---
Google Chrome is one of the world’s most used browsers. With complex features and lightning-fast JavaScript support, thanks to its V8 engine, it’s a crucial part of our daily browsing. However, cyber threats keep evolving, and even the best software sometimes has critical bugs. One such issue is CVE-2024-12695, which grabbed attention due to its potential to let attackers run code on your machine – just by you visiting a bad webpage.
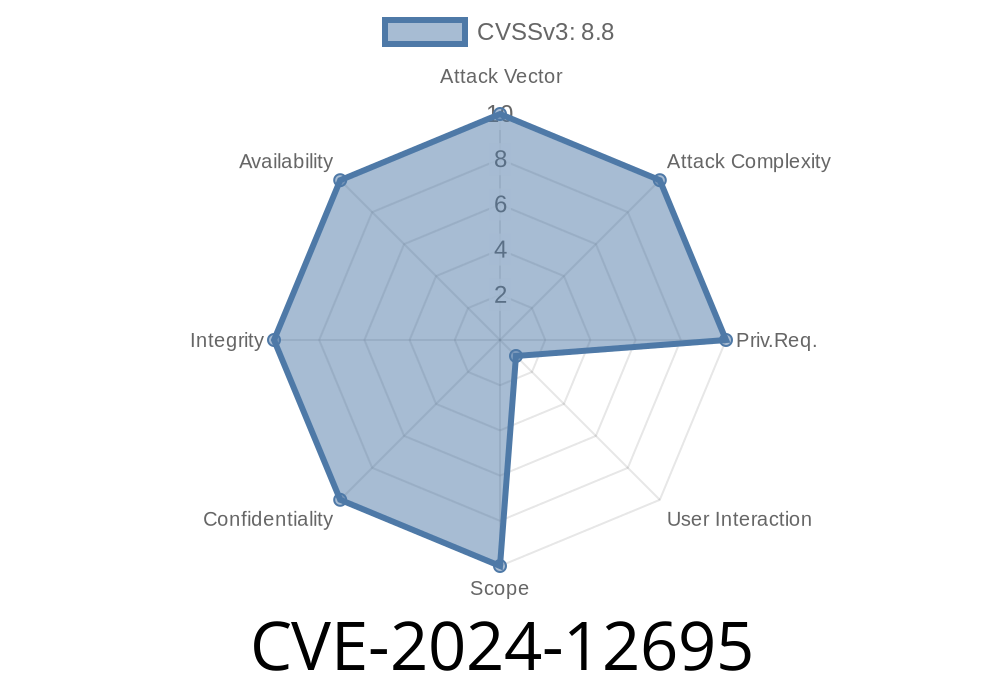
1. What is CVE-2024-12695?
On April 2024, Google issued a security advisory for Chrome, fixing multiple bugs. The most notable was:
> "Out of bounds write in V8 in Google Chrome prior to 131..6778.204 allowed a remote attacker to execute arbitrary code inside a sandbox via a crafted HTML page. (Chromium security severity: High)"
Simple translation: A bug in the JavaScript engine (V8) could let attackers break out of normal restrictions and run custom code, just by you landing on a malicious website.
2. How Does The Bug Work?
Out-of-bounds write (OOBW) occurs when the software writes data outside the allocated boundaries of memory (an array, buffer, or object). This is dangerous because it messes up nearby data, crash the process, or—worst—give an attacker a way to run their own code.
In V8, this can happen due to a flaw in handling arrays, typed arrays, or tricky optimizations the engine does. If memory boundaries are bypassed, hackers can overwrite executable code or vital memory chunks.
3. Demonstration With Code Snippets
Let’s look at a simplified way this could be triggered. (Note: This is for educational purposes only and based on public info!)
Suppose V8 mishandles a TypedArray object, allowing JavaScript to write beyond the array’s real length.
// Hypothetical code - for illustration only
let arr = new Uint32Array(10);
arr.length = xFFFFFFFF; // Force an oversize length via some exploit chain
arr[100000] = x41414141; // Write far outside original buffer
// Now 'arr' is overwriting memory after its buffer,
// potentially overwriting objects or code
If V8’s engine doesn't properly check array bounds, the line above writes uncontrolled data into forbidden memory. With clever tricks, an attacker can corrupt structures, change pointers, or hijack execution.
Gain arbitrary code execution (inside the Chrome sandbox).
Attackers usually need multiple bugs or advanced knowledge to escape Chrome’s strong sandbox, but this sort of memory bug can be the first step—especially in spearphishing or targeted attacks.
4. Exploit: Proof of Concept
A real-world exploit is complex. But to help understand, here’s what a skeleton exploit for OOB write could look like (heavily simplified):
// WARNING: Do not use; educational only
// Step 1: Allocate objects in memory
let arrs = [];
for(let i=;i<10000;i++) {
arrs.push(new Uint32Array(100));
}
// Step 2: Vulnerable operation
let victim = arrs[1234];
victim.length = x100000; // Oversize
// Step 3: Overwrite adjacent memory via OOB write
victim[200000] = x13371337;
// Step 4: Try to hijack something "next door" in memory
// (Usually requires knowledge of V8 internals)
> In practice, attackers chain this with info-leak bugs to make exploitation reliable.
Can bypass basic browser limits: Can manipulate V8 internals.
- Can lead to full remote code execution (RCE): With further bugs, may escape Chrome's sandbox, install malware, or spy.
6. Who is at Risk & What Should You Do?
Affected:
Platforms: Windows, Mac, Linux, etc.
Protection steps:
Update Chrome ASAP!
Visit chrome://settings/help to check your version.
Always restart your browser after an update.
Note: Other Chromium-based browsers (Edge, Brave, etc.) may also be affected if using the same V8 version.
7. References & Further Reading
- Google Chrome Release Notes (May 2024)
- Chromium Bug Tracker Entry (CVE-2024-12695) *(May be restricted until patch roll-out)*
- Official CVE Record for CVE-2024-12695
- Project Zero blog – Understanding Chrome exploits
8. Conclusion
CVE-2024-12695 proves even highly-secure tech like Chrome can have dangerous flaws. Out-of-bounds writes are a top target for hackers. Chrome’s quick patching kept many safe—but always staying updated, being wary of suspicious links or downloads, and knowing how to check your browser’s version are your best defenses.
Stay safe, and keep your software up to date!
*(You are free to share this post with credit. For responsible disclosure, do not attempt to exploit this bug. The information here is for educational security awareness.)*
Timeline
Published on: 12/18/2024 22:15:06 UTC
Last modified on: 01/06/2025 15:15:10 UTC