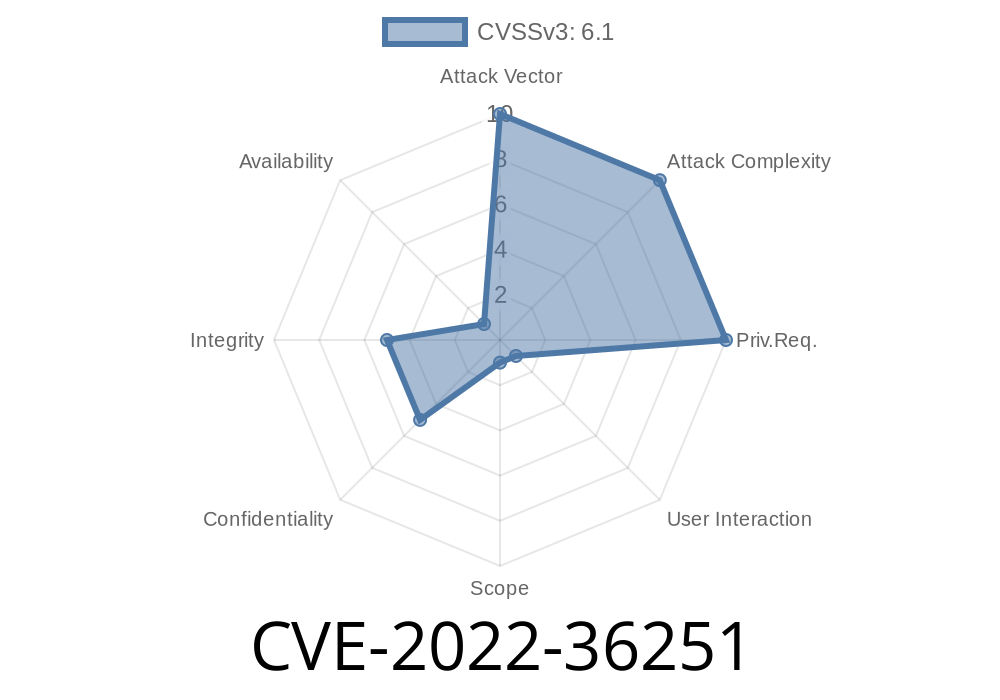
CVE-2022-36251 Clinic's Patient Management System v1.0 is vulnerable to Cross Site Scripting (XSS) via patients.php
A remote attacker can inject malicious code into the system via this vector. An attacker can create a patient record with a script that causes
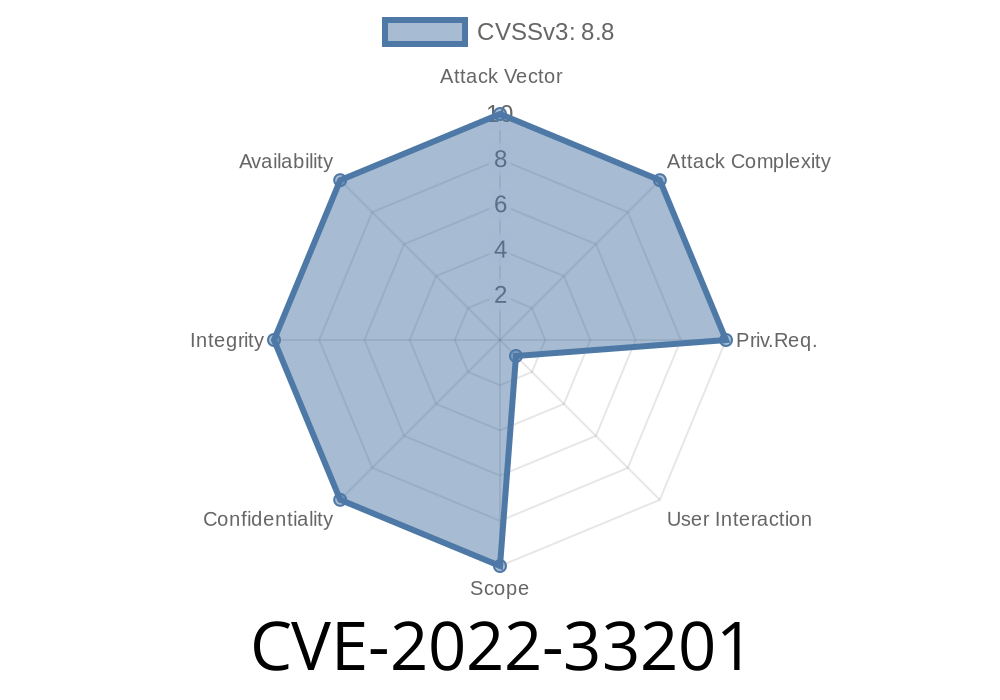
CVE-2022-33201 The MailerLite - Signup forms (official) plugin 1.5.7 has a CSRF vulnerability that allows an attacker to change the API key.
