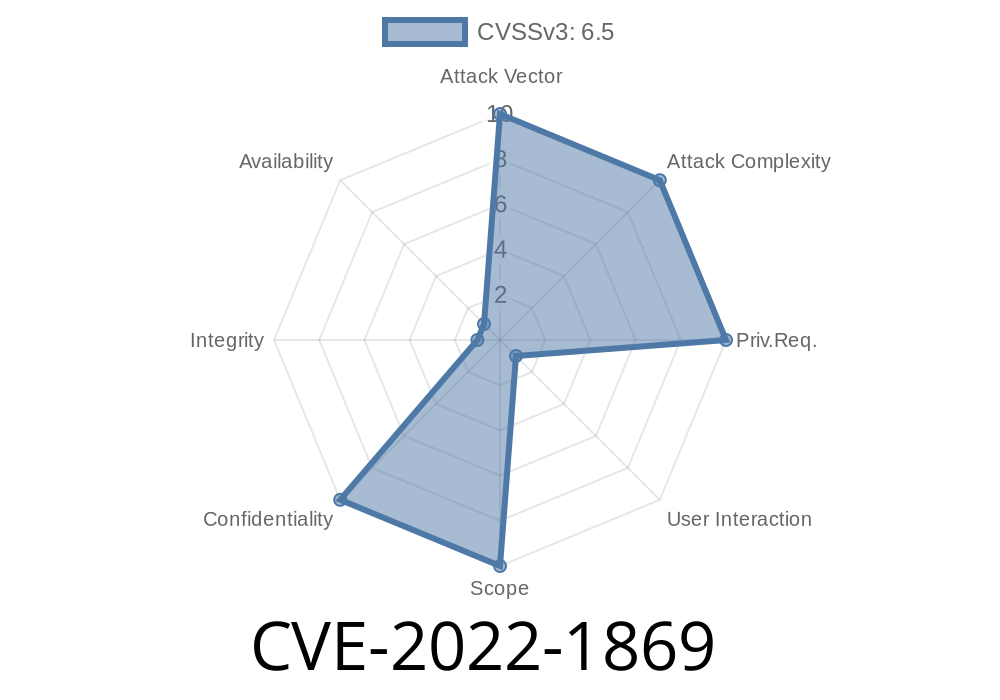
CVE-2022-1869 Confusion in V8 allowed a remote attacker to exploit heap corruption.
This issue did not affect most users, as the browser tried to prevent this by performing strict type enforcement. However, since the type system was
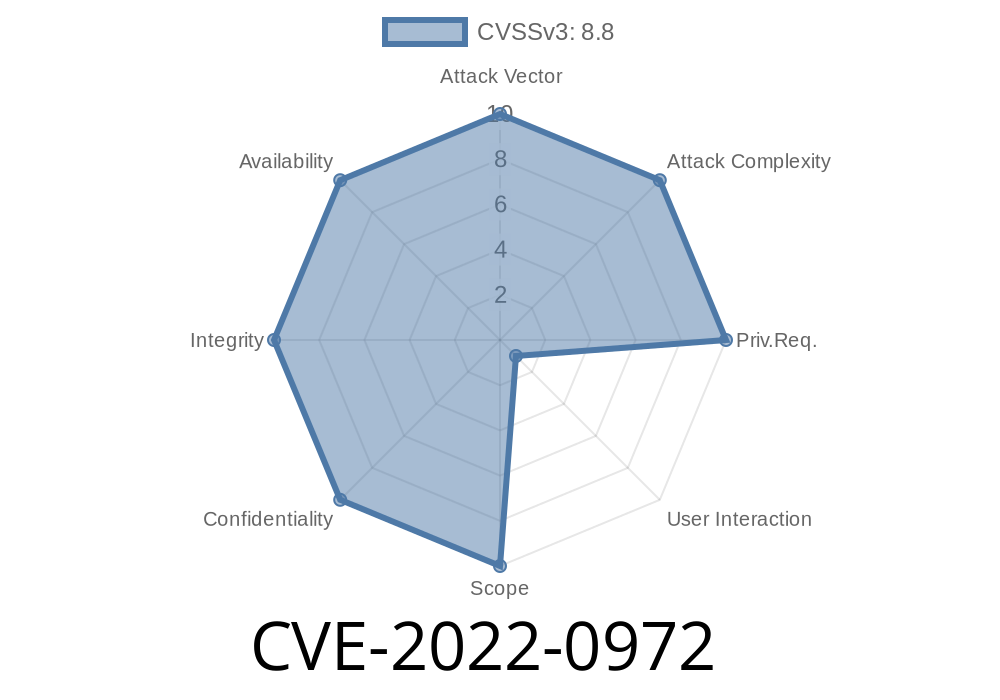
CVE-2022-0972 An attacker who convinces a user to install a malicious extension can exploit heap corruption in Chrome.
