---
Introduction
In February 2024, Microsoft patched a critical Windows Kernel vulnerability identified as CVE-2024-21340. This security flaw is classified as an information disclosure vulnerability, meaning attackers could potentially access sensitive data hidden within the kernel's protected memory. Let’s break down what this means, how it works, how it can be exploited, and what you can do about it.
What is CVE-2024-21340?
CVE-2024-21340 resides in the Windows Kernel, the central core of the Windows Operating System. When exploited, it could expose parts of kernel memory to regular user-mode applications—bypassing the safety walls set up by Microsoft between your apps and the heart of Windows.
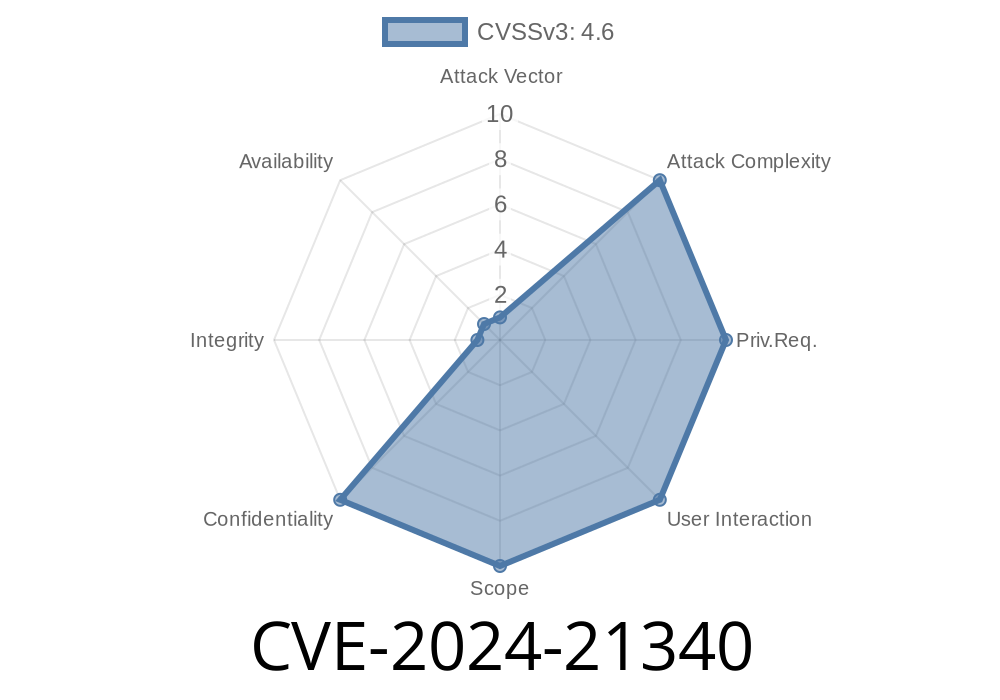
Severity: Important
- CVE Entry: NIST NVD Link
- Microsoft Advisory: Microsoft Security Update Guide
Root Cause
At the root, the bug exists because the Windows kernel fails to properly initialize certain memory buffers before exposing them to user-mode processes. If an attacker crafts a specific API call, the kernel could return pieces of memory containing sensitive information—a class of bug we commonly call "uninitialized memory disclosure."
How Could This Vulnerability Be Exploited?
An attacker needs to run code locally on a target computer. By repeatedly invoking the affected API, it's possible to harvest chunks of kernel memory. This type of exploit cannot be done remotely and, on its own, doesn't allow code execution—but it’s a valuable tool for attackers seeking to escalate privileges.
Code Snippet: Proof-of-Concept
Below is a simplified C code snippet mimicking a proof-of-concept that exploits buffer disclosure (note: actual implementation may require deeper Windows internals knowledge):
// Warning: For educational use! Do NOT use maliciously.
#include <windows.h>
#include <stdio.h>
int main() {
char buffer[1024] = {};
DWORD bytesReturned = ;
// Assume IOCTL xXXXX exposes kernel memory with uninitialized memory leak
HANDLE device = CreateFileW(L"\\\\.\\VulnerableDevice",
GENERIC_READ | GENERIC_WRITE,
, NULL, OPEN_EXISTING, , NULL);
if (device == INVALID_HANDLE_VALUE) {
printf("Failed to open device.\n");
return 1;
}
// Send IOCTL, receive uninitialized kernel memory in buffer
DeviceIoControl(device,
x9C402580, // Example control code
NULL, ,
buffer, sizeof(buffer),
&bytesReturned, NULL);
// Dump buffer to see what leaks
for (int i = ; i < bytesReturned; ++i)
printf("%02X ", (unsigned char)buffer[i]);
printf("\n");
CloseHandle(device);
return ;
}
Note: The device name and IOCTL code here are placeholders. Actual exploitation depends on the vulnerable code path, which is not public. This sketch illustrates the general infoleak pattern.
Could speed up local privilege escalation chains
- Leaked memory might contain sensitive information like passwords, security tokens, or kernel pointers
Patch Immediately: Microsoft fixed CVE-2024-21340 in their February 2024 Patch Tuesday cycle.
References
1. NIST NVD: https://nvd.nist.gov/vuln/detail/CVE-2024-21340
2. Microsoft Security Update: https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21340
3. Patch Analysis Blog: Sophos Labs - Patch Tuesday February 2024
Security Researcher Reports
- Google Project Zero: Kernel Infoleaks Blog
Conclusion
CVE-2024-21340 is a reminder that information leaks can severely weaken the foundation of operating system security. Attackers love finding these bugs because they often open the door to even more damaging attacks. Protect yourself and your organization by updating your systems as soon as possible—and keep an eye out for future kernel bugs.
Timeline
Published on: 02/13/2024 18:15:49 UTC
Last modified on: 02/20/2024 21:30:54 UTC