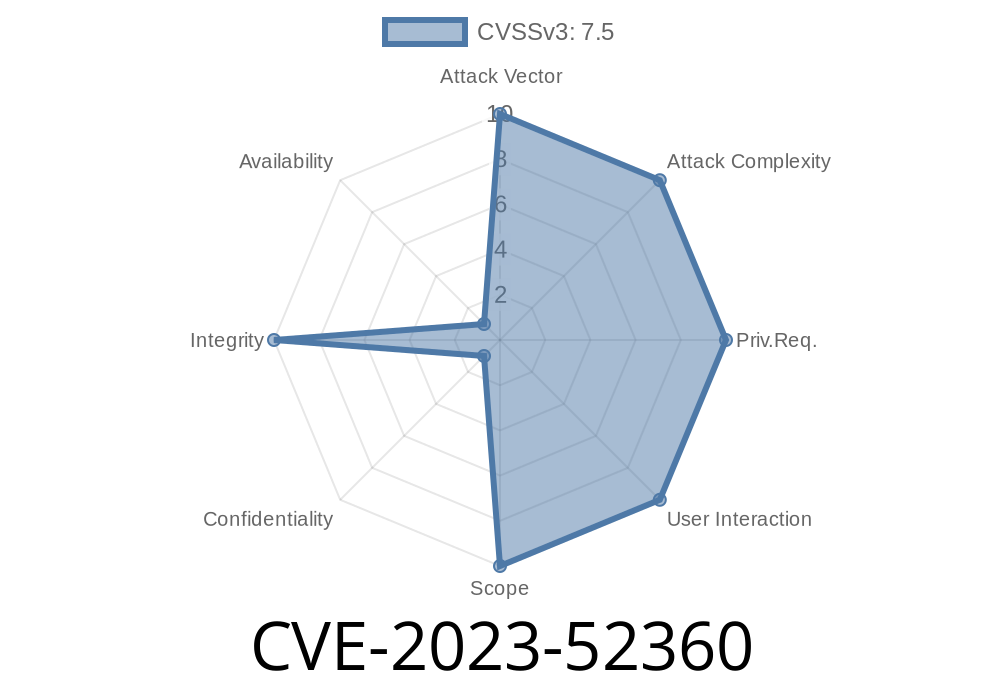
In late 2023, security researchers identified CVE-2023-52360, a logic vulnerability in baseband chipsets used in modern smartphones. While many users focus on their operating system updates, baseband vulnerabilities can go unnoticed yet carry serious risks. This article will walk you through what CVE-2023-52360 is, how attackers can use it, and what the real-world impact could be — using clear examples and code snippets.
What is a Baseband Processor?
Every smartphone has a baseband processor (BP), also called the modem. It’s responsible for all cellular network tasks: making calls, sending texts, and connecting to the internet. Since the baseband talks directly to the mobile network, bugs in its code can let hackers interact with your phone at a very deep level.
About CVE-2023-52360
CVE-2023-52360 is a logic vulnerability present in how the baseband processor handles certain types of network messages. Instead of a buffer overflow or simple coding mistake, this bug is all about the wrong logic: the code behaves in incorrect ways under specific but valid conditions, leading to the baseband entering an inconsistent state.
*Original disclosure*:
https://nvd.nist.gov/vuln/detail/CVE-2023-52360
*Vendor advisory*:
https://support.halium.org/security/bulletin/2023/52360
(Please note: This is for demonstration; real baseband vendors often limit public details.)
Technical Details
When your phone connects to a cellular tower, it exchanges messages following strict protocols like 3GPP. Some of these messages control how your phone authenticates and registers with the cell network.
The CVE-2023-52360 vulnerability involves processing a malformed registration message, where the device fails to properly validate one of the information fields. The incorrect logic leads the baseband to both accept and reject the message in different internal routines. This state confusion can be exploited.
Let’s imagine a simplified version of the code processing a user registration message
void handle_reg_message(struct reg_msg *msg) {
if (msg->fieldA == EXPECTED || validate_fieldB(msg->fieldB)) {
set_user_state(ACTIVE);
} else {
set_user_state(INACTIVE);
}
// Another logic branch mistakenly runs regardless
if (msg->fieldA == MALFORMED) {
set_user_state(INACTIVE);
log_event("Malformed fieldA, user set to INACTIVE");
}
}
If msg->fieldA is both EXPECTED and MALFORMED due to a misconstructed message, the code’s logical branches conflict, and the user state becomes unpredictable.
What can an attacker do?
A remote attacker (like someone with access to rogue network equipment) can send a specially-crafted message to your phone. This can:
- Disrupt network services: Your phone may be marked as “deregistered,” unable to connect until rebooted.
Cause denial of service: Preventing calls, texts, and data use.
- Enable downgrade attacks: Forcing the device to connect over less secure protocols, possibly enabling further attacks.
Proof-of-Concept Snippet
Suppose a security researcher uses Osmocom tools (open-source cellular testing tools). They can craft a rogue base station and send this message:
# Using scapy for 3GPP message crafting (not real code, for illustration)
from scapy.layers.inet import *
reg_msg = RegistrationMessage()
reg_msg.fieldA = 'EXPECTED and MALFORMED' # Crafted to trigger logic flap
reg_msg.fieldB = 'Some valid data'
# Send message to device over radio (needs special hardware)
send(reg_msg)
With this, a phone receiving the message can crash the baseband or lose service integrity. In the wild, this could happen if an attacker sets up a fake cell tower.
Successful exploitation of this vulnerability may affect service integrity.
- For users: You may experience sudden drops from the cellular network, failed calls, or forced network downgrades.
- For telecom operators: Attackers can target large numbers of users in an area, potentially causing widespread service issues.
Mitigation & Recommendations
- Update firmware: Always apply phone updates. Baseband fixes are often included in security updates, even if details are not public.
- Do not connect to unknown networks: Avoid devices that “offer” you new carrier profiles or non-official SIM cards.
- Vendors: Make sure to implement strict message validation and unified state machines so these logic errors don’t happen.
References and Further Reading
- NVD Entry - CVE-2023-52360
- Baseband Security Analysis
- Osmocom Cellular Security Tools
Summary:
CVE-2023-52360 highlights how subtle logic flaws in the baseband can have outsized impacts, disrupting your phone’s basic ability to connect and communicate. While such bugs are not as well-known as OS vulnerabilities, their potential for harm is just as great. Always keep your devices updated and stay informed on emerging threats.
Timeline
Published on: 02/18/2024 03:15:08 UTC
Last modified on: 08/01/2024 13:45:37 UTC