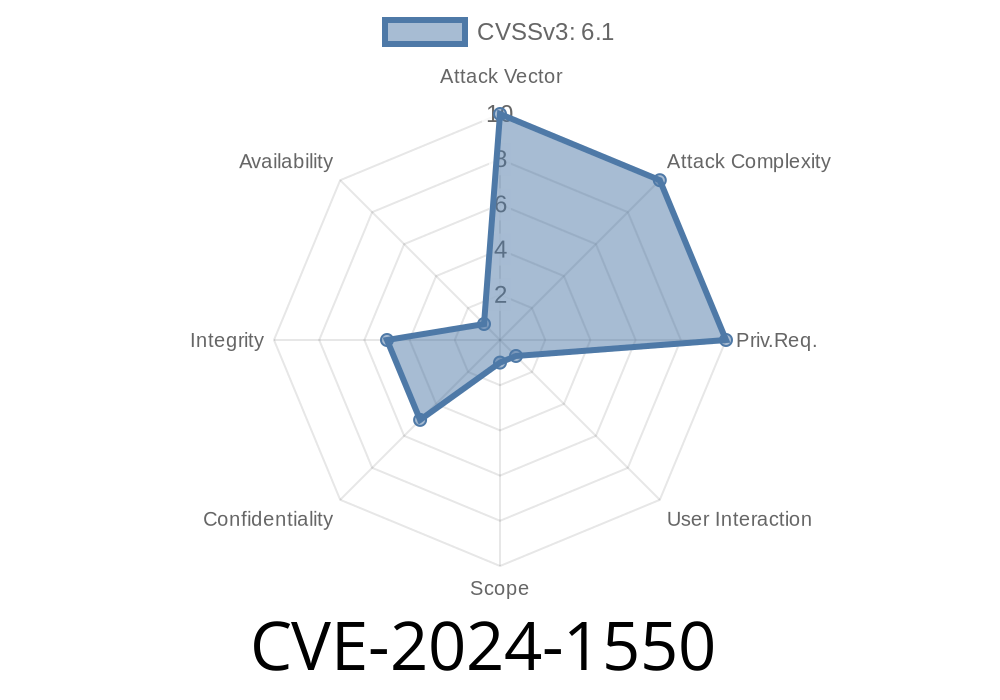
Cybersecurity threats are always lurking around the corner, ready to exploit vulnerabilities within software and take advantage of unsuspecting users. A recent vulnerability has come to light, identified as CVE-2024-1550, which affects Firefox versions earlier than 123, Firefox ESR (Extended Support Release) versions earlier than 115.8, and Thunderbird versions earlier than 115.8. This vulnerability could enable a malicious website to use a combination of exiting fullscreen mode and the requestPointerLock feature to re-position the user's mouse cursor unexpectedly, leading to user confusion and potentially causing users to grant permissions they did not intend to grant. This article provides an in-depth look at this vulnerability, its implications, and how to mitigate it.
How the Vulnerability Works
The crux of the vulnerability lies in the two aforementioned features: exiting fullscreen mode and the requestPointerLock API. The requestPointerLock feature is a JavaScript API used for games and other applications where cursor movement needs to be continuous and not bound by the screen's borders. It hides the cursor and captures all mouse movement events, allowing the application to utilize them.
The vulnerability arises when a website combines this feature with exiting fullscreen mode. A user visiting a website in fullscreen mode (such as watching a video) might not notice that the website has also requested a PointerLock. Once the user exits fullscreen mode, they might experience unexpected mouse behavior due to the ongoing PointerLock in the background. This could lead to user confusion and accidentally clicking on elements in the background, potentially granting permissions and taking actions they did not intend to take.
Here's some example code to demonstrate this exploit
document.addEventListener("fullscreenchange", () => {
if (!document.fullscreenElement) {
document.exitPointerLock();
}
});
document.querySelector("#btnFullscreen").addEventListener("click", () => {
document.documentElement.requestFullscreen();
document.documentElement.requestPointerLock();
});
In this example code, the btnFullscreen button requests both fullscreen mode and PointerLock when clicked. The fullscreenchange event listener exits the PointerLock once the user exits fullscreen mode. This combination could lead to unexpected mouse behavior as mentioned earlier.
Exploit Details & References
This vulnerability, tagged as CVE-2024-1550, was first reported by security researcher Tim Nguyen and confirmed by Mozilla, the organization behind Firefox and Thunderbird. The details can be found in Mozilla's security advisory here.
Mitigation
The best mitigation to protect against this vulnerability is to update your Firefox, Firefox ESR, or Thunderbird software to the latest versions available, which include patches for this vulnerability. Ensure that you are running at least Firefox version 123, Firefox ESR version 115.8, or Thunderbird version 115.8.
Conclusion
In conclusion, CVE-2024-1550 highlights the importance of regularly updating software to stay abreast of the latest security patches and keeping your system safe from potential exploits. It also emphasizes the need to be cautious while browsing the web, as seemingly benign actions such as exiting fullscreen mode can lead to unexpected consequences and compromise your security. Always remember to use the latest versions of your favorite software, and remain vigilant while navigating the online world.
Timeline
Published on: 02/20/2024 14:15:08 UTC
Last modified on: 12/10/2024 15:30:13 UTC