This issue happens when a user signs up for a MailerLite account through a WordPress site. During the registration process, an attacker can use a
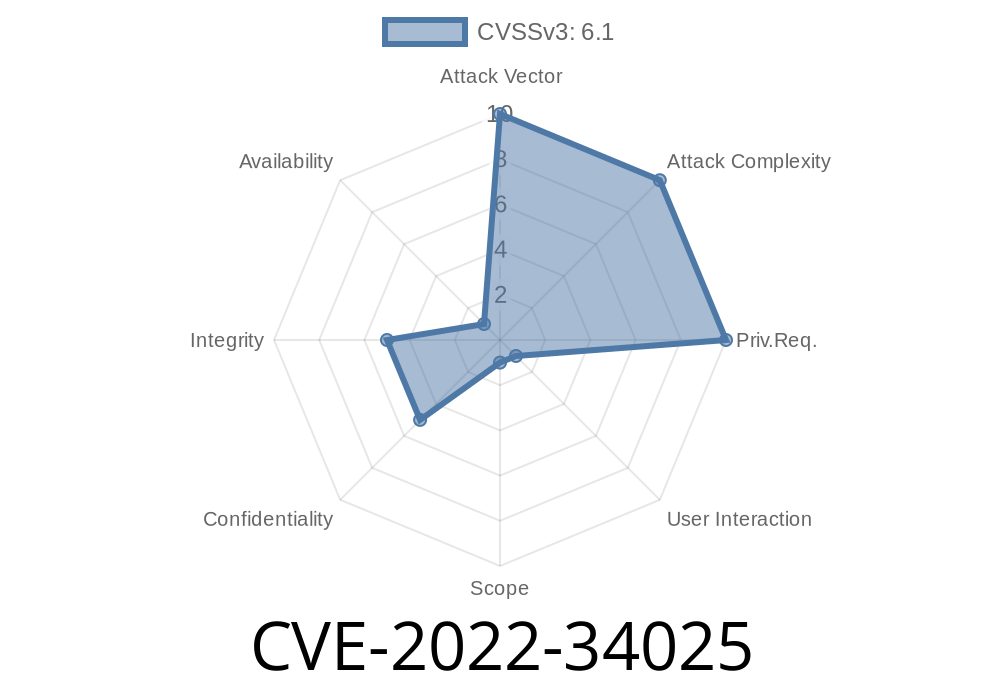
CVE-2022-34025 Vesta 1.0.0-5 had a XSS vulnerability via the post function at /web/api/v1/upload/UploadHandler.php.
An attacker can exploit this vulnerability by uploading malicious files to the target’s account. A successful exploit can result in session hijacking or information
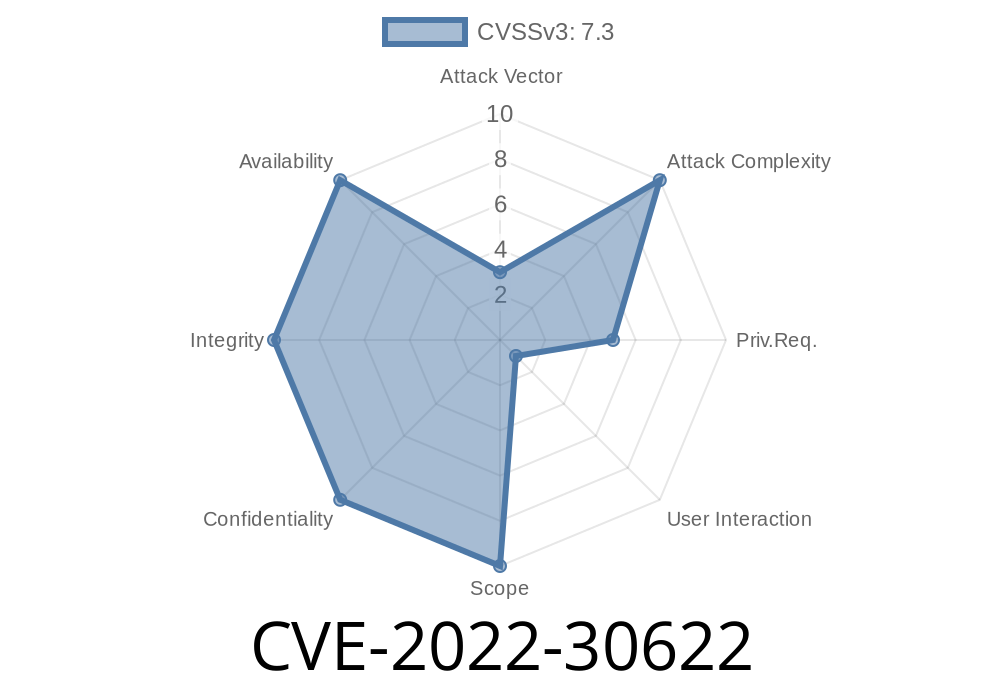
CVE-2022-30622 The system discloses usernames and passwords, which means it's possible to enter the system. The system loads the request clearly by default.
The server code is very vulnerable, as it is described in the following example. In addition, the server has hard-coded authentication credentials (admin/admin). Path
CVE-2022-1672 - Unpacking the CSRF Vulnerability in Google PageSpeed WordPress Plugin Before v4..7
If you use WordPress and rely on Google PageSpeed Insights Plugin to boost your site speed, you might have been at risk without even knowing
Episode
00:00:00
00:00:00