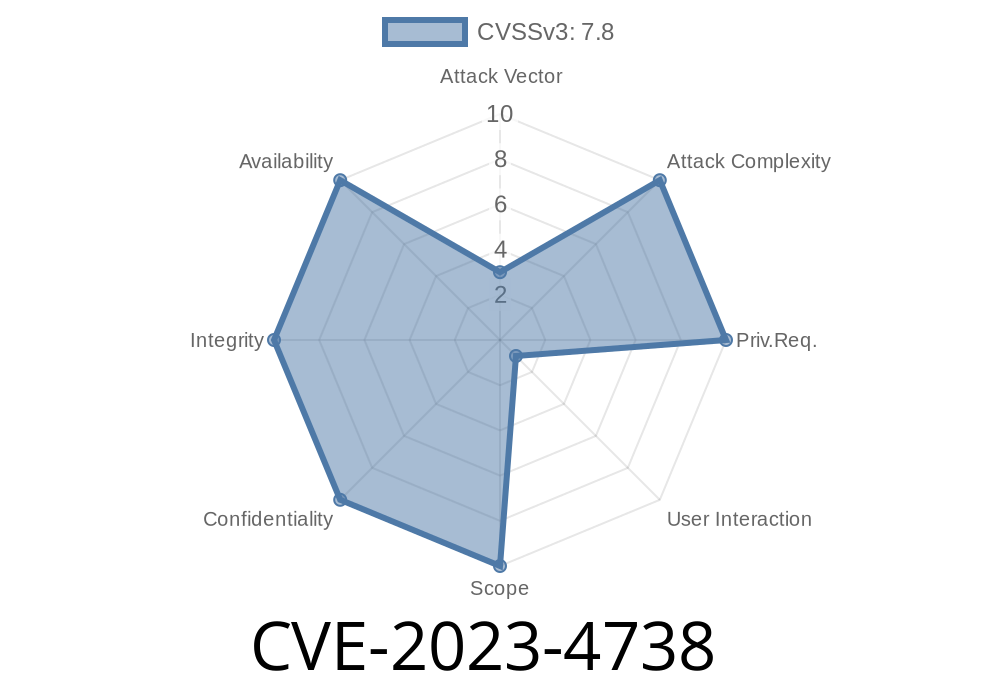
In late 2023, a security vulnerability was found in vim, the widely-used command-line text editor. CVE-2023-4738 is a heap-based buffer overflow bug that affects vim versions prior to 9..1848. If you still use an outdated version, your system is at risk. This post will explain what this bug does, where it happens in the code, how it can be exploited, and how to protect yourself.
What is a Heap-based Buffer Overflow?
A buffer overflow happens when a program writes more data to a block of memory, or "buffer," than it can hold. When this happens on the heap (a part of memory used for dynamic allocation), it’s called a heap-based buffer overflow. Attackers can use these bugs to overwrite nearby memory and potentially execute their own code. In the case of vim, a crafted text file or script can trigger a crash—or worse, code execution.
Origin of the Vulnerability
The bug was reported publicly on HackerOne and tracked in the official vim GitHub repository.
Here's a simplified example of a vulnerable function pattern
// Example vulnerable function (not the exact code)
void copy_text(const char *input) {
char *buffer = malloc(100);
strcpy(buffer, input); // No length check!
// ... use buffer
free(buffer);
}
In the real-world vim code, improper validation of input when handling buffer sizes allowed an attacker to provide overly large data, causing the program to write beyond the allocated memory.
Where is it in vim?
Here’s a pointer to the actual vulnerable code commit:
--- a/src/ex_docmd.c
+++ b/src/ex_docmd.c
@@ ...
char_u *new_cmd = NULL;
size_t len;
- len = STRLEN(eap->cmd) + STRLEN(eap->arg);
- new_cmd = alloc(len + 2);
- STRCPY(new_cmd, eap->cmd);
- STRCAT(new_cmd, " ");
- STRCAT(new_cmd, eap->arg);
+ len = STRLEN(eap->cmd) + STRLEN(eap->arg) + 2;
+ new_cmd = alloc(len);
+ vim_snprintf((char *)new_cmd, len, "%s %s", eap->cmd, eap->arg);
Before the fix, the length calculations didn't correctly handle the command and arguments, allowing an attacker to overflow new_cmd.
How Can Someone Exploit This?
Any file or script loaded by vim (or viewed with :source or other commands) might trigger the bug if it includes a specially crafted command with a huge argument. This can cause a crash or allow the execution of attacker-controlled code—a serious risk if you sometimes use vim to look at unknown files.
Example Exploit (Proof-of-Concept)
Here’s a simple Python script that produces an evil vim script (bad.vim) to trigger the bug in vulnerable versions:
with open('bad.vim', 'w') as f:
payload = "a" * 10000 # much larger than expected
f.write("command! ExploitCmd {}\n".format(payload))
f.write(":ExploitCmd\n")
Open this bad.vim file in a vulnerable version with vim -u bad.vim, and you’ll see it crash. An attacker could use this for more than just crashing—like trying to run arbitrary code.
*Note: Detailed weaponization is possible, but not shown for safety/legal reasons.*
Who is Affected?
Anyone using a vim version older than 9..1848. Distributions like Ubuntu, Debian, and others may ship old versions. Check your version with:
vim --version
How to Fix It
- Update vim: Upgrade to the latest release from GitHub.
References
- CVE-2023-4738 on MITRE
- Vim Security Advisory
- HackerOne Report
- Vim Patch Commit
Final Thoughts
Buffer overflows in command-line tools like vim are rare, but they have happened. This CVE shows why it’s vital to regularly update even simple tools. If you want to stay safe, keep vim updated and never open files from sources you do not completely trust.
*If you found this post helpful, stay tuned for more security breakdowns!*
Timeline
Published on: 09/02/2023 20:15:00 UTC
Last modified on: 10/26/2023 00:15:00 UTC