The internet is driven by sharing, and podcasts are one of the best ways for ideas to travel. But what if the tool you use to share is open to bad actors? Today, we're diving deep into CVE-2023-47691, a serious security issue discovered in the popular Podlove Web Player.
Let’s break it down in a way that’s easy to understand, showing you what happened and what you—or your tech team—should do about it.
What is Podlove Web Player?
Podlove Web Player is a flexible and open-source podcast player, used by countless WordPress sites and individual podcasters. Its charm lies in simplicity and customization, letting you share content anywhere on the web.
Website: https://podlove.org
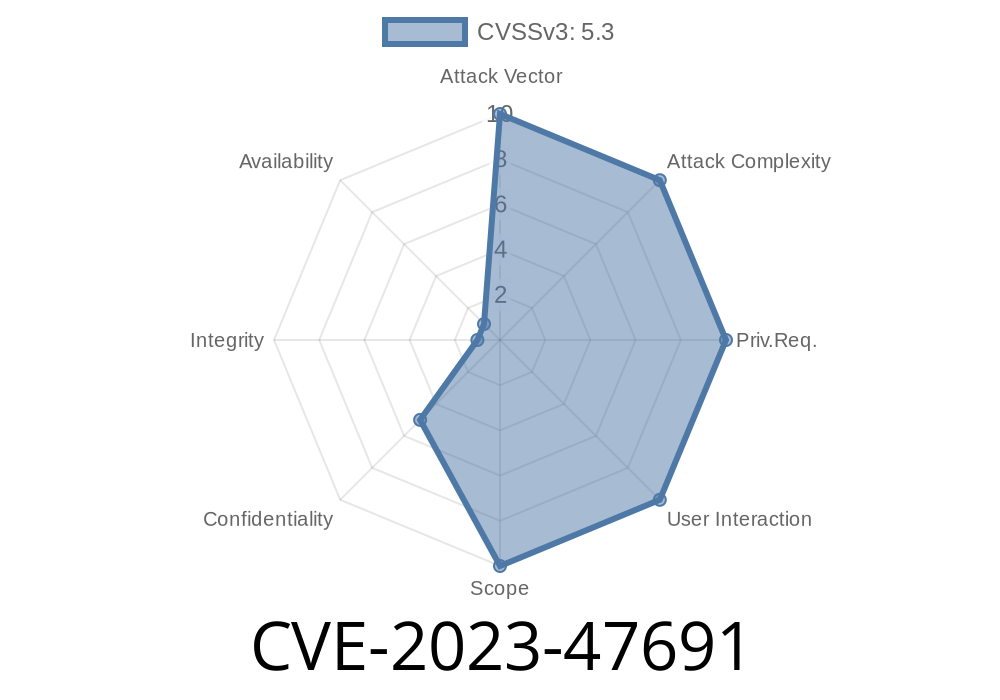
What is CVE-2023-47691?
This Common Vulnerability and Exposure (CVE) relates to a Missing Authorization bug in Podlove Web Player, affecting all versions up to and including 5.7.3.
In simple terms
- Some actions or API endpoints in Podlove did not check if a user was allowed to do what they were doing.
Anyone could invoke these actions, regardless of their permissions.
- A determined attacker could change podcast player settings, inject malicious data, or access information that should remain private.
Where’s the Problem? (Technical Details)
A key issue lies in how Podlove handled certain administrative or configuration actions through its REST API. Requests to endpoints did not require the user to be authenticated, or did not check user roles properly.
Imagine a simplified API handler in Podlove
app.post('/settings/update', (req, res) => {
// FLAW: No check if user is admin or authorized
const newSettings = req.body;
db.saveSettings(newSettings); // Dangerous: Anyone can call this!
res.send('Updated!');
});
If a route like /settings/update is exposed this way, a regular user (or even a non-logged-in attacker) can use curl or a web browser to POST new configuration data.
Suppose the /api/v1/settings endpoint updates player settings
curl -X POST https://victimsite.com/api/v1/settings \
-d '{"autoplay": true, "theme": "malicious-theme"}'
If the server does not check if you’re logged in or have admin access, this call will succeed. The attacker now controls how your player behaves on your site!
With more creativity, they might inject scripts or alter links to phish site visitors.
Upgrade Immediately:
Update to the latest release of Podlove Web Player.
Review Custom Integrations:
If you built custom API wrappers, make sure to require proper authorization before updating any settings.
Example Secure Handler (Node.js / Express)
app.post('/settings/update', ensureAdmin, (req, res) => {
const newSettings = req.body;
db.saveSettings(newSettings);
res.send('Updated!');
});
function ensureAdmin(req, res, next) {
if (!req.user || !req.user.isAdmin) {
return res.status(403).send('Forbidden');
}
next();
}
References & Further Reading
- GitHub Security Advisory for Podlove Web Player
- National Vulnerability Database - CVE-2023-47691
- Podlove Web Player Releases
Conclusion
CVE-2023-47691 is proof that missing a simple authorization check can spell big trouble. If you use Podlove Web Player, check your version and update as soon as you can. Always make sure only authorized users can access powerful features.
Stay safe, upgrade, and audit your endpoints!
If you want to go deeper or need help patching your site, check the official Podlove documentation or contact their support channels.
*By understanding vulnerabilities like this, we all help make the internet safer—for creators and listeners alike.*
Timeline
Published on: 03/07/2024 14:15:46 UTC
Last modified on: 03/08/2024 14:02:57 UTC