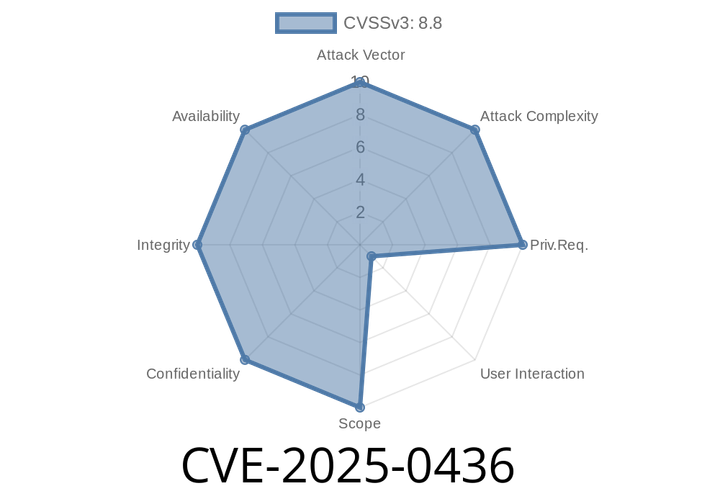
CVE-2025-0436 - Integer Overflow in Skia Graphics Engine Lets Hackers Exploit Chrome (Pre-132..6834.83)
TL;DR:
A newly disclosed bug—CVE-2025-0436—lets hackers remotely attack Google Chrome using a specially crafted web page. The culprit: an integer overflow in
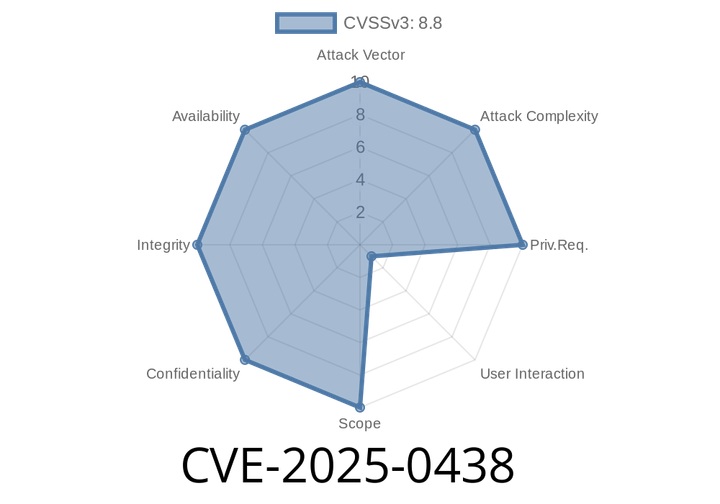
CVE-2025-0438 - Stack Buffer Overflow in Chrome Tracing – How Attackers Can Exploit It
Google Chrome is one of the most popular web browsers on the planet, and for good reason: it’s fast, reliable, and updated frequently to
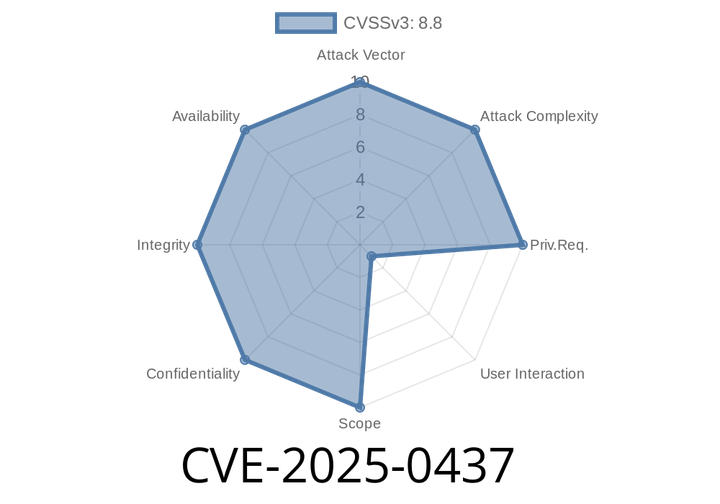
CVE-2025-0437 - Out-of-Bounds Read in Google Chrome's Metrics – Exploit and Deep Dive
In early 2025, researchers uncovered a serious security issue affecting Google Chrome prior to version 132..6834.83. Known as CVE-2025-0437, this vulnerability allows remote
CVE-2025-23013 - Local Privilege Escalation in Yubico pam-u2f (Authentication Bypass Exploit Guide)
Published: June 2024
Introduction
If you're using Yubico's pam-u2f for authentication on your Linux or Mac system, pay close attention: a
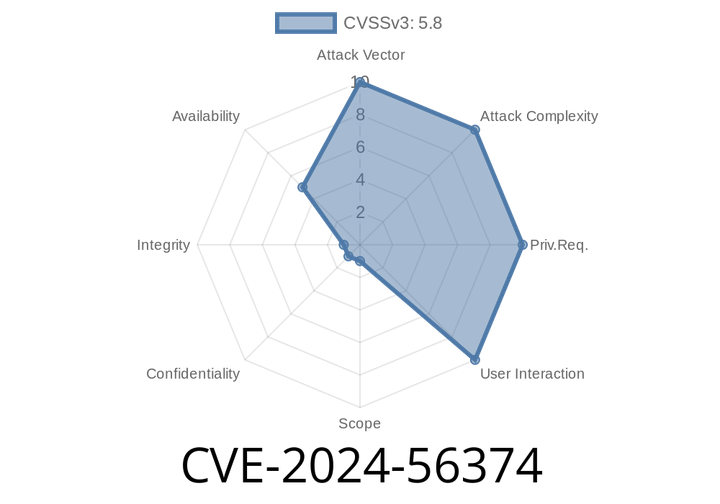
CVE-2024-56374 - Exploiting Django's IPv6 Validation for Denial-of-Service Attacks
Django is a super popular web framework for Python, powering countless websites and applications. But even the best tools can have bugs, and in early
Episode
00:00:00
00:00:00