actual bug is a bit more complex and buried in Vim’s internals, but this is the pattern.*
How Could Attackers Exploit CVE-2023-4734?
Attackers could supply specially crafted input—like a big file or a weird sequence of commands—to trigger the integer overflow. This could result in:
Data corruption
While no proof-of-concept exploit has been posted publicly as of this writing, all the classic building blocks for memory corruption are present.
Vim Security Advisory:
NVD Entry:
Vuldb Writeup:
Vuldb Entry
The author of the fix (Bram Moolenaar and Vim contributors) added checks to ensure the sums don’t wrap around.
Exploit Scenario (How a Bad Actor Could Use This)
Let’s say an attacker creates a malformed Vim swap file or a magic string in a file that, when opened, forces Vim to calculate a very large size for a buffer—one that wraps around to just a few bytes. Vim then tries to read a lot of data into a tiny memory area, smashing memory and potentially taking over the process.
Here’s a sketch of a Proof of Concept in “pseudocode” (not working code!)
# Python pseudocode for creating a malicious file
very_large_length = (2**32) - 2 # will wrap around when +1
payload = b"A" * very_large_length
with open("evil.vim", "wb") as f:
f.write(payload)
If Vim tries to read this file into an under-allocated buffer, boom—crash or worse!
Be careful with unknown files.
Opening untrusted files is never perfectly safe; that’s doubly true when bugs like this are still being found.
Check your package manager.
If your Linux distro hasn’t shipped the latest Vim version, contact them or grab it from the Vim repo directly.
Use sandboxing where possible.
Use containers, VMs, or tools like Firejail to limit damage from a misbehaving app.
Closing Thoughts
CVE-2023-4734 is a solid reminder that even mature, trusted open-source projects can have dangerous bugs hiding in the code. Integer overflows are sneaky—and attackers love them.
So, whether you’re a developer, sysadmin, security enthusiast, or just someone who wants to keep their text editor from being a ticking time bomb, make sure you:
Stay safe and keep coding!
*Written by a security enthusiast. Feel free to share or link with credit.*
References:
- Vim security patches
- NVD CVE-2023-4734
- Patch Example
Let me know in the comments if you have questions about Vim security or want a walk-through of the actual patched code!
Timeline
Published on: 09/02/2023 18:15:00 UTC
Last modified on: 10/26/2023 00:15:00 UTC