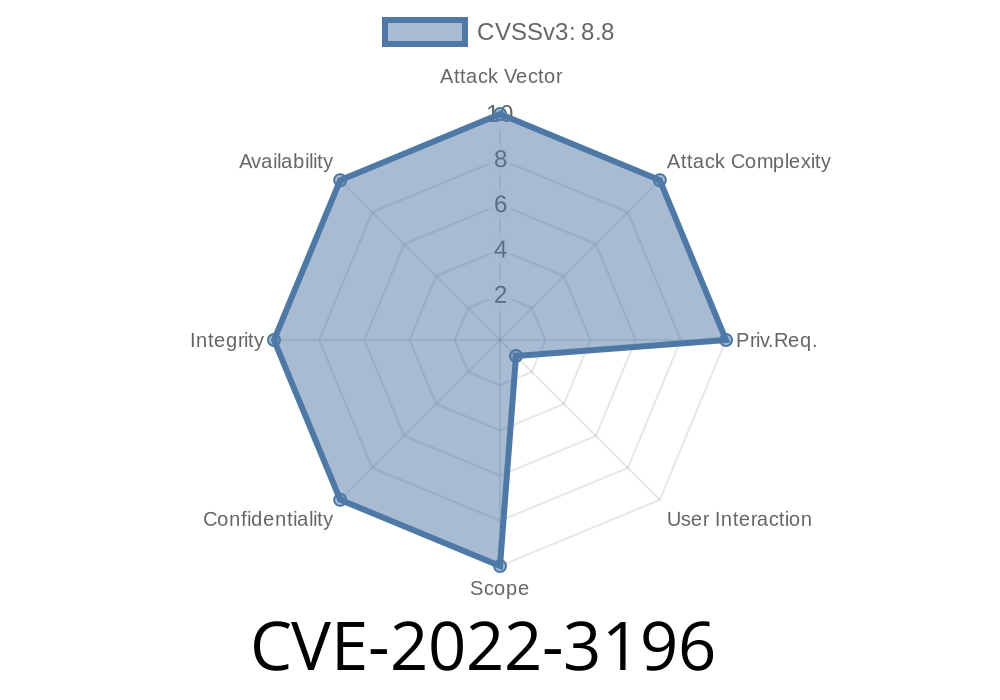
CVE-2022-3196 An after free vulnerability in Google Chrome could be exploited to cause heap corruption.
CVE-2018-6050 was assigned this issue. As of writing this advisory, it is still unclear whether this issue can be exploited to achieve remote code execution.
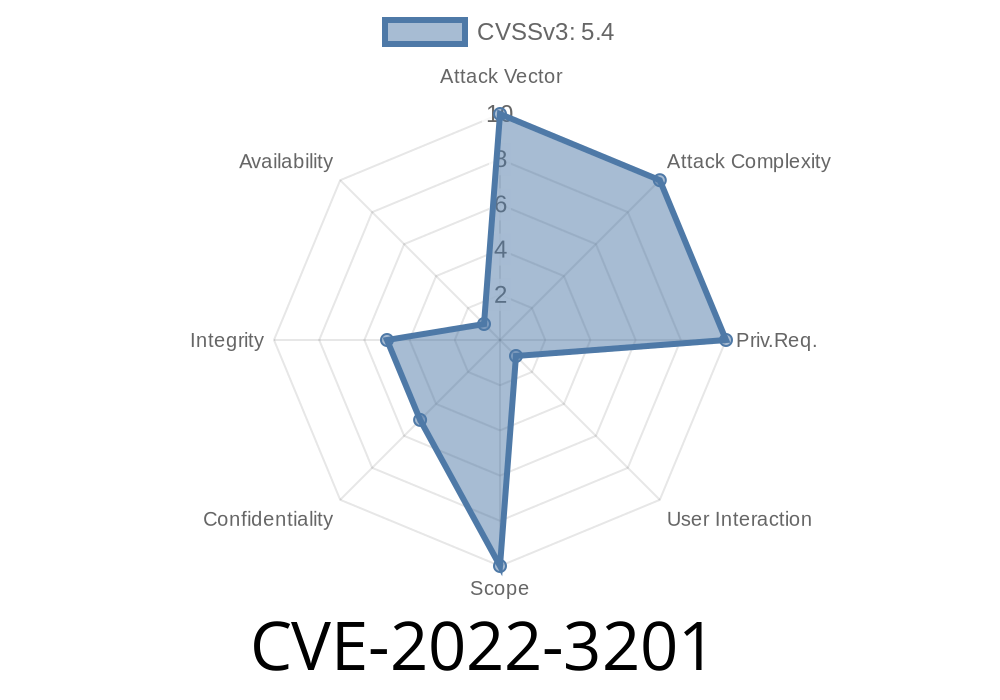
CVE-2022-3201 In past DevTools, an attacker could convince a user to install a malicious extension, which could bypass navigation restrictions.
