CVE-2022-30637 - How an Out-of-Bounds Write in Adobe Illustrator Could Let Hackers Take Over Your Computer
Adobe Illustrator is one of the most popular graphics editing programs on the market, used by creatives and professionals around the world. But even the
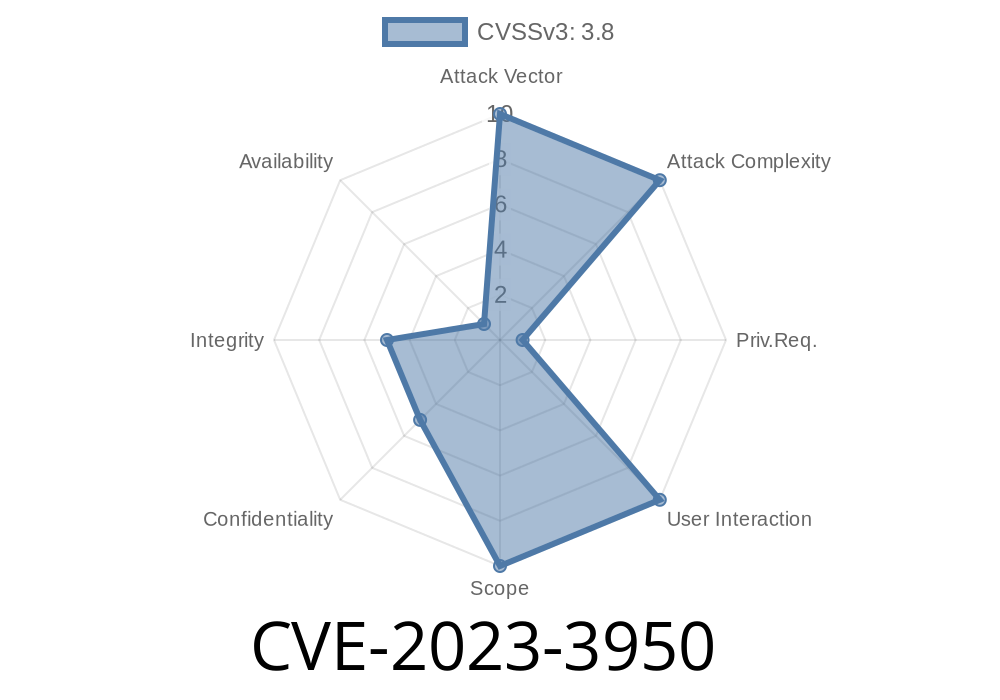
CVE-2023-3950 - Information Disclosure Vulnerability in GitLab EE: Public Key Exposure for Google Cloud Logging Audit Event Streaming Destination.
A security vulnerability, identified as CVE-2023-3950, has been discovered in GitLab Enterprise Edition (EE). The vulnerability exposes an information disclosure issue, allowing unauthorized users to
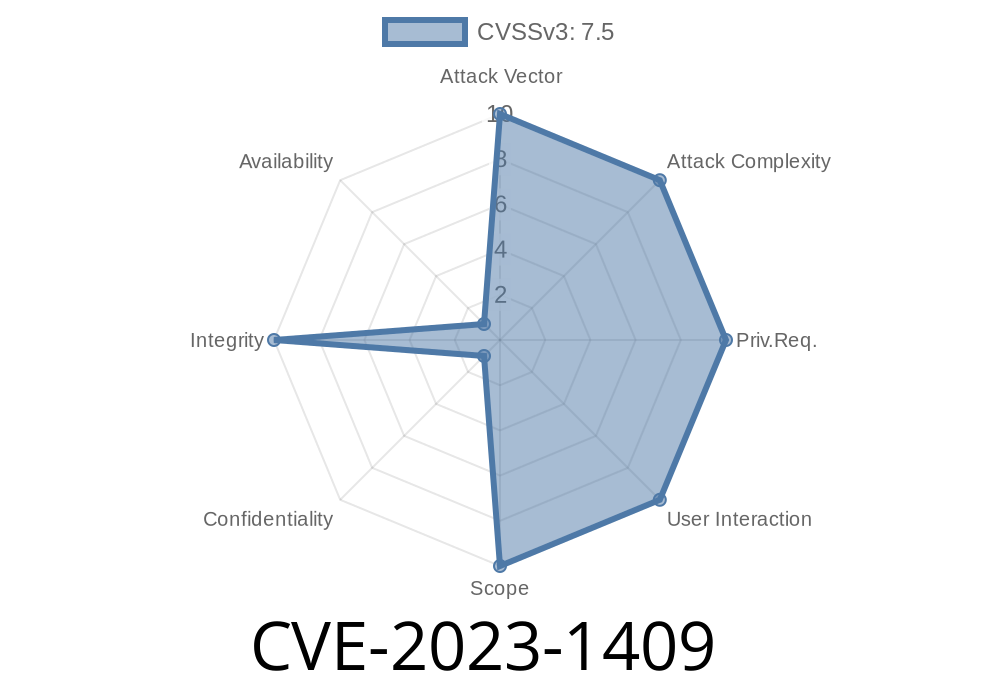
CVE-2023-1409 - How Misconfigured TLS Lets Attackers Bypass MongoDB Client Certificate Validation on Windows & macOS
In March 2023, the MongoDB team discovered a dangerous vulnerability with heavy implications for anyone running MongoDB Server on Windows or macOS using TLS. This
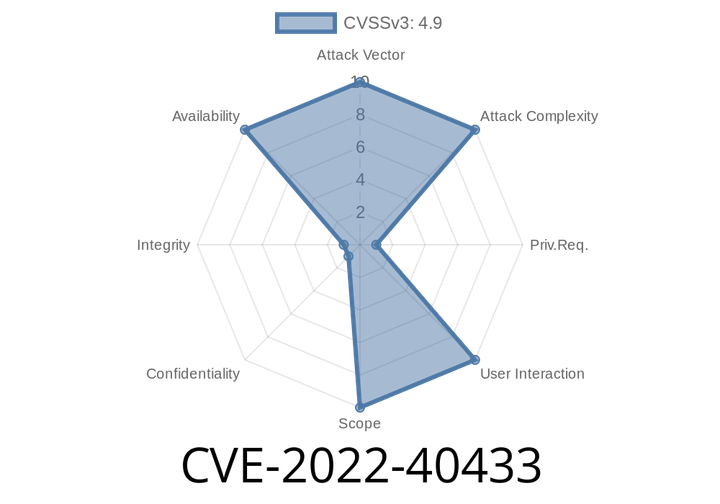
CVE-2022-40433 - Denial of Service in HotSpot JVM’s ciMethodBlocks::make_block_at Function — Exploit Details and Simple Breakdown
Java is everywhere, running millions of apps and systems. The Java Virtual Machine (JVM) is what makes Java code run, and Oracle’s HotSpot is
CVE-2023-40267 - How An Incomplete Fix in GitPython Opened the Door for Command Injection (with Demo)
Git is everywhere—from open-source projects to enterprise releases. So, libraries like GitPython make working with Git nicer in Python programs. But sometimes, a small
Episode
00:00:00
00:00:00