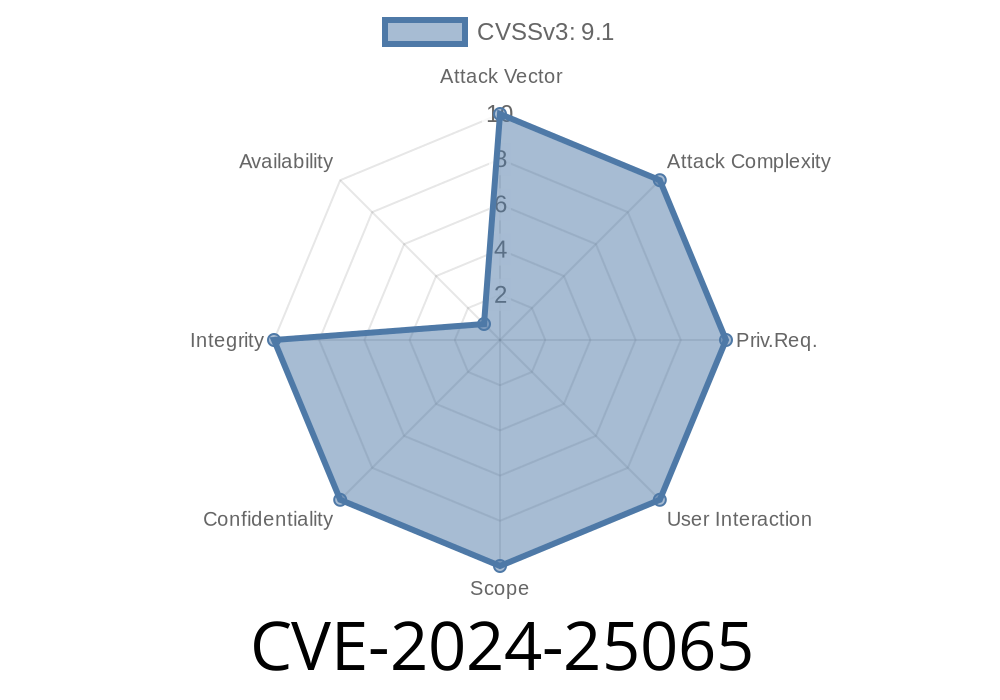
A new security flaw has been found in Apache OFBiz, an open-source enterprise automation platform. Labeled CVE-2024-25065, this critical vulnerability lets attackers perform path traversal attacks, granting them unauthorized access and allowing possible authentication bypass.
Put simply: if you're running an older version of OFBiz, hackers might sneak into your system without proper login details by exploiting a loophole in the way OFBiz manages file paths.
What is Path Traversal?
Path traversal is when someone tricks a program into letting them access files and folders they shouldn't. For example, instead of just opening user.txt, a hacker could request ../../etc/passwd to try to break out of the intended folder and access the whole system.
In web applications, improper handling of URLs or file paths in code could allow someone to "walk up" the directory tree and access sensitive files—or, in this case, bypass authentication.
Risk:
- Attackers can craft malicious URLs to bypass authentication systems and possibly gain admin access without the right password.
Exploit Details (How Attackers Abuse It)
This bug happens because OFBiz didn't properly validate file paths or requests in some endpoints. An attacker could send a specially crafted HTTP request using path traversal characters like ../ to reach outside the expected directories—skipping security checks.
Suppose your OFBiz runs on https://your-ofbiz-server/. An attacker might use
GET /webtools/control/../../..//webtools/control/login HTTP/1.1
Host: your-ofbiz-server
- The ../../..// sequence tells OFBiz to climb up directories and reload the login endpoint.
- Repeating these sequences at the right endpoint can trick OFBiz into serving restricted pages, skip authentication, or leak sensitive information.
Pseudo-Code Snippet Demonstrating Bad Path Handling
// Vulnerable code (simplified)
String resourcePath = request.getParameter("path");
File resource = new File(baseDir, resourcePath);
if (resource.exists()) {
// Serve the file or process the request
}
// No sanitization of 'resourcePath' allows directory traversal!
What’s wrong?
If resourcePath is ../../etc/passwd, the program opens a system file instead of a restricted one.
Authentication Bypass: Attackers can get in *without* correct credentials.
- Potential System Control: If exploited further, they could access sensitive files or administer your system.
- Data Theft/Corruption: Unauthorized data access and manipulation.
Upgrade to OFBiz version 18.12.12 or later, which includes a patch for this problem!
Developers:
Always sanitize any user-supplied input before using it in file paths. Prevent use of ../ or absolute paths.
Secure Java Example
// Secure way
Path basePath = Paths.get(baseDir).toRealPath();
Path requestedPath = basePath.resolve(resourcePath).normalize();
if (!requestedPath.startsWith(basePath)) {
throw new SecurityException("Path Traversal detected!");
}
if (Files.exists(requestedPath)) {
// Serve file
}
References
- Apache OFBiz Security Page (CVE List)
- CVE-2024-25065 in NVD
- OFBiz 18.12.12 Release Notes
- Path Traversal Attack Explanation (OWASP)
Conclusion
CVE-2024-25065 is easy for attackers to abuse and gives access to anyone smart enough to craft the right URL.
If you manage Apache OFBiz, do NOT delay—patch as soon as possible.
Want help upgrading? The official OFBiz documentation and user forums are the best places to start.
Timeline
Published on: 02/29/2024 01:44:14 UTC
Last modified on: 08/29/2024 20:36:15 UTC