This issue was addressed by disabling installation of extensions from non-trusted sources such as the Chrome Web Store. We also enabled a warning message when
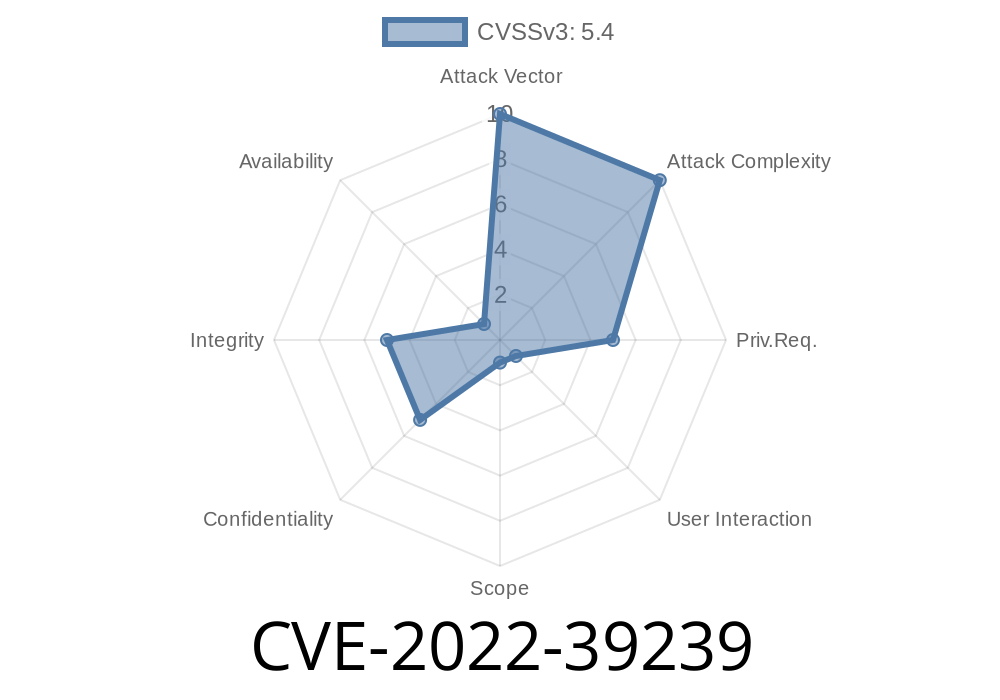
CVE-2022-39239 On-Demand image optimization for Netlify using ipx. Versions prior to 1.2.3 are vulnerable to brute force attacks that can bypass the source image domain allowlist.
If you are using custom domain mapping or a wildcard mapping, it may be necessary to clear the cache manually by regenerating the mapped subdirectory.
