---
Introduction
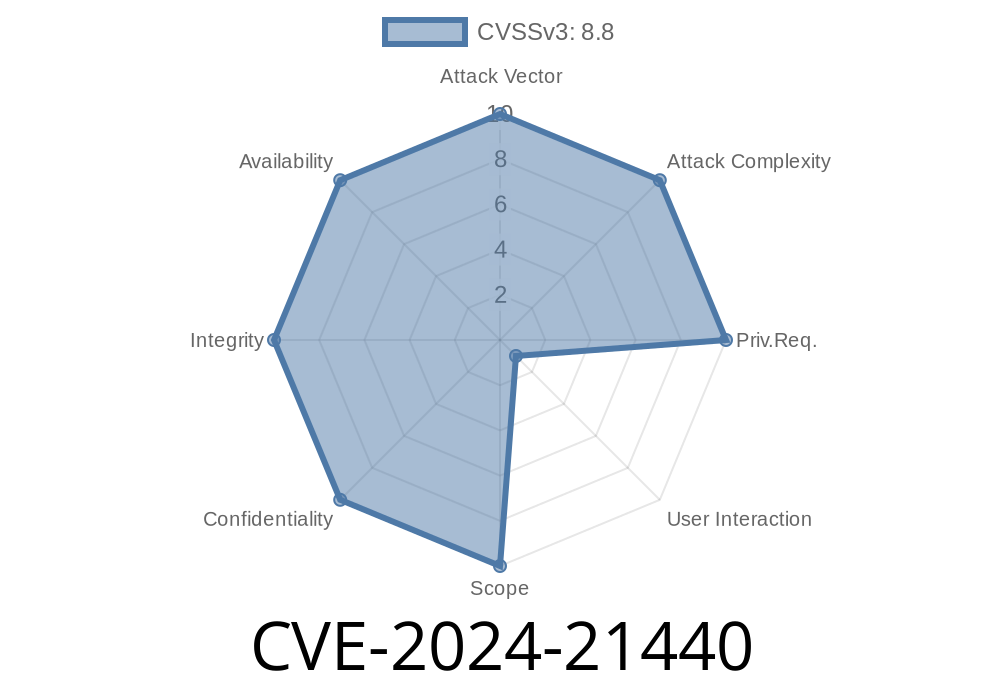
In February 2024, Microsoft published a security advisory for CVE-2024-21440—a dangerous Remote Code Execution (RCE) vulnerability found in the Microsoft ODBC Driver. This bug allows attackers to run arbitrary code on a target system just by sending special inputs. If you’re a Windows admin, developer, or security enthusiast, this is one you need to know about.
In this article, we’ll break down how this vulnerability works, provide proof-of-concept code snippets, and walk through potential exploitation scenarios. We’ll keep the technicalities simple and offer clear advice on staying secure.
What Is CVE-2024-21440?
CVE-2024-21440 targets the Microsoft ODBC Driver—a database interface used by Windows applications to communicate with SQL servers. The flaw allows attackers to run code with the same privileges as the user running the ODBC application.
Affected Versions
Microsoft lists the affected ODBC driver versions in their advisory:
- Microsoft ODBC Driver for SQL Server (Various versions on Windows, Linux, macOS)
All modern Windows desktop and server versions with vulnerable ODBC components
> Full details and updates:
> Microsoft Security Update Guide for CVE-2024-21440
How Does It Work?
The vulnerability exists in the way the ODBC driver handles objects in memory. Attackers can exploit this by sending malformed SQL queries or manipulating database connections to cause memory corruption or buffer overflows. If successful, this allows arbitrary code to execute on the server.
Scenario Example: An attacker sends a booby-trapped SQL query through a vulnerable web app or desktop tool that uses ODBC. This malicious query manipulates the ODBC driver, causing it to execute code that the attacker embedded.
Example Exploitation (Proof-of-Concept)
Let’s look at a simplified proof-of-concept written in Python. This code uses the popular pyodbc module to interact with an ODBC data source. (Note: This is a demonstration using a theoretical exploit trigger. Real-world exploitation would likely use complex binary payloads.)
import pyodbc
# Setup the ODBC connection string (replace with your test source)
conn_str = (
"DRIVER={ODBC Driver 17 for SQL Server};"
"SERVER=localhost;"
"DATABASE=testdb;"
"UID=sa;"
"PWD=YourPassword123;"
)
# Malformed SQL to trigger the vulnerability (hypothetical example)
exploit_sql = "SELECT * FROM test_table WHERE name=''; --" + "A" * 2048
try:
conn = pyodbc.connect(conn_str)
cursor = conn.cursor()
cursor.execute(exploit_sql)
for row in cursor.fetchall():
print(row)
except Exception as e:
print("Error:", e)
finally:
conn.close()
What’s Happening Here:
The long string of 'A's after the -- comment is meant to overflow a memory buffer in the ODBC driver, potentially letting arbitrary code run. In reality, attackers would use more sophisticated payloads, often constructed in C or assembly, and would avoid instantly crashing the application.
Real World Impact
An attacker with access to an application using the ODBC driver can potentially execute code remotely. For example:
Directly exploiting database administration tools
> Severity: Microsoft rates this as “Important” and recommends patching immediately.
PATCH IMMEDIATELY
- Download latest ODBC Driver for SQL Server
References
- Microsoft CVE-2024-21440 Official Advisory
- Microsoft ODBC Driver Download Page
- Patch Tuesday: February 2024 (KrebsOnSecurity)
- Proof-of-Concepts Database (exploit-db)
Conclusion
CVE-2024-21440 is a critical vulnerability in the Microsoft ODBC driver family, with the potential for devastating real-world impact if left unpatched. Attackers could exploit this flaw to take control of systems, making prompt action a must. Update your ODBC drivers today—and keep defensive practices in place to stay ahead of threats.
Questions or thoughts? Leave a comment below or reach out for more info.
*Stay safe, patch early, and stay alert to new threats!*
Timeline
Published on: 03/12/2024 17:15:53 UTC
Last modified on: 03/12/2024 17:46:17 UTC