This issue was addressed by restricting the permissions of extensions installed through the Chrome Web Store. Red Hat Enterprise Linux 7 provides mitigations against a
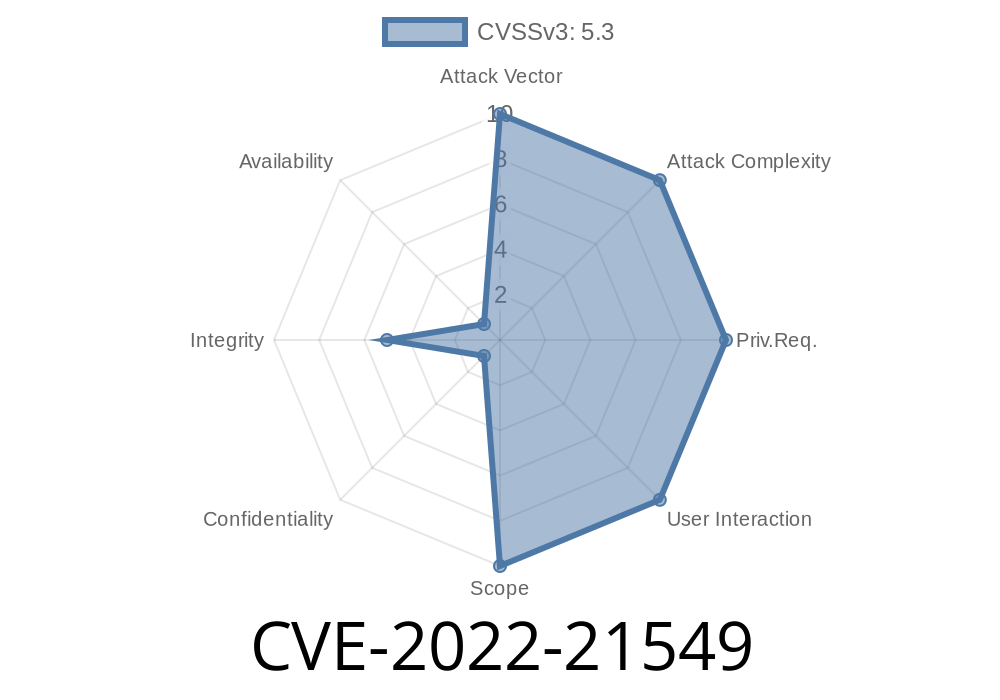
CVE-2022-21549 Oracle Java SE, Oracle GraalVM Enterprise Edition is affected by a vulnerability in the Libraries component. The vulnerability could allow a remote attacker to obtain system privileges.