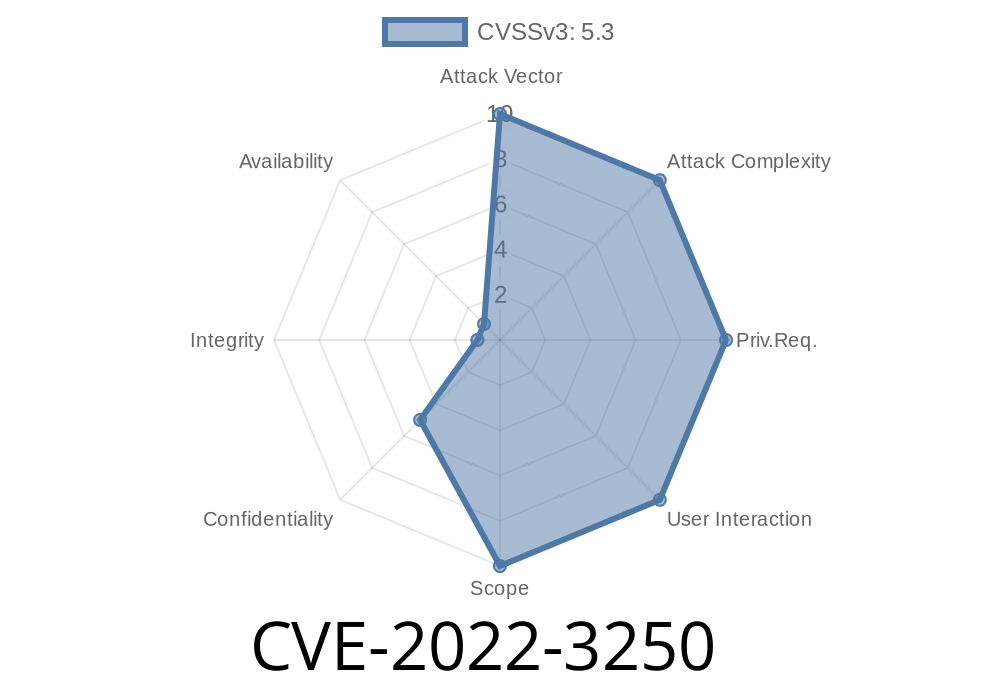
CVE-2022-3250 An insecure cookie was placed in a HTTPS session by a GitHub repository before 2.4.6.
If a browser requests a file over HTTP instead of HTTPS, it will show a lock symbol in the URL bar. Modern browsers come with
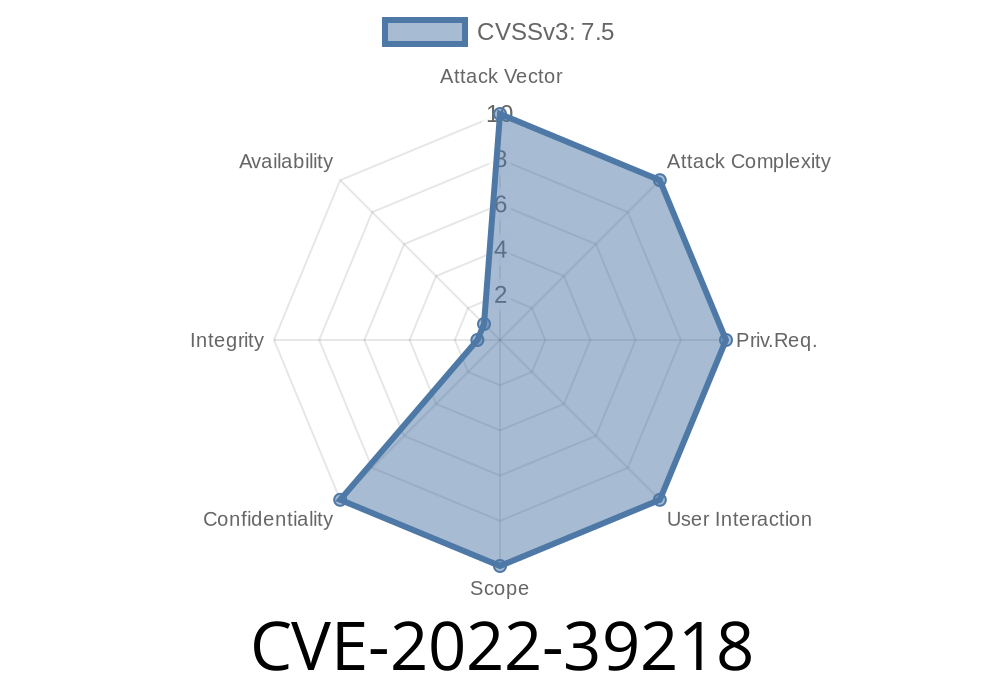
CVE-2022-39218 The JS Compute Runtime for Compute@Edge is the environment JavaScript is executed in when using the Compute@Edge JavaScript SDK.
When using the `crypto.getRandomValues` method on a `Compute@Edge` instance, a small bug in the JS Compute Runtime that was previously unpatched allows the
Episode
00:00:00
00:00:00