Published: June 2024
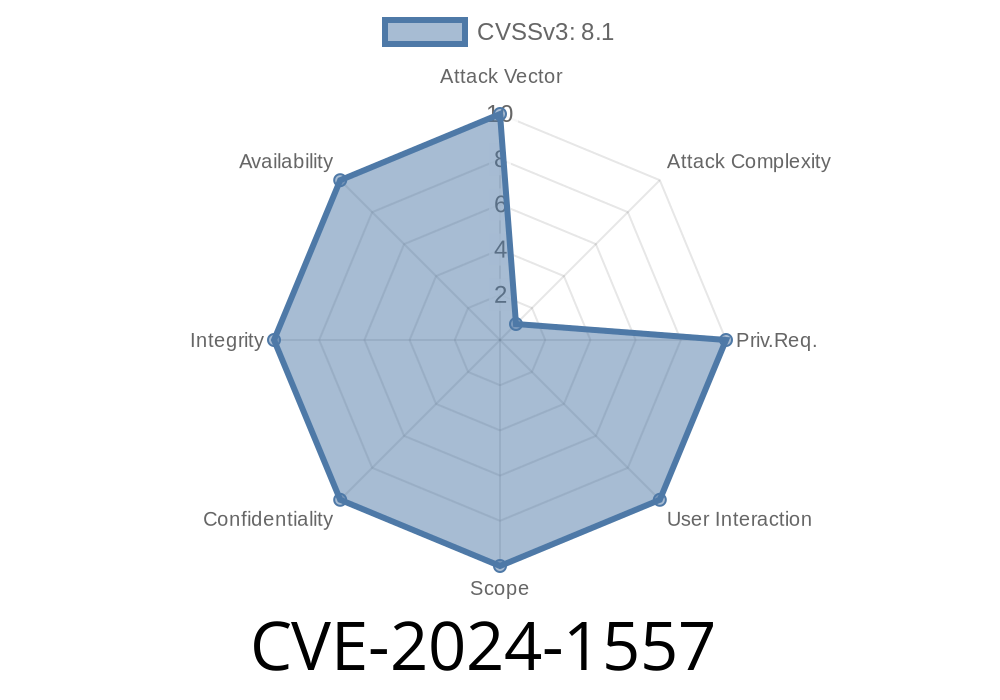
Severity: High
Affected Versions: Firefox < 123 (including Firefox 122)
Attack Vector: Remote
Exploitability: Possible Arbitrary Code Execution
Introduction
A new critical vulnerability has been discovered affecting Mozilla Firefox, tracked as CVE-2024-1557. This issue involves multiple memory safety bugs that were found in Firefox version 122. These bugs demonstrated possible memory corruption which, in certain circumstances, could let an attacker execute arbitrary code on your system by simply luring you to a malicious website.
In this article, you’ll get an exclusive, simplified explanation of the vulnerability, see code snippets illustrating the memory flaw, and review information on how attackers could exploit it.
What is CVE-2024-1557?
CVE-2024-1557 is a collection of memory safety vulnerabilities in the Firefox browser before version 123. The bugs mainly revolve around the way Firefox manages memory when handling certain web content. If an attacker tricks a user into opening a malicious website—or even a compromised ad—they could take control of user’s computer to run malicious software.
Mozilla’s official advisory:
- MFSA 2024-12 Security Vulnerabilities fixed in Firefox 123
What is a “memory safety bug”?
A memory safety bug happens when a program incorrectly handles computer memory. If this mistake leads to reading or writing outside allowed boundaries (“buffer overflow”), it could crash the browser or let attackers sneak malicious data into Firefox’s memory.
Simplified Example
Suppose Firefox is processing an image or script from a website. A bug might let the page send too much data, and Firefox tries to fit it into a fixed-size buffer:
// Pseudocode illustrating unsafe memory handling
char image_buf[1024];
int image_size = get_image_data_from_site(image_buf);
if (image_size > 1024) {
// Oops: buffer overflow! Too much data is being copied.
memcpy(image_buf, attacker_data, image_size);
}
Here, if image_size is greater than 1024, attacker-supplied data spills past image_buf’s boundary, overwriting critical memory. Clever attackers craft this spill to take over execution flow.
How Could Attackers Exploit This?
1. Prepare malicious content: An attacker crafts a web page exploiting the vulnerable memory operation—possibly affecting images, scripts, or other specific web elements.
2. Entice victims: The attacker gets users to visit the malicious page using phishing emails, malicious ads, or compromised legitimate sites.
3. Trigger the bug: When the victim’s Firefox 122 processes this content, the browser’s memory is corrupted.
4. Execute code: With enough skill and knowledge of browser internals, an attacker shapes the overflow to run their own commands—installing backdoors, stealing data, etc.
This kind of exploit is serious because the only defense—before the patch—is not visiting shady websites, which isn’t always practical.
Proof of Concept
While no public exploit code is known (and Mozilla wisely keeps details sparse), here’s a high-level PoC showing the *type of data* an attacker might use:
// Javascript - triggering a potential buffer overflow
var bigArr = [];
for (let i = ; i < 100000; i++) {
bigArr.push("A".repeat(10000)); // Fills browser memory
}
// Then trigger a bug with vulnerable API
try {
vulnerableFunction(bigArr.join(""));
} catch (e) {
// If exploit works, code execution may be possible here.
}
Important: The above is just an illustration! Actual exploits require deep browser knowledge and substantial research.
Firefox will check for updates and install version 123 or later.
If you use a Linux distribution, check your package manager for the latest updates.
Reference:
- Mozilla Firefox Download & Release Notes
References
- Mozilla Security Advisory MFSA2024-12
- CVE-2024-1557 in NIST NVD
- What is a buffer overflow? (OWASP)
Final Thoughts
CVE-2024-1557 is a serious vulnerability—proof that even the most popular browsers can harbor hidden dangers. Most users just need to update right away and stay vigilant. For defenders and researchers: remember, memory safety is hard, but regular patching helps keep everyone safer.
Stay safe,
*Your Cybersecurity Info Team*
Timeline
Published on: 02/20/2024 14:15:09 UTC
Last modified on: 08/12/2024 17:35:01 UTC