CVE-2022-41100 - Exploiting Windows ALPC Elevation of Privilege Vulnerability (Deep Dive & PoC)
In the world of Windows security bugs, few things draw the attention of both attackers and defenders like elevation of privilege (EoP) vulnerabilities in core
CVE-2022-41104 - Microsoft Excel Security Feature Bypass Vulnerability Deep Dive
Microsoft Excel is one of the world’s most popular spreadsheet applications, used by private individuals, companies, and institutions alike to manage and analyze data.
CVE-2022-41091 - Breaking Down the Windows Mark of the Web (MotW) Security Bypass Vulnerability
---
Windows users and system administrators rely on built-in protections to help catch malicious files before they can run. One powerful security barrier is the
CVE-2022-41122 - Digging Into the Microsoft SharePoint Server Spoofing Vulnerability (With Exploit Details, Code & References)
---
If you manage Microsoft SharePoint servers, you can’t afford to ignore CVE-2022-41122. This vulnerability, disclosed and patched by Microsoft in November 2022, exposes
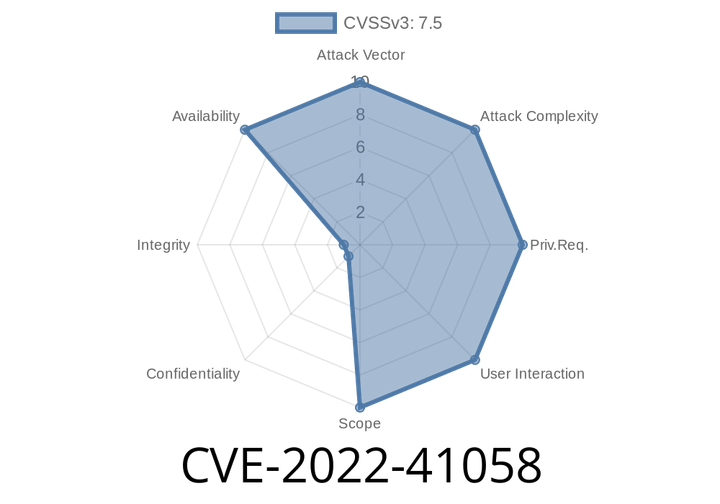
CVE-2022-41058 - Windows NAT Denial of Service Vulnerability - What You Need To Know
---
In this article, we’ll break down everything you need to know about CVE-2022-41058, a Windows Network Address Translation (NAT) vulnerability that could let
Episode
00:00:00
00:00:00