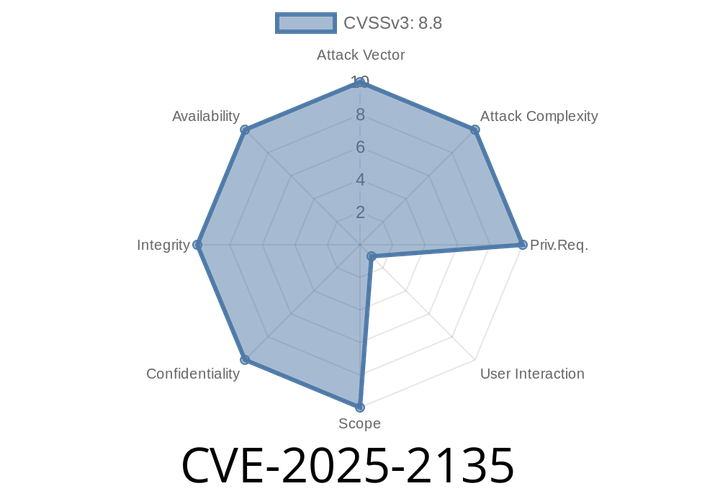
CVE-2025-2135 - Type Confusion in Chrome V8 – Heap Corruption Risk Explained (with Code & Exploit Details)
In March 2025, Google announced CVE-2025-2135, a high-severity security flaw in the V8 JavaScript engine—used in Google Chrome and other Chromium-based browsers. If you
CVE-2025-2136 - Chrome’s Inspector "Use-After-Free" Flaw Explained + Exploit Example
Earlier this year, researchers and Google’s own Security team uncovered a security vulnerability impacting Google Chrome’s Inspector feature. This flaw, tracked as CVE-2025-2136,
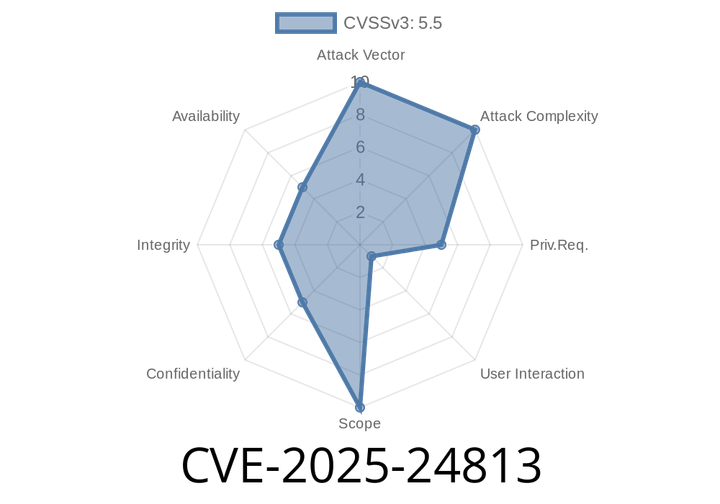
CVE-2025-24813 - Exploiting Path Equivalence and Internal Dots in Apache Tomcat – Remote Code Execution & Sensitive File Disclosure
Apache Tomcat is one of the most popular web servers used around the world, powering everything from development servers to large-scale production services. In February
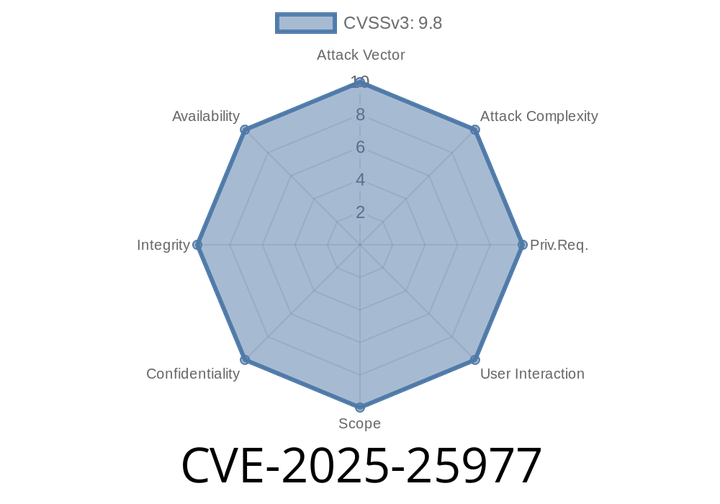
CVE-2025-25977 - Remote Code Execution in canvg v4..2 via StyleElement Constructor
A new critical security flaw, CVE-2025-25977, has been discovered in canvg, a popular JavaScript library for rendering SVGs on Canvas. This vulnerability affects version v4.
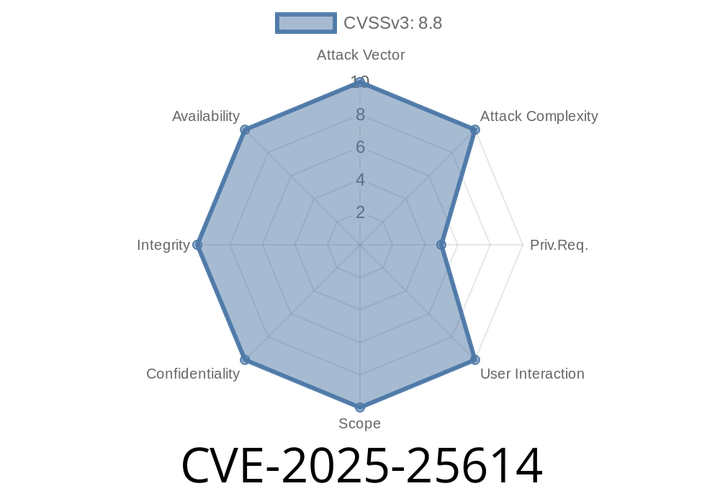
CVE-2025-25614 - Privilege Escalation in Unifiedtransform 2. via Incorrect Access Control
Unifiedtransform is a popular open-source school management and examination platform, used by educational institutions worldwide. But in early 2025, a security issue—now indexed as
Episode
00:00:00
00:00:00