by using the sendMessage API with a crafted object. The attacker cannot inject malicious code using the Java language, but can instead use scripting languages
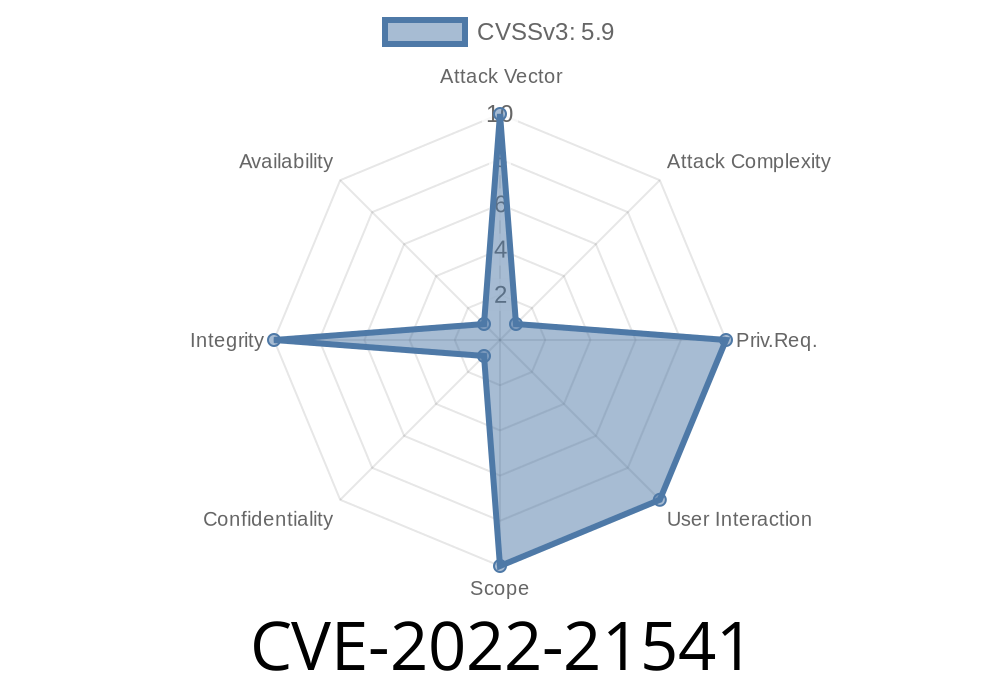
CVE-2022-21541 Oracle Java SE product has a vulnerability.
- The attacker must compromise the Java Security Manager to exploit this vulnerability. An attacker must have access to the network to compromise Oracle Java
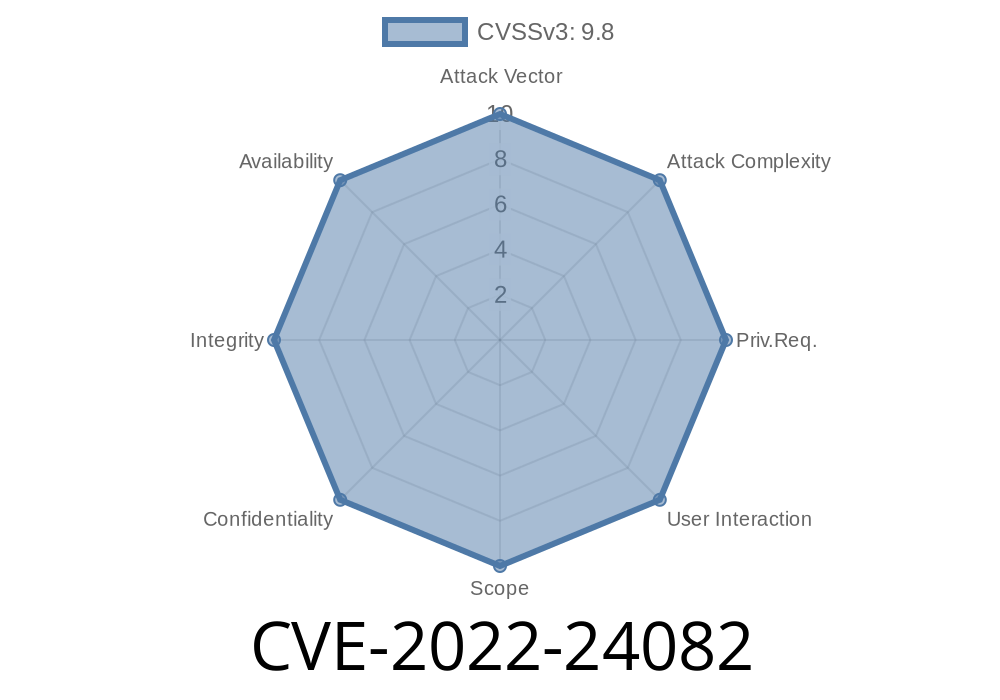
CVE-2022-24082 - Exploiting Pega Platform’s JMX Misconfiguration for Remote Code Execution
> Disclaimer: This article is for educational purposes only. Never attempt unauthorized access to computer systems.
Introduction
CVE-2022-24082 describes a critical vulnerability affecting on-premise installations
Episode
00:00:00
00:00:00