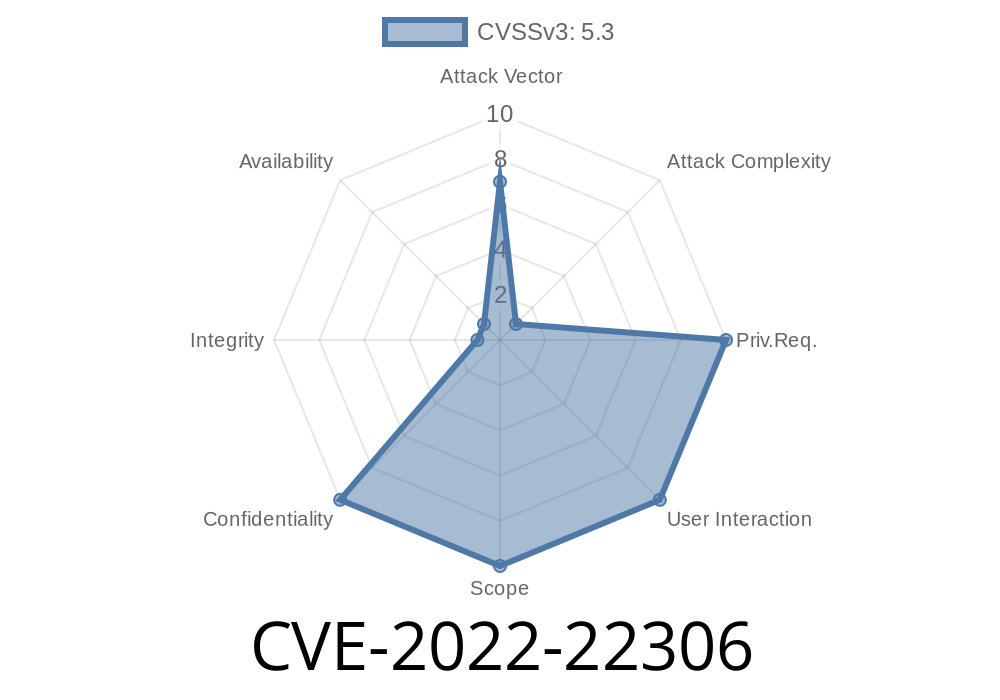
CVE-2022-22306 - How Improper Certificate Validation in FortiOS Opens the Door for Man-in-the-Middle Attacks
Fortinet's FortiOS is the backbone for many organizations' firewalls, VPNs, and cloud gateways. However, between specific versions (6.. up to 7..), a
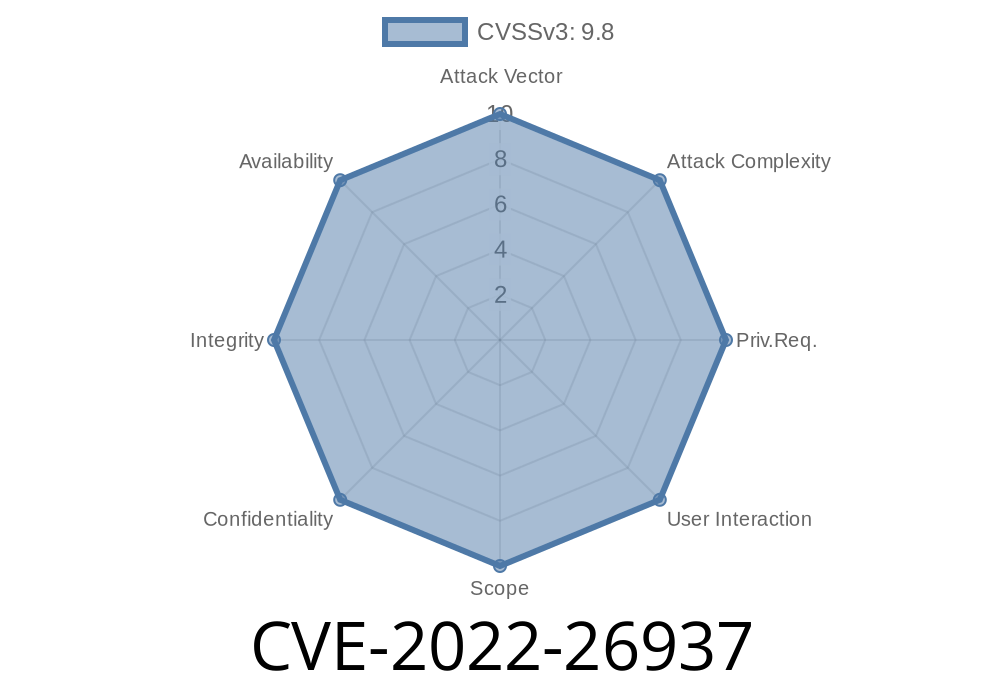
CVE-2022-26937 Windows Network File System Remote Code Execution Vulnerability.
This issue was discovered by NXP when they analyzed the firmware version on one of their products. They reported this issue to Juniper, who quickly
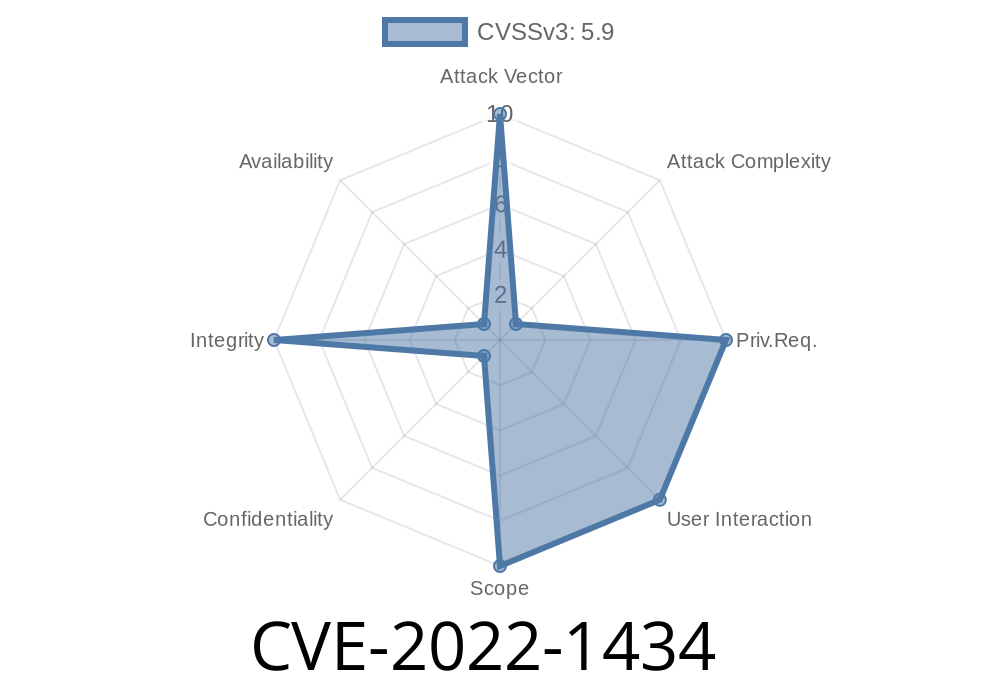
CVE-2022-1434 The OpenSSL 3.0 RC4-MD5 ciphersuite uses AAD as the MAC key, which is trivially predictable.
used. Due to the non-deterministic nature of IBM's implementation of the RC4-MD5 cipher, an attacker could potentially exploit this issue to generate traffic
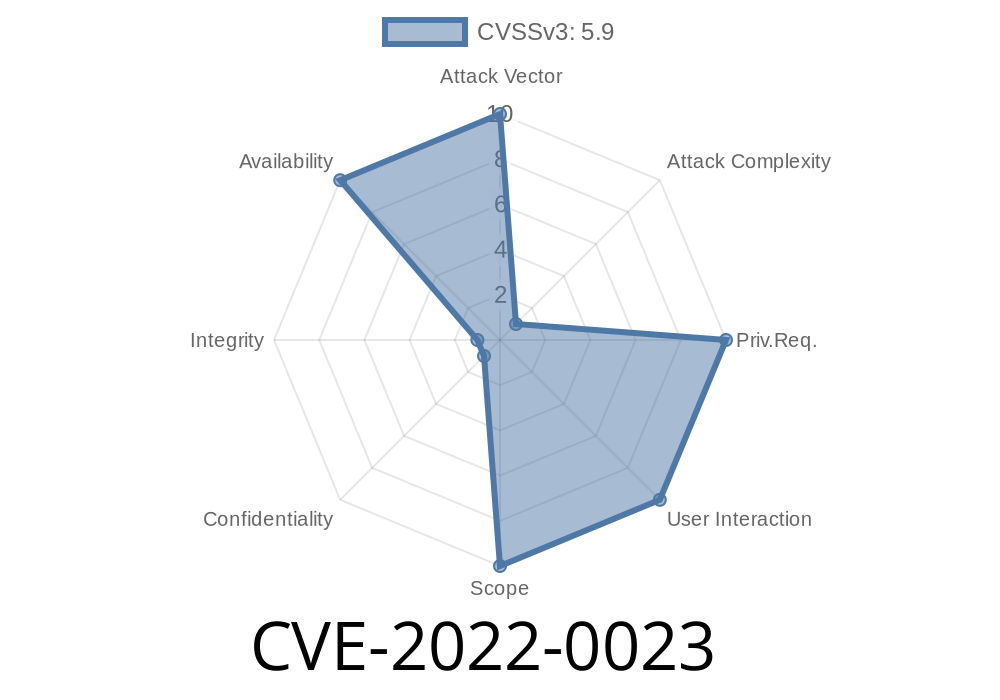
CVE-2022-0023 DNS proxy feature of PAN-OS can be exploited if the firewall is mishandled during an MITM attack.
The DNS proxy feature of PAN-OS is responsible for handling DNS requests forwarded to external DNS servers. A MITM can inject DNS records into the
CVE-2022-0759 - Critical Vulnerability in Ruby’s Kubeclient—What You Need to Know
Kubernetes has become the backbone for cloud-native workloads, and Ruby developers often turn to the kubeclient gem for interacting with Kubernetes APIs. But did you
Episode
00:00:00
00:00:00