In February 2024, Microsoft disclosed several important security flaws, but among the most notable was CVE-2024-21375. This critical vulnerability affects the Microsoft WDAC (Windows Data Access Components) OLE DB provider for SQL Server. Attackers can exploit this bug for remote code execution (RCE)—essentially gaining control of a vulnerable system from a remote location. In this article, we'll dig into what CVE-2024-21375 is, how it works, and what you should do to stay protected.
What is CVE-2024-21375?
CVE-2024-21375 is a vulnerability in the OLE DB provider, a component used by applications to connect and interact with databases such as Microsoft SQL Server. The flaw specifically impacts the way the provider processes certain malicious SQL queries or data, potentially leading to an attacker executing their own code on the server.
💡 Technical Summary:
Exploit Type: Remote Code Execution
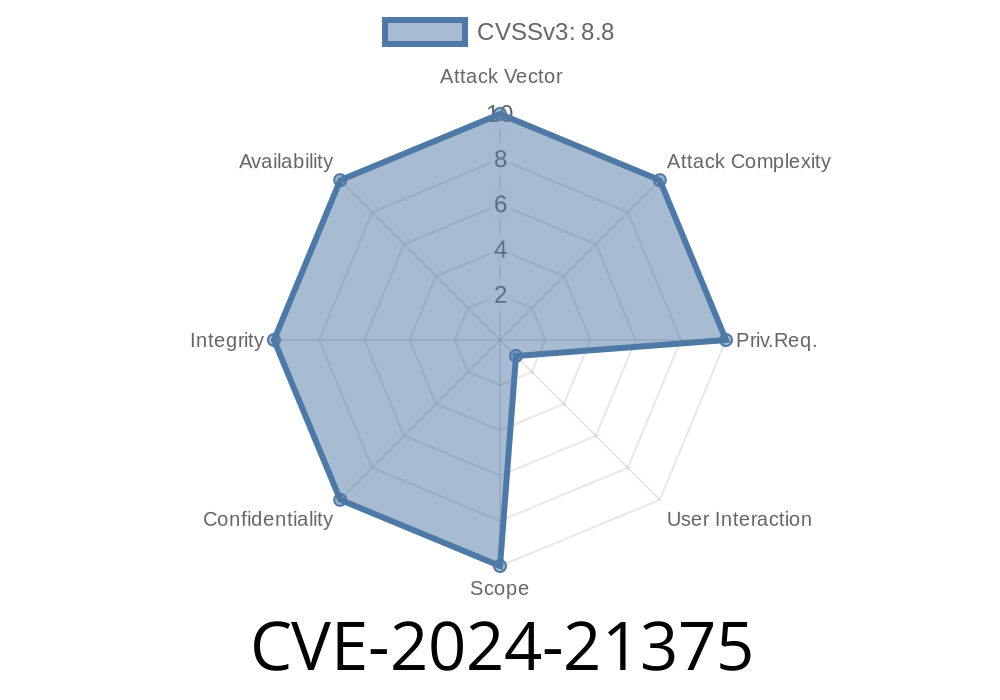
- CVSS Score: 8.8 (High/critical)
How Does the Exploit Work?
The vulnerability is based on how the OLE DB provider parses data or queries sent from clients. If a client sends a specially crafted SQL query or payload, the server can end up executing arbitrary code supplied by the attacker—sometimes with very high privileges.
An attacker sends a crafted SQL query, possibly embedding malicious code.
2. The provider does not properly validate or sanitize input, leading to memory corruption or code injection.
3. The attacker’s code is executed in the context of the affected process—typically with SYSTEM or administrative privileges.
Proof-of-Concept: Simple Exploit Flow
While Microsoft hasn’t released a public exploit, the attack surface is similar to past WDAC/SQL Server bugs. Here’s a high-level pseudocode showing how an exploit might work:
import pyodbc
# Replace with target server
server = 'victim.example.com'
database = 'testdb'
username = 'attacker'
password = 'password'
# Craft a malicious payload, e.g., triggering OLE DB vulnerability
malicious_payload = "SELECT * FROM users; -- OLEDB RCE payld"
# Connect using OLE DB provider
conn_str = (
"Provider=SQLOLEDB;"
f"Data Source={server};Initial Catalog={database};"
f"User ID={username};Password={password};"
)
try:
conn = pyodbc.connect(conn_str)
cursor = conn.cursor()
cursor.execute(malicious_payload)
print("[*] Payload executed")
except Exception as e:
print(f"[!] Exploit failed: {str(e)}")
Note: This is a simplified view; actual exploitation would require crafting a precise payload triggering the buggy code path in sqlsrv32.dll.
You are vulnerable if you
- Use Microsoft’s OLE DB provider for SQL Server (common in many ASP, legacy, or even modern .NET apps).
- Allow untrusted users or code to interact with your SQL Server or any connected applications that use OLE DB for data access.
Patching and Mitigating CVE-2024-21375
The best fix:
Apply the patches released by Microsoft in February 2024.
➡️ Microsoft Security Bulletin for CVE-2024-21375
References
- Microsoft’s official CVE-2024-21375 documentation
- Microsoft OLE DB Driver for SQL Server
- CVE Record on NIST NVD
Conclusion
The CVE-2024-21375 vulnerability is a powerful reminder that even trusted, “legacy” technologies like OLE DB can yield serious remote code execution bugs. Attackers move fast on security news—so make sure your systems are patched and follow the latest mitigation best practices.
If you’re using applications or servers that rely on the Microsoft WDAC OLE DB provider, update immediately and consider moving away from outdated data access layers whenever possible.
Timeline
Published on: 02/13/2024 18:15:55 UTC
Last modified on: 02/13/2024 18:22:53 UTC