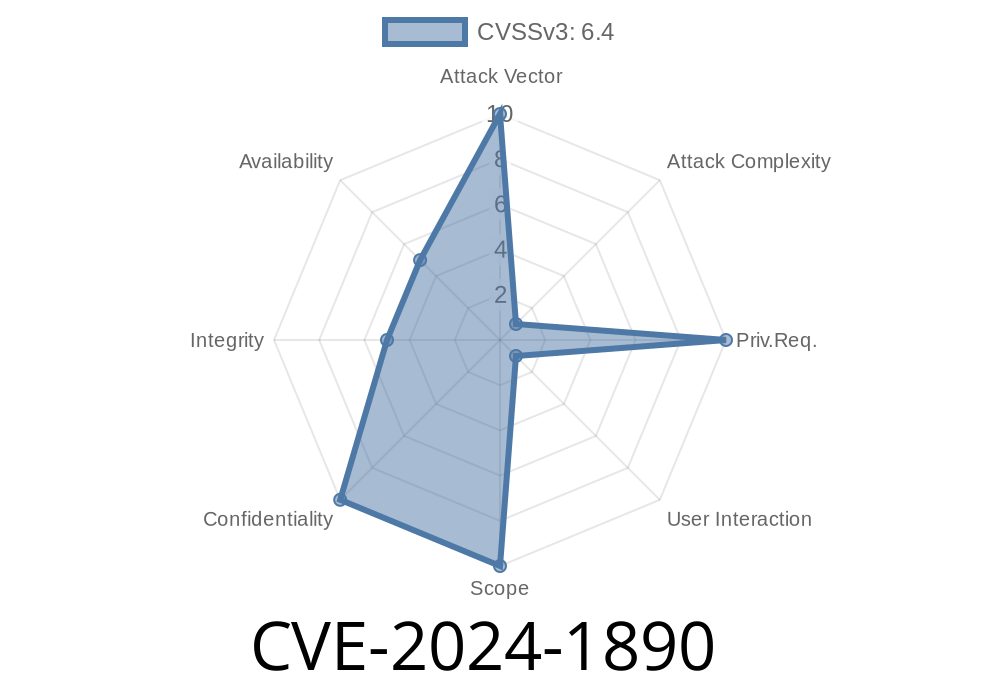
A newly discovered vulnerability, identified as CVE-2024-1890, allows remote attackers to perform clickjacking attacks on Sunny WebBox firmware version 1.6.1 and earlier. A vulnerable operator who clicks on a malicious link sent by an attacker would unknowingly grant remote access to their device, allowing an attacker to take unauthorized actions on the victim's behalf.
CVE Details
- CVE-2024-1890: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-1890
Exploit Details
The vulnerability is exploited through a method known as clickjacking, which is a type of user interface redressing attack. In a clickjacking attack, the attacker overlays an invisible frame on top of the legitimate content. The victim, without realizing it, will then click on the malicious frame, resulting in unintended consequences, and in this case, potentially giving the attacker unauthorized access to the victim's Sunny WebBox device.
The attacker can exploit this vulnerability by creating a malicious website or HTML link and sending it to an authenticated operator of a vulnerable Sunny WebBox device. The following is an example of a simple HTML code snippet that an attacker can use to create the malicious link:
<!DOCTYPE html>
<html>
<head>
<style>
iframe {
position: absolute;
width: 100%;
height: 100%;
opacity: ;
z-index: 2;
}
</style>
</head>
<body>
<iframe src="http://[Sunny_WebBox_IP]/"></iframe>;
</body>
</html>
When the targeted operator clicks on this malicious link, they would unknowingly perform actions on their Sunny WebBox using the attacker's crafted URL, potentially leading to unauthorized changes and remote access to their Sunny WebBox device.
Mitigation
Sunny WebBox operators should update to the latest firmware version to address and prevent this vulnerability. It is also recommended to avoid clicking on suspicious or untrusted links and to install anti-clickjacking browser plugins, such as "NoScript" or "uMatrix."
Original References
1. CVE-2024-1890: https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-1890
2. Sunny WebBox Firmware: https://www.sma.de/en/products/monitoring-control/sunny-webbox.html
3. NoScript: https://noscript.net/
4. uMatrix: https://github.com/gorhill/uMatrix
_By staying vigilant and up-to-date on firmware versions for your connected devices, you can help ensure your network remains secure from this and similar vulnerabilities. Share this information with those who may be affected by the CVE-2024-1890 vulnerability and encourage them to take preventative measures._
Timeline
Published on: 02/26/2024 16:27:55 UTC
Last modified on: 02/26/2024 16:32:25